Infographic
Vulnerabilities Key Findings
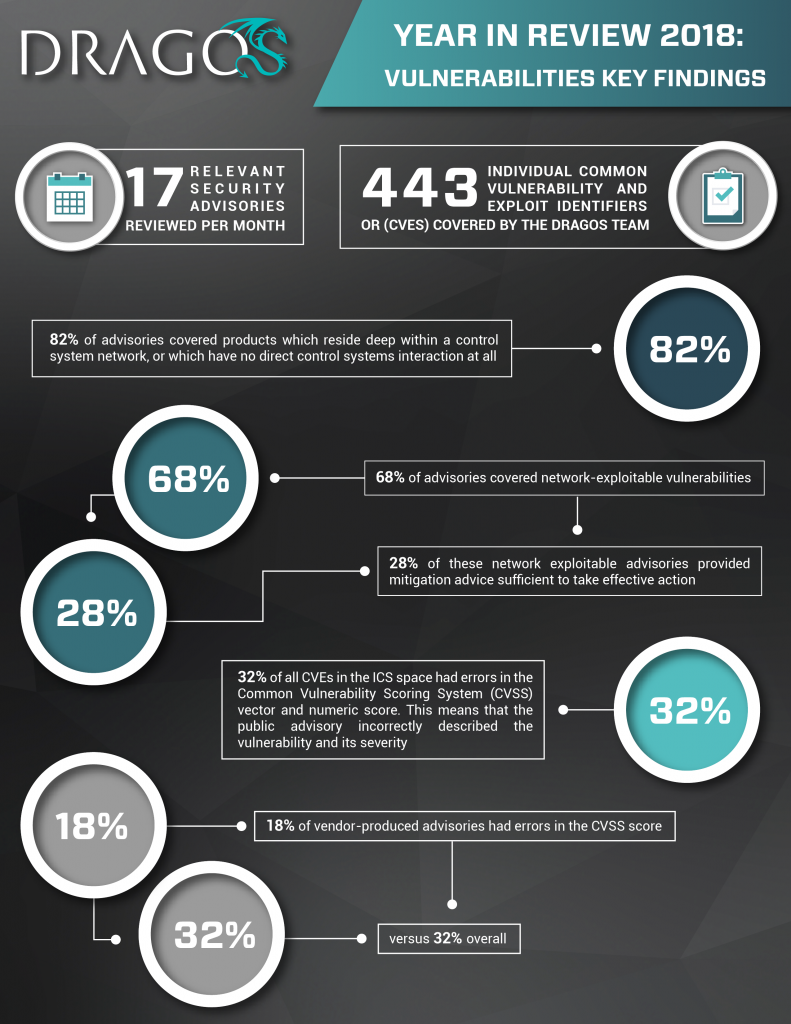
Vulnerabilities Key Findings from Dragos’s 2018 Year in Review.
View our next infographic
See the Dragos Platform in Action
Take the next step to protect your OT environment now with a free demo