KAMACITE
Since 2014
KAMACITE represents a long-running set of related behaviors targeting critical infrastructure and industrial verticals since at least 2014. KAMACITE facilitated ICS-specific operations including the BLACKENERGY2 campaign and the 2015 and 2016 Ukraine power events.
KAMACITE Threat Group Operations
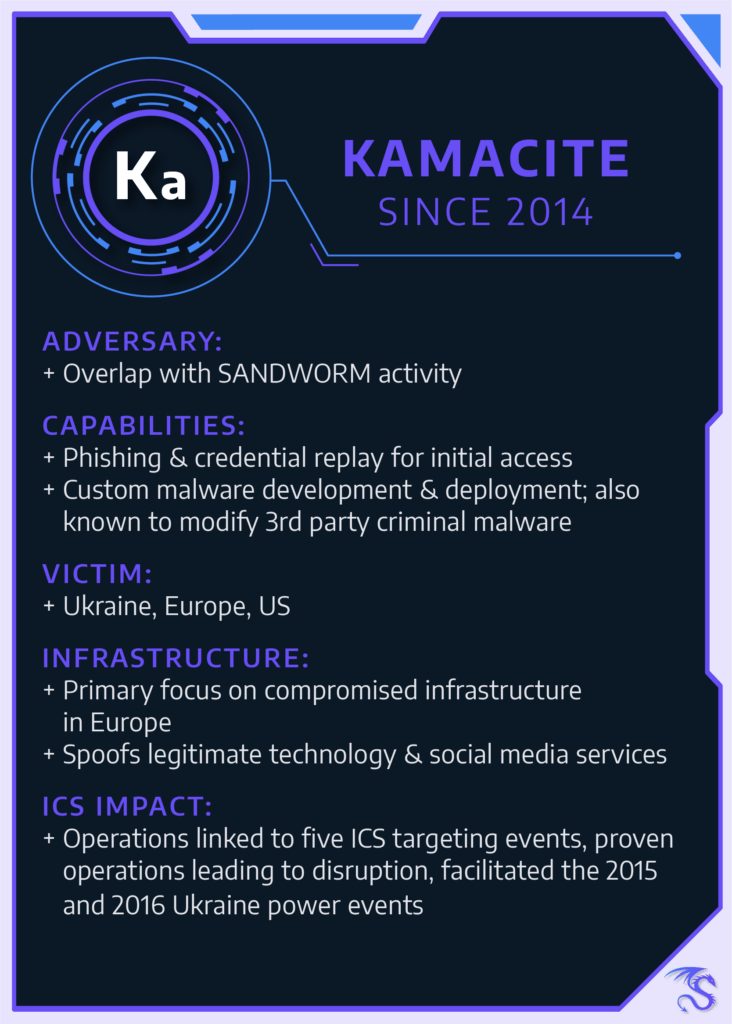
While the group has evolved over time, many aspects of its operations and tradecraft have remained remarkably similar over the past six years as of this writing. Although KAMACITE has not directly caused an ICS disruptive event according to Dragos analysis, the group is responsible for enabling other entities – such as ELECTRUM – to be in a position to deliver ICS-specific attacks.
About Dragos Threat Intelligence
Dragos threat intelligence leverages the Dragos Platform, our threat operations center, and other sources to provide comprehensive insight into threats affecting industrial control security and safety worldwide. Dragos does not corroborate nor conduct political attribution to threat activity. Dragos instead focuses on threat behaviors and appropriate detection and response. Read more about Dragos’ approach to categorizing threat activity and attribution.
Dragos does not publicly describe ICS activity group technical details except in extraordinary circumstances in order to limit tradecraft proliferation. However, full details on KAMACITE and other group tools, techniques, procedures, and infrastructure is available to network defenders via Dragos WorldView.