Welcome back to The Hunt, a blog series where we dive into the value of security through proactive threat hunting. While finding the “bad guys” is the mission, the benefits can come in different forms. Today, we discuss one of the positive outcomes of threat hunting on Operational Technology (OT) environments, which is the identification of misconfigurations. Misconfigured equipment is common across OT environments and exposes systems to unnecessary risk. Threat hunting can help close the gap. Misconfigurations not only open the door to security breaches but also could lead to operational disruptions if leveraged by a malicious threat actor. By identifying and rectifying these vulnerabilities, we can enhance both the security and efficiency of OT environments.
The Dragos OT Watch team uses the Dragos Platform to detect potential misconfigurations and uncover hidden threats within our customers’ environments. Combining human expertise with advanced technology, Dragos can fortify defenses and mitigate risks in ways that technology alone cannot.
Boston Beer Company Transforms OT Cybersecurity & Reduces Costs
In a recent Dragos Case Study, OT Watch Customer, Boston Beer, discusses the impact of identifying misconfigurations and operational benefits of threat hunting.
Download Case StudyWhat Are Misconfigurations?
Misconfigurations are errors or flaws in the setup of software, devices, or network architecture within an Operational Technology (OT) environment. These can include incorrect settings, default passwords, or insecure configurations that expose the system to potential risks. Misconfigurations are common and can significantly impact the security and operational efficiency of OT environments. Common examples of misconfigurations include:
- Incorrect IP Address Configuration: An OT device configured with an incorrect IP address can prevent proper communication between critical systems, leading to operational disruptions.
- Exposed DNS Connections: Devices configured to point to external DNS resolvers can expose the internal network to potential external attacks.
- Insecure Protocols: The use of insecure protocols, such as SMBv1, Telnet, or FTP, which transmit data in plaintext, can be exploited by attackers to intercept sensitive information.
- Default Credentials: Devices or systems that are left with default usernames and passwords can be easily accessed by unauthorized users.
Misconfigurations can lead to several risks, both from a security and operational perspective:
- Security Vulnerabilities: Misconfigurations can create entry points for unauthorized access, allowing attackers to escalate privilege to gain control of the system or to steal sensitive data.
- Operational Disruptions: Errors in configuration can cause communication failures between devices, delays in process execution, and even complete system shutdowns, affecting the overall efficiency of operations.
- Increased Attack Surface: Misconfigurations can increase the number of potential attack vectors, making it easier for adversaries to find and exploit weaknesses within the network.
Identifying Misconfigurations with the Dragos Platform
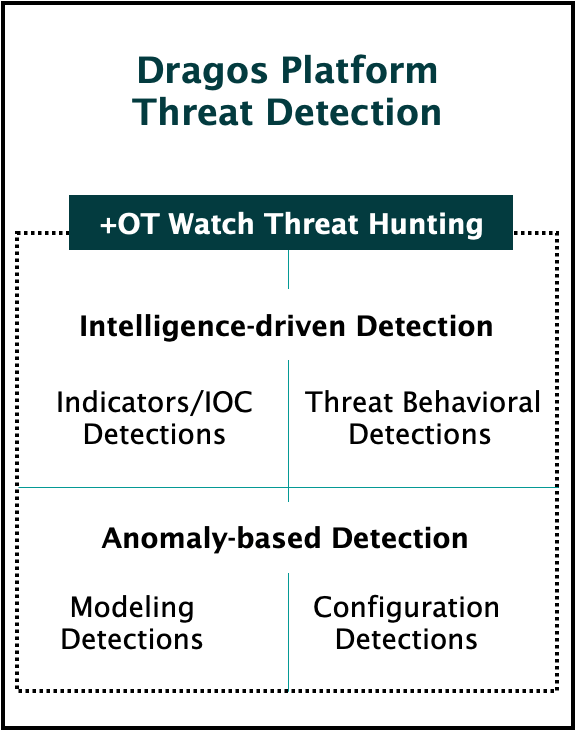
Dragos OT Watch threat hunters continuously monitor customer environments using the Dragos Platform. The Platform employs four types of threat detection, including modeling, which defines “normal” behavior and identifies deviations over time. In OT environments, this method can detect misconfigurations by analyzing protocol interactions and flagging unusual or unexpected activity. When the Dragos Platform flags these anomalies, OT Watch threat hunters investigate to identify and escalate misconfigured assets. The proactive identification and alerting of misconfigurations can significantly enhance both security and operational efficiency. Let’s break down a few examples.
The “Low Hanging Fruit” Hunt:
With each OT Watch customer we onboard, step 1 is completing the “Low Hanging Fruit Threat Hunt.” This initial threat hunt focuses on identifying misconfigurations and insecure-by-design protocols within the OT environment. The goal is to find easily exploitable configurations and alert customers for remediation, enhancing security from the outset.
Metrics reveal that 100% of all OT Watch customers had at least one significant misconfiguration issue, highlighting the importance of this proactive approach.
Hunting for External DNS Communications:
One prevalent instance discovered during routine threat hunts by OT Watch is the misconfiguration of DNS settings on hosts. In many cases, OT Watch found that organizations had DNS settings on at least one host configured to point to external addresses like Google DNS. This misconfiguration could expose internal networks to potential external attacks if the firewall is not properly configured to block this traffic. By identifying this issue and alerting affected organizations to correct the misconfiguration, OT Watch helps close a significant security gap and reduce the risk of the organization being targeted by attackers.
Hunting for Insecure Remote Access Solutions:
When performing hunts across its customer base looking for the use of insecure remote access solutions, OT Watch found that insecure remote access solutions were present in over 10% of customer OT environments. In one case OT Watch threat hunters discovered an insecure remote access solution being used by a vendor in the customers OT environment without permission. The customer subsequently revoked and blocked the unapproved access method. A couple of weeks later, the customer reported to OT Watch that the vendor had since been compromised and the customer was able to report that they had already audited and revoked unapproved access from that vendor.
Controller Mistakenly Configured to Poll an External IP Address:
During routine hunting operations, OT Watch uncovered a real-time automation controller (RTAC) mistakenly configured to poll an external IP address instead of an internal asset. This misconfiguration could have exposed the RTAC to unauthorized access. The OT Watch team immediately recognized the non-RFC1918 address as suspicious and brought the misconfiguration to the customer’s attention and they corrected the IP address the RTAC was polling. This proactive approach to finding and eliminating a potentially serious security misconfiguration was lauded by the customer for how quickly it was discovered by the technology deployed and by the recommendations made by the OT Watch team.
The Value of Addressing Misconfigurations in Your OT Environments
Identifying and addressing misconfigurations via threat hunting offers several benefits.
- Enhanced Security: By closing gaps that could be exploited by attackers, organizations can significantly improve their security posture. The Dragos Platform threat detection capabilities identify and prioritize these gaps effectively.
- Reduced Risk of Crises: Early detection and resolution of misconfigurations can prevent potential crises, such as data breaches or operational failures, thereby safeguarding both the organization and its stakeholders. The Dragos Platform’s continuous monitoring and advanced analytics play a crucial role in this proactive approach.
- Improved Operational Efficiency: Correcting misconfigurations ensures that systems operate as intended, reducing downtime and increasing productivity. The Dragos Platform’s automated analysis and reporting helps organizations understand and rectify issues quickly.
Hunt for Misconfigurations with Dragos + OT Watch
The Dragos Platform is crucial in enabling OT Watch’s threat hunts. It provides comprehensive visibility into the OT environment, signaling misconfigurations and vulnerabilities that might otherwise go unnoticed. Combining advanced technology with human expertise, Dragos protects OT environments against both known and emerging misconfigurations. This proactive approach significantly enhances security and operational efficiency, highlighting the importance of maintaining a secure and efficient OT environment.
If you are interested in learning more about Dragos Platform and OT Watch, please contact us.
Request a Platform Demo
Ready to put your insights into action?
Take the next steps and contact our team today.

