CHRYSENE
Since 2017
The CHRYSENE activity group developed from long-running cyberespionage activity that first came into the general public’s consciousness after a destructive cyberattack in 2012 impacting Saudi Aramco.
CHRYSENE Threat Group Operations
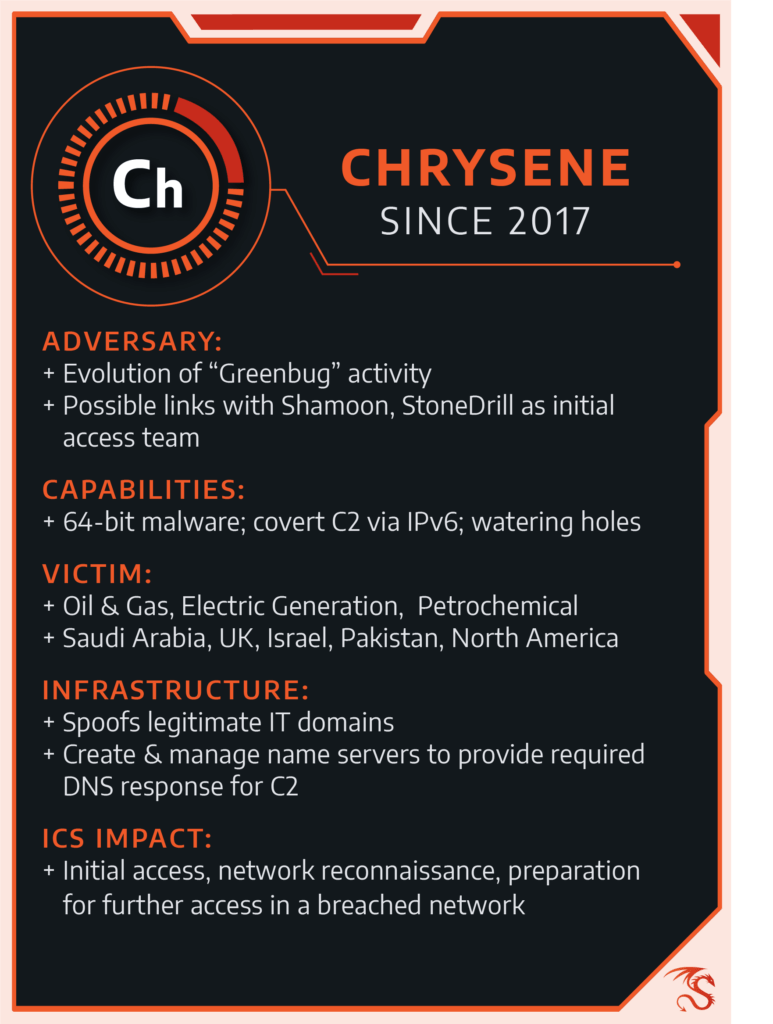
The group specializes in initial penetration—CHRYSENE compromises a target machine and passes the victim to another group for further exploitation. The group has been observed operating in at least Iraq, Pakistan, Israel, and the UK, and is an evolution of previous campaigns focusing exclusively on the Arabian Gulf region.
The 2012 Shamoon attack targeted Saudi Aramco and disabled tens of thousands of workstations. A group called Greenbug by Symantec and OilRig by Palo Alto Networks carried out initial preparations and network intrusion in advance of the Shamoon event, according to analysis following the attack. This group also appears to have been involved in supporting additional attacks—Shamoon 2—in 2016. Since then, it remains active and targets the Gulf Region of the Middle East.
CHRYSENE targets the petrochemical, oil, gas, and electric generation sectors while shifting targeting outside the Gulf Region. It also features significant advancement in technical capabilities from Greenbug/OilRig.
In 2017, Dragos observed new CHRYSENE activity and malware infrastructure targeting ICS networks, including watering hole attacks using websites unrelated to ICS, to compromise victims in an attempt to steal credentials and gain access to victims’ machines.
The group leveraged 64-bit malware that can only run in 64-bit environments and established unique Command and Control Network (C2) capabilities. (Full reports detailing CHRYSENE’s tools, techniques, and procedures are available to Dragos WorldView customers.)
Dragos uncovered multiple samples of CHRYSENE-related malware and other activity in 2018, indicating the group remains active and is evolving in more than one area, including revising and updating its malicious software toolkit. CHRYSENE aims to evade existing anti-virus and other detection mechanisms.
For now, the group appears to focus on penetrating networks and conducting ICS-specific reconnaissance. Dragos has not seen evidence of this group having any ICS-specific capabilities that could damage critical infrastructure. Rather, CHRYSENE appears focused on initial network access and information gathering required for future activity directly targeting ICS resources.
About Dragos Threat Intelligence
Dragos threat intelligence leverages the Dragos Platform, our threat operations center, and other sources to provide comprehensive insight into threats affecting industrial control security and safety worldwide. Dragos does not corroborate nor conduct political attribution to threat activity. Dragos instead focuses on threat behaviors and appropriate detection and response. Read more about Dragos’ approach to categorizing threat activity and attribution.
Dragos does not publicly describe ICS activity group technical details except in extraordinary circumstances in order to limit tradecraft proliferation. However, full details on CHRYSENE and other group tools, techniques, procedures, and infrastructure is available to network defenders via Dragos WorldView.