In today’s rapidly evolving cybersecurity landscape, integrating IT (Information Technology) and OT (Operational Technology) security into a unified security operations center (SOC) is increasingly critical. This integration not only enhances visibility and threat detection capabilities but also streamlines incident response processes.
As OT threats have become more frequent and sophisticated, understanding cybersecurity maturity is crucial. Data shows that cyber adversaries increasingly target industrial control systems (ICS) and OT environments to cause physical damage. In 2023, ransomware attacks against industrial organizations increased by 50 percent, totaling 905 incidents.
In this blog, we deep dive into the challenges, strategies, and benefits of creating a unified SOC that incorporates OT asset visibility, based on insights from industry leaders CrowdStrike and Dragos.
Watch our on-demand webinar with experts from Crowdstrike and Dragos on how to unify your Security Operations Center (SOC).
Watch On-DemandIntegrating OT into IT Security Operations
The journey towards cybersecurity maturity and integrating OT into an IT-focused security operations center (SOC) is complex and multifaceted, requiring significant planning and adaptation over many months or even years. Maturing your organizational cybersecurity programs to include monitoring and securing OT environments centers on three key concepts: people, process, and technology.
- People: It is crucial to identify and train the right team members. Those in the SOC need to understand OT environments and collaborate effectively with OT engineers. This involves not just IT personnel being reassigned to OT roles but also fostering an environment where both teams can work together, respecting each other’s expertise.
- Process: A comprehensive approach to incident response is vital. This includes defining how to conduct investigations, analyze data, and prioritize actions. Understanding the unique needs and operations of OT environments is essential to avoid disruptions that can have significant operational and safety impacts.
- Technology: Implementing the right technology is key. This includes security information and event management (SIEM), incident workflow and orchestration, threat intelligence, OT network monitoring and threat detection, and endpoint detection and response (EDR) technologies.
This is still something organizations are struggling with; this is not a one size fits all thing. There are plenty of companies that have done wonderful things ingesting OT data into an already operational SOC focused on IT, but it is not something you just flip a switch and move forward on. It is something that takes a lot of planning.
Dragos Director of Strategic Accounts Sam Van Ryder
Unifying IT & OT – A New Era in Cyber Defense
A unified SOC must bridge the cultural gap between IT and OT teams, each with different priorities and operational speeds. While IT teams are used to rapid changes, OT environments require more calculated and cautious approaches due to their direct impact on business operations and safety.
Building this unified approach requires starting with basic, manageable tasks and gradually evolving these tasks through close cooperation and mutual understanding. Engaging OT teams early, understanding their critical systems, and respecting their operational constraints are crucial steps in maturing organizational security programs. This collaboration fosters a trust that is essential for effectively securing the increasingly interconnected IT and OT environments.
Additionally, digital transformation and the integration of IT and OT is now a reality, necessitating harmonious network operations to maintain functionality. However, increased interconnection also introduces opportunity for advanced threats. A lack of unity between IT and OT can create blind spots that adversaries exploit, potentially leading to operational shutdowns and significant financial losses, as well as regulatory noncompliance.
The blind spot between IT and OT is the real problem, as we’ve seen a lot of adversaries start in the IT environment and move into OT, though that’s not always the case. If you are completely blind (without visibility) and unprotected in that environment, relying on the air gap someone created 15 or 20 years ago is not an effective security strategy. If you are an IT person and this is new to you, hopefully that kind of perks your ears.
CrowdStrike Senior Product Marketing Manager Adam Roeckl
Scalability must be matched with enhanced security, bridging the visibility gap between IT and OT. As recent incidents have shown, adversaries often exploit this lack of visibility by moving from IT to OT environments to evade detection, which highlights the fact that relying on outdated air gaps is not sufficient; modern security strategies must integrate protections across both domains.
Maturing security operations involves several steps:
- Establish a baseline. Creating a baseline by conducting architecture assessments, creating incident response plans, and organizing asset inventories.
- Operationalize key ICS security controls. Fundamental OT compensating controls must be operationalized, key OT vulnerabilities identified, and a Crown Jewels assessment performed to fully understand the risk of the environment.
- Optimize key ICS security controls. Having the ability to detect and respond to incidents is essential. This can be expanded and optimized through the integration of OT incidents and intelligence with a SOC that provides validation of the defensive controls, further enhancing security.
The SANS 5 Critical Controls for ICS Cybersecurity provide a structured approach to what is outlined above. Develop an ICS-specific incident response plan, design defensible architectures, ensure ICS network visibility and monitoring, secure remote access, and manage vulnerabilities based on risk. These controls must be tailored to the unique mission profiles and operational lifespans of OT environments.
You must think through the industrial and business processes and impact. What does it mean if we declare we shut down or isolate this facility? What is the financial business impact? You cannot use the same approach from the IT side by patching everything because that creates downtime in an environment that usually depends on uptime seven days a week, 365 (days a year). So, make sure it aligns with business requirements and risk.
Dragos Director of Senior Service Owner Incident Response Services Kai Thomsen
In a new era in cyber defense, effective cybersecurity in integrated IT/OT environments demands collaboration between the IT and OT teams. A unified SOC with cross-disciplinary communication and awareness of critical assets on both sides enables more effective defense, mitigating risks and preventing adversaries from achieving their destructive goals.
Building a Unified SOC with CrowdStrike and Dragos
A SOC utilizes a range of cybersecurity tools to monitor, detect, respond to, and manage security incidents, providing essential visibility, analytics, and response capabilities to safeguard organizational assets. By bridging IT and OT cybersecurity, organizations can leverage the Dragos Platform into the CrowdStrike Falcon® Next-Gen SIEM. This integration offers full visibility into OT/IoT assets, detections, and vulnerabilities within the CrowdStrike Falcon platform, also enriching the Dragos Platform with additional threat telemetry and endpoint detection and response (EDR) asset information. This constructive collaboration accelerates the detection, investigation, and response to cyber incidents.
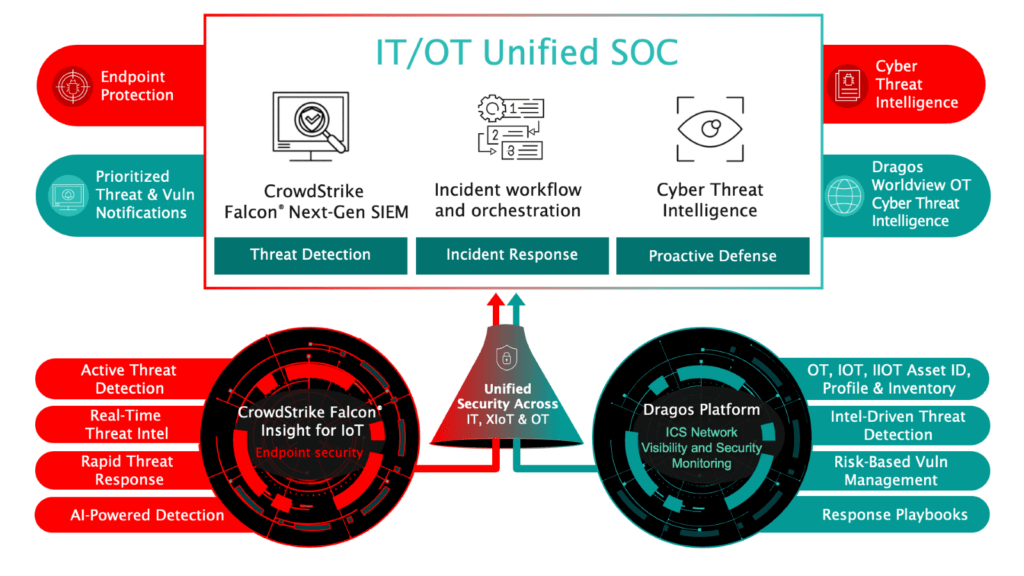
Plus, the integration enables SOC analysts to conduct more thorough investigations and root cause analyses across IT and OT environments, to swiftly identify malicious behavior on OT networks, providing the context needed to reduce false positives, prioritize mitigations, and achieve faster response times, thereby reducing mean time to respond and recover (MTTR).
Slapping something from IT over into OT you are going to cause yourself more headaches than you expected, and you might not be getting any of the functionality that you are paying for. So, I think that is critical for partnerships like Dragos and CrowdStrike and are extremely important to defending from all angles.
CrowdStrike Senior Product Marketing Manager Adam Roeckl
To continue the discussion, the CrowdStrike and Dragos webinar, “Unified SOC: Centralized Security Data with OT Visibility for Intelligence Driven Investigations,” is now available on-demand. For more information about the partnership between Dragos and CrowdStrike and these integrated solutions, visit https://www.dragos.com/partner/crowdstrike/.
View Our Webinar
Ready to put your insights into action?
Take the next steps and contact our team today.
