Frontline Perspective
Our perspective for protecting civilization from cyber threats
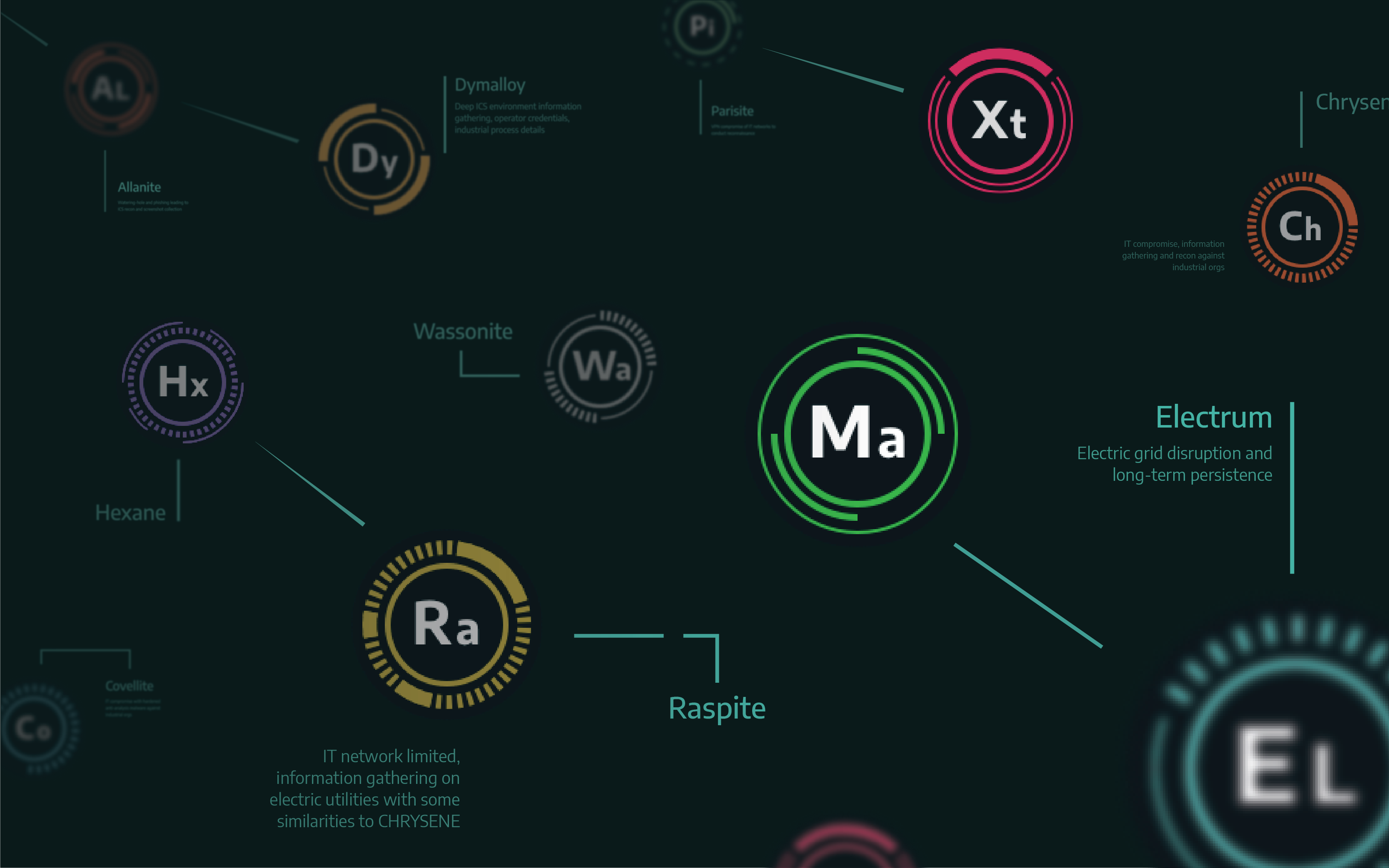
When the world needs help protecting critical infrastructure, they trust the experts who have been on the frontlines of the world’s most significant cybersecurity attacks. But saving the world from adversaries isn’t a one-person job. That’s why we want to empower you to take charge of your operational technology (OT) environments with resources produced by our top experts — our perspective for protecting modern civilization from industrial cyber threats.
The world trusts our frontline perspective.
We take pride in being the first team called when there is a new threat. Now it’s your turn.
Explore our many resources below that can help you on your ICS cybersecurity journey.

Want to speak directly to a Dragos expert?
We'll put you in touch with exactly who you need.