Advanced Threat Detection Solution
Stay Ahead of OT Cyber Threats with Real-Time Detection, Powered by Dragos OT Cyber Threat Intelligence
Are Cyber Threats Evading Detection in Your Critical Environments?
Sophisticated adversaries, hacktivists, and ransomware groups are targeting operational technology (OT) while existing defenses are falling behind. Organizations face poor visibility into OT-specific threats, noisy detection tools, and delayed investigations due to inefficient OT security workflows.
Industry-Leading OT Cyber Threat Detection
The Dragos Platform enables teams to detect, prioritize, and respond to OT cyber threats with accuracy, leveraging advanced intelligence and four detection methods to protect critical environments.
Alerts Based on Known Threat Behaviors
Leverages IOCs and behavior analytics to alert on suspicious activity and known adversary TTPs derived from Dragos Threat Intelligence, ensuring clear, actionable alerts for critical OT risks.
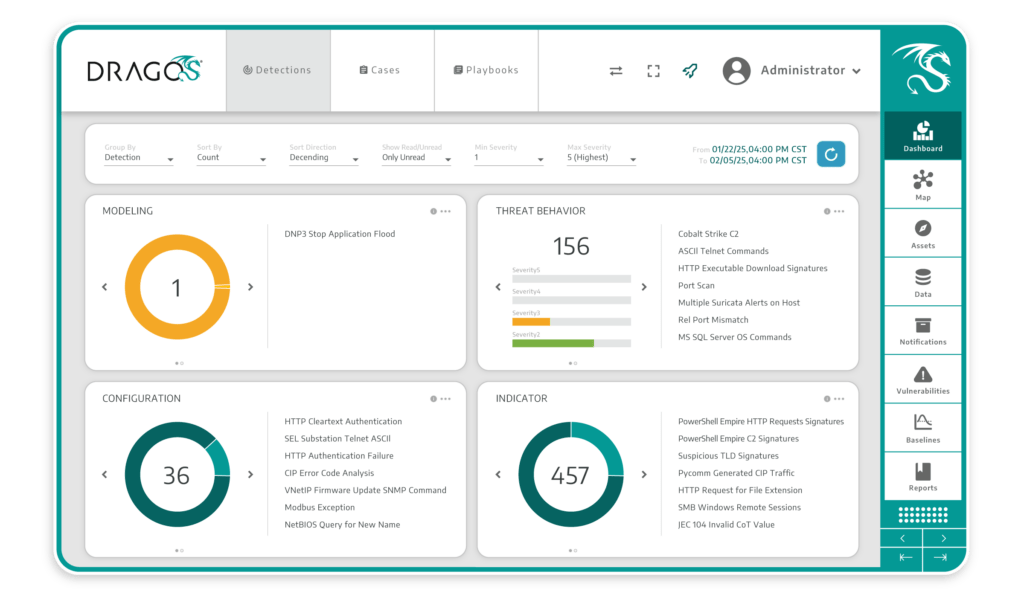
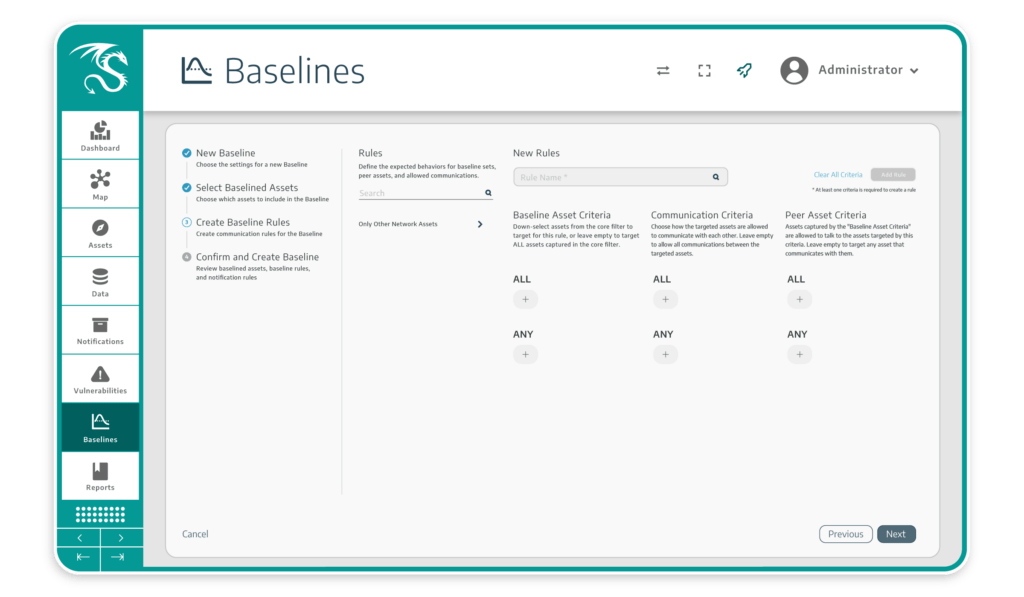
Detects Deviations from Normal
Uses baseline learning to detect deviations from normal configurations and anomalies in communication patterns, enabling the proactive identification of potential threats to support operational consistency.
Prioritizes Detections According to Risk
Reduces noise allowing you to focus on what matters most. Detections are categorized by severity and include insight into operational impact. With query-focused data sets, simply filter and analyze data for rapid identification of risks.
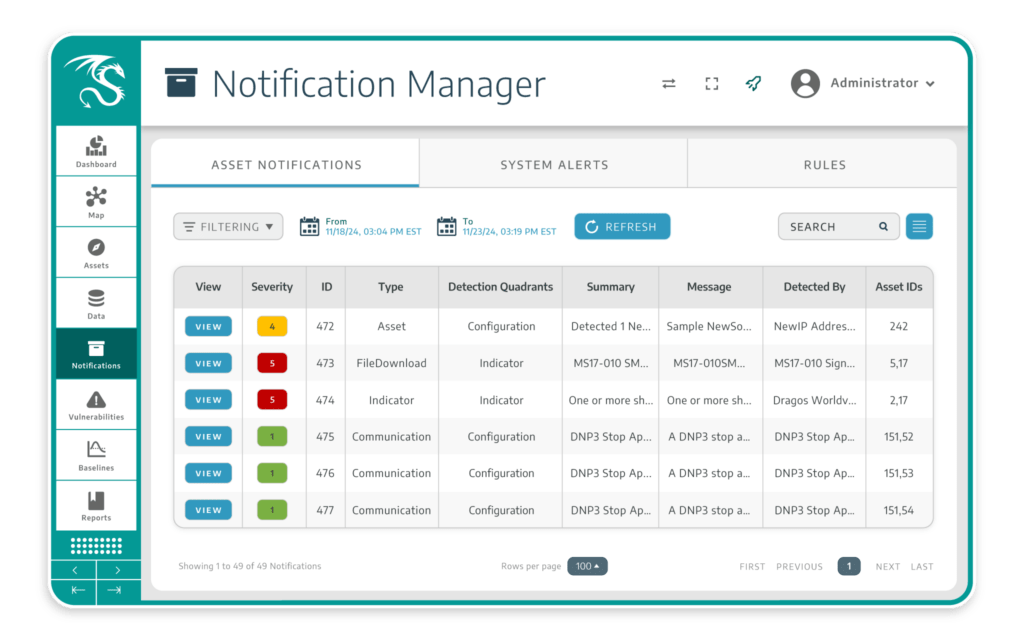
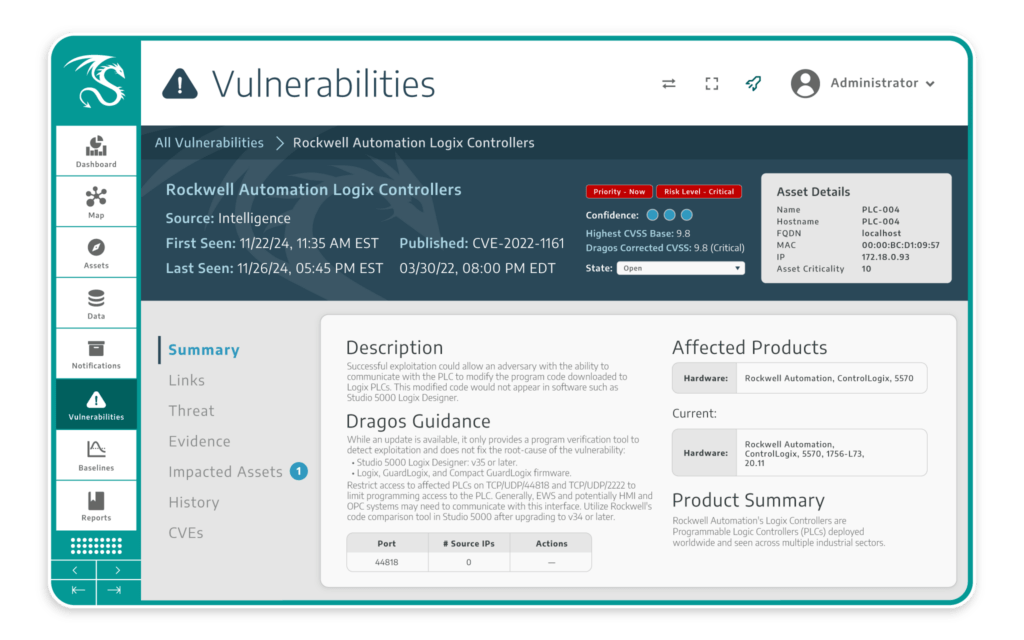
Offers Investigative Tools and Guidance
The Dragos Platform simplifies investigations with activity timelines, deep packet capture, and event triggers. Expert-authored playbooks offer actionable steps to investigate and respond, ensuring swift and effective incident response.
23 OT-focused Threat Groups, with 9 active last year.
The Dragos Difference
Dragos delivers continuous intelligence to adapt to evolving OT threats:
- Knowledge Packs: Weekly content updates with the latest IOCs, TTPs, vulnerabilities and playbooks.
- WorldView: Subscription-based OT cyber threat intelligence, offering detailed reports on adversary tactics, global trends, and custom insights for proactive defense.
- Neighborhood Keeper: An opt-in network for anonymous data sharing,
What Our Customers Say
See the Dragos Platform in Action
Take the next step to protect your ICS environment now with a free demo