Today we’re thrilled to publicly announce Neighborhood Watch, our integrated Managed Threat Hunting program for industrial infrastructure organizations large and small. While the announcement is a milestone, we’ve been delivering and refining this offering for 2 years with customers across all of our core industries. Neighborhood Watch was created to address two critical, persistent struggles that industrial organizations face: limited, or no, ability to understand what’s in their operational technology (OT) networks – including hidden threats; and the scarcity of skilled cybersecurity professionals that also possess a deep appreciation for, and understanding, of ICS/OT environments and how they differ from IT.
Simply put, Neighborhood Watch brings the best people, processes, and technology available to bear to defend industrial infrastructure organizations against cyber threats.
Update: As of September 2021, Neighborhood Watch is now known as OT Watch
Back To Basics?
Data from recent SANS Institute studies on best practices in SOC operations and threat hunting point out some alarming statistics that are validated by our own first-hand findings, published in the Dragos 2019 Year In Review.
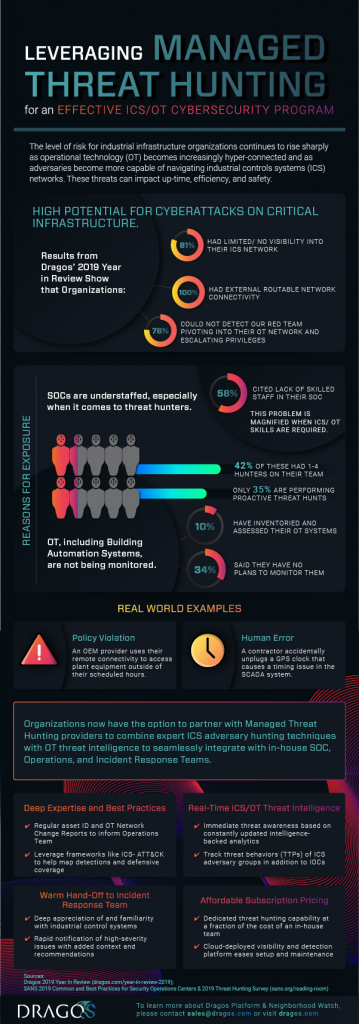
TL;DR: SOCs are understaffed, they aren’t monitoring OT networks, and they’re struggling so much reacting to alerts and IOCs that they have no time for proactive threat hunting which presents a huge risk.
Check out the infographic to the right to dig a little deeper into the numbers and also some first-hand accounts from the front lines.
These are unsettling facts, and beg the question – why? With dozens and dozens of managed services covering the IT side of things, and OT network monitoring and threat detection tools (including our own Dragos Platform), what’s the missing piece to solve this puzzle?
Generally speaking, technology alone isn’t enough to solve the problem of securing a plant’s people and processes from cyber threats. With sophisticated ICS-capable adversaries at your doorstep, or potentially already in your network, the missing piece is the right people with the necessary skills and experience.
Hunting For Hunters
If you’re struggling to find the right balance in your SOC, you’re not alone. The challenge to find and retain skilled cybersecurity staff was the #1 barrier to operational excellence in SOCs according to the SANS 2019 Common and Best Practices for Security Operations Centers survey. When you also factor in the need for highly specialized skills understanding and working with specialized industrial control systems, the problem is magnified tremendously.
With an already overworked staff, many have resorted to assigning the critically important job of threat hunting to analysts who are busy reacting to hundreds of alerts, pushing out patches, and keeping IT systems running on a daily basis. This leaves no time for true proactive threat hunting, which is vitally important in uncovering threats as early as possible in an attack. Threat hunters leverage tools, threat intel, and their experience to search for evidence of attacker behaviors on an ICS network – testing hypotheses on how an attack may happen and then proving or rejecting it based on their findings. As a best practice, they may also utilize a framework like MITRE’s ATT&CK for ICS to inform their hypotheses and then map gaps in a SOC’s ability to detect threats.
Enter Dragos Neighborhood Watch
With Neighborhood Watch, our team of expert analysts utilize the Dragos Platform on our customers’ behalf to deliver regular reports on OT assets and their behaviors and perform routine, proactive threat hunting. We’ve already been working with customers in industries like oil & gas, manufacturing, water treatment (Trinity River Authority of Texas), and the electric sector who didn’t have the staff or expertise they knew they needed in order to safeguard their people, operations, and surrounding communities.
They benefit from asset identification reports that provide an up-to-date understanding of changes made to key systems such as the controllers and their supervisory systems, and allow the security team to more effectively communicate to operations. This, in turn, allows the operations team to make better informed decisions for things like safety, root cause analysis, and understanding contractors/vendors and what they’re doing in their environments. Routine threat hunts by our expert analysts uncover threats and vulnerabilities along with recommendations to remediate them, in a language the operations team can understand and action while also bridging the divide with IT security teams. The end result is an overall improvement in defensive coverage and security posture, with continuous knowledge transfer from our team to theirs.

To learn more, we invite you to visit the Neighborhood Watch web page and view the recorded SANS/Dragos webinar Leveraging Managed Threat Hunting for an Effective ICS/OT Cybersecurity Program.
Ready to put your insights into action?
Take the next steps and contact our team today.