TALONITE
Since 2019
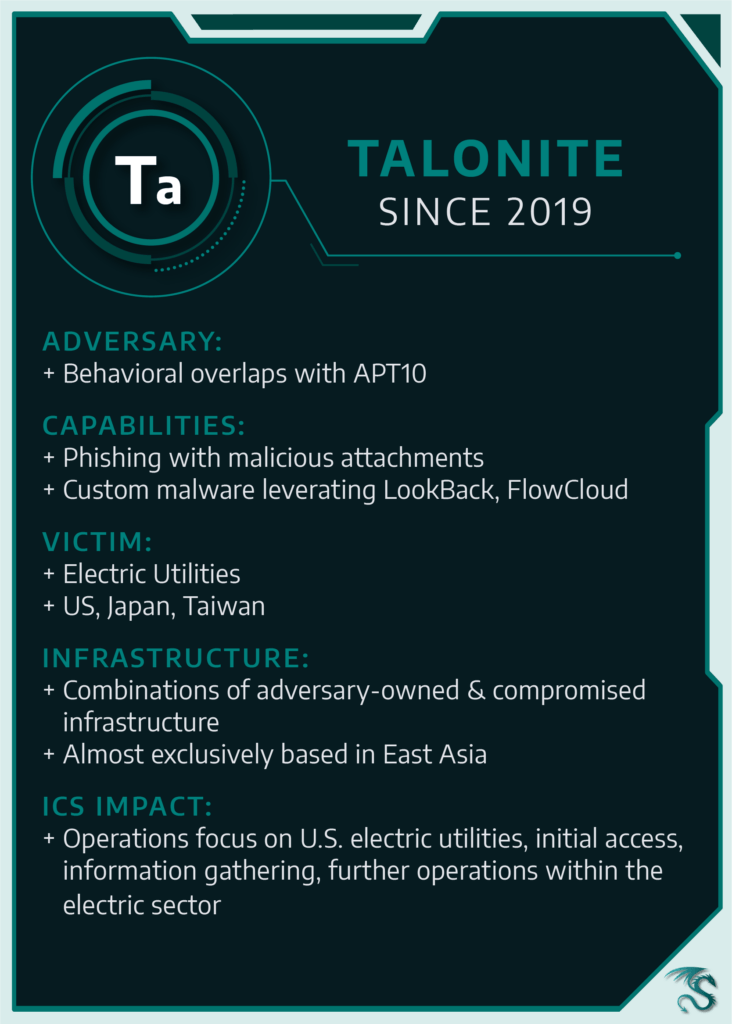
Dragos began tracking the TALONITE activity group in July 2019, with operations focusing on initial access compromises in the United States (U.S.) electric sector. The group uses phishing techniques with either malicious documents or executables. TALONITE uses two custom malware families that both feature multiple components known as LookBack and FlowCloud.*
TALONITE Threat Group Operations
TALONITE focuses on subverting and taking advantage of trust with phishing lures focusing on engineering-specific themes and concepts, malware using legitimate binaries maliciously or modifying such binaries to include additional functionality, and a combination of owned and compromised network infrastructure.
TALONITE activity is difficult to track and contain given the group’s propensity to blend techniques and tactics to ensure a successful intrusion. Although there is behavioral overlap between TALONITE and the Chinese state-sponsored group, APT10, Dragos cannot definitively link these two groups.
About Dragos Threat Intelligence
Dragos threat intelligence leverages the Dragos Platform, our threat operations center, and other sources to provide comprehensive insight into threats affecting industrial control security and safety worldwide. Dragos does not corroborate nor conduct political attribution to threat activity. Dragos instead focuses on threat behaviors and appropriate detection and response. Read more about Dragos’ approach to categorizing threat activity and attribution.
Dragos does not publicly describe ICS activity group technical details except in extraordinary circumstances in order to limit tradecraft proliferation. However, full details on TALONITE and other group tools, techniques, procedures, and infrastructure is available to network defenders via Dragos WorldView.
*LookBack Malware Targets the United States Utilities Sector with Phishing Attacks Impersonating Engineering Licensing Boards – proofpoint