Converging Data From Both IT and OT Networks
Dragos and Splunk have teamed to provide industrial customers with a deeper view of data collected from both IT and OT networks. Cybersecurity teams can now access ICS datasets from Dragos alongside the enterprise IT datasets collected in Splunk, providing analysts with improved overarching situational awareness.

This partnership expands the ICS cybersecurity ecosystem to ensure industrial infrastructure organizations are better prepared with enhanced visibility that improves threat awareness and threat detection inclusive of OT environments, regardless of where an adversary may attack. It enables more effective SOC (security operations center) functions including threat intelligence, threat detection, threat hunting, and incident response.
Together, Dragos and Splunk are providing ICS/OT focused cyber defenders with better tools, visibility, and expertise for a better SOC.
With this partnership, you will be able to:
- Manage your OT & IT cybersecurity posture in a single view and create workflows to ensure you are resolving threats and vulnerabilities on both OT/IT networks.
- Provide context rich asset visibility across your OT network, including PLCs, HMIs, SCADA systems, Historians, and other assets.
- Reduce alert fatigue by utilizing Dragos’s exclusive and curated Indicators of Compromise (IOCs) to look for malicious behavior on your network.
Dragos Apps and Integrations for Splunk
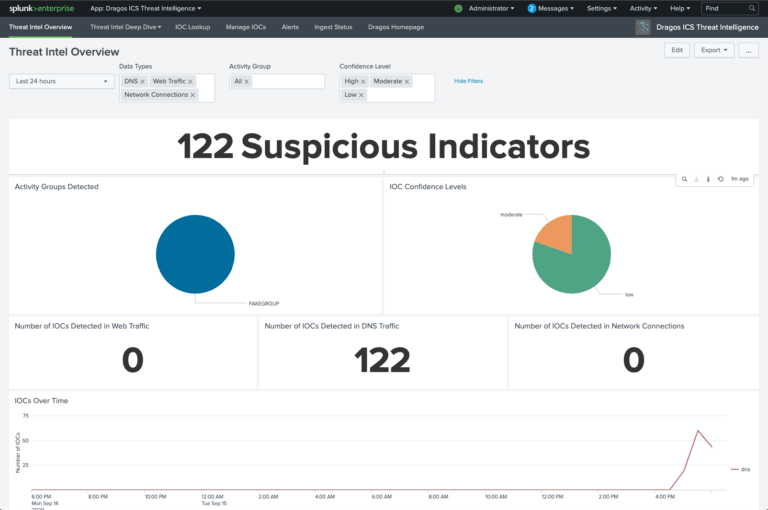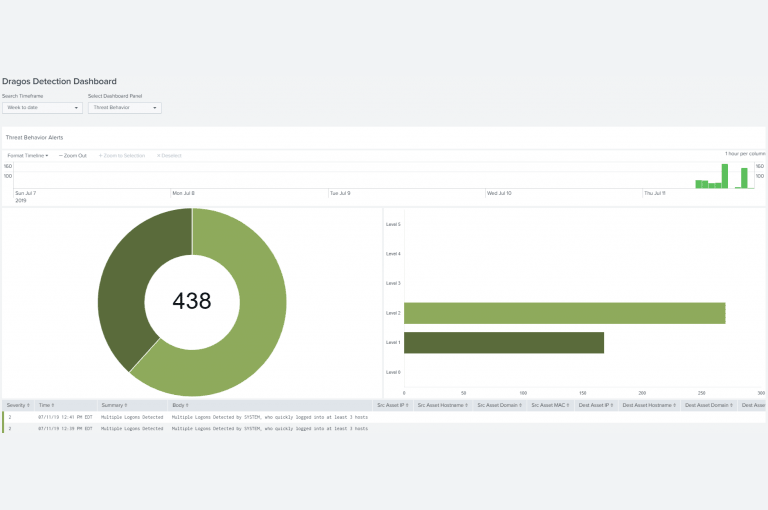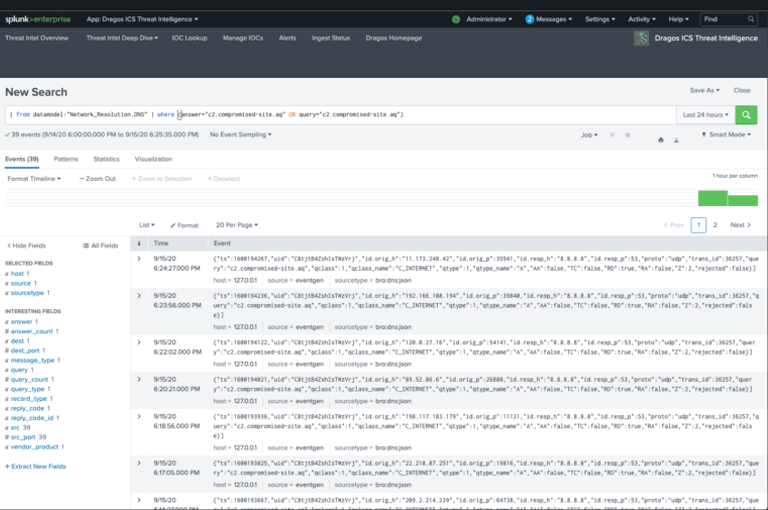
Dragos solutions integrate with Splunk to provide users with improved processes to ensure secure industrial operations. Click below to learn how to better protect your ICS environment with Dragos and Splunk.
Play the New Dragos + Splunk Boss of the SOC
Dragos and Splunk have released the latest Boss of the SOC (BOTS), a virtual ICS/OT capture-the-flag (CTF) challenge, developed to provide a fun and engaging way cybersecurity teams can enhance their capabilities. Sign up for free to play!
Learn how to better protect your ICS environment with Dragos and Splunk.