ELECTRUM
Since 2016
In December 2016, in Kiev, Ukraine, a significant malware incident blacked out a portion of the city’s electricity for about an hour. ELECTRUM is the activity group responsible for the 2016 power outage event caused by the ICS malware CRASHOVERRIDE. But it wasn’t the first time this group targeted Ukraine.
ELECTRUM Threat Group Operations
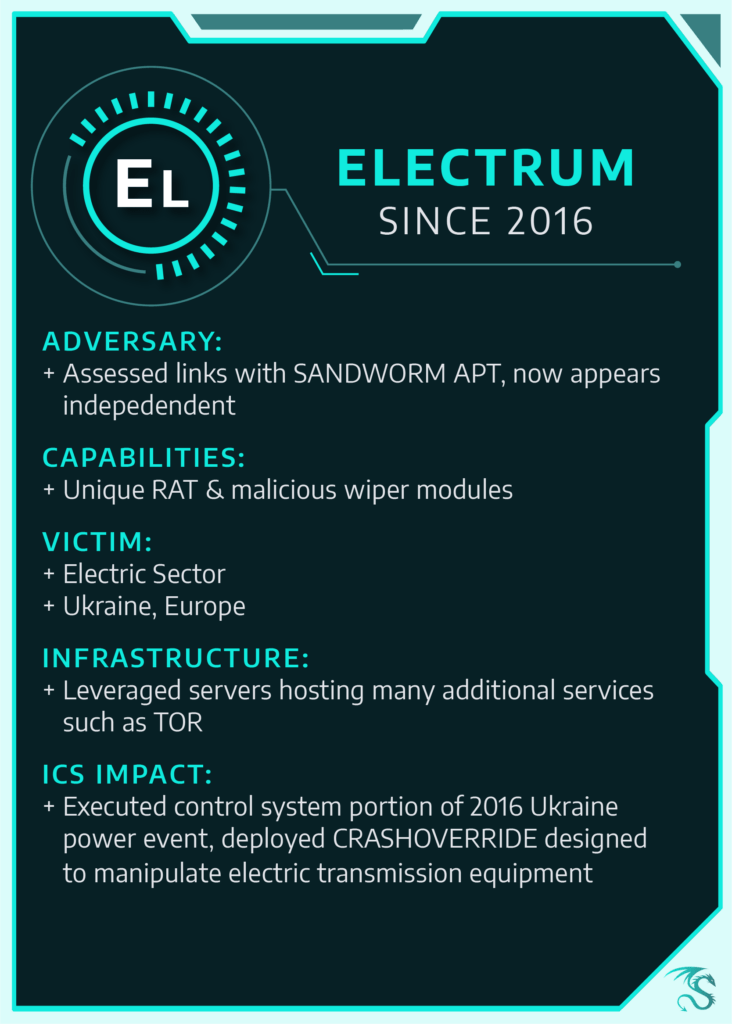
Dragos associates ELECTRUM with the SANDWORM Advanced Persistent Threat (APT) responsible for another Ukrainian power outage in 2015.
ELECTRUM previously served as a development group facilitating some of the earlier SANDWORM activity, but it moved into both a development and operational role in the CRASHOVERRIDE incident.
Earlier this year, Dragos identified new intelligence that provided more insight into ELECTRUM infiltration techniques and attack capabilities within the CRASHOVERRIDE malware. The group does not rely on exploits or zero-day vulnerabilities and instead leverages common exploitation behaviors and methodology.
For instance, the group used Microsoft SQL database servers as the gateway that bridges both the business and industrial control networks, to successfully compromise industrial control systems where they used stolen credentials to execute code.
ELECTRUM remains active, though our evidence suggests the group is no longer focusing exclusively on Ukraine. The group’s ongoing activity and link to the SANDWORM team indicate ELECTRUM’s sponsor could direct ICS disruption operations to other geographic areas. Dragos considers ELECTRUM to be one of the most competent and sophisticated threat activity groups currently in the ICS industry.
About Dragos Threat Intelligence
Dragos threat intelligence leverages the Dragos Platform, our threat operations center, and other sources to provide comprehensive insight into threats affecting industrial control security and safety worldwide. Dragos does not corroborate nor conduct political attribution to threat activity. Dragos instead focuses on threat behaviors and appropriate detection and response. Read more about Dragos’ approach to categorizing threat activity and attribution.
Dragos does not publicly describe ICS activity group technical details except in extraordinary circumstances in order to limit tradecraft proliferation. However, full details on ELECTRUM and other group tools, techniques, procedures, and infrastructure is available to network defenders via Dragos WorldView.