Dragos is an industrial cybersecurity company leveraging software, intelligence, and professional services to safeguard civilization. The SANS Institute empowers cybersecurity professionals with high quality training, certifications, degree programs, and more to help them make the world a safer place. Together, we have created a blog series about OT cybersecurity fundamentals, crafted for practitioners and executives alike to gain a better understanding of operational environments and their unique security requirements. This is the second blog in our series.
Operational technology (OT) serves as the cornerstone of the modern industrial world, ensuring the seamless function of critical infrastructure across numerous sectors. With the rapid convergence of information technology (IT) and OT networks, coupled with escalating cyber threats, understanding and securing operational technology network architecture has never been more crucial. This installment of the Dragos and SANS ICS OT Cybersecurity Fundamentals Blog Series delves into the components, systems, and security implications of OT network architecture. See the first blog in our series covering, What Is OT Cybersecurity?
OT networks form the backbone of industrial operations, connecting and coordinating various operational technology components to monitor, control, and manage physical processes. Unlike traditional IT networks that handle data and communications, OT networks are specifically designed to support real-time operations across industrial sectors, including manufacturing, utilities, and transportation sectors.
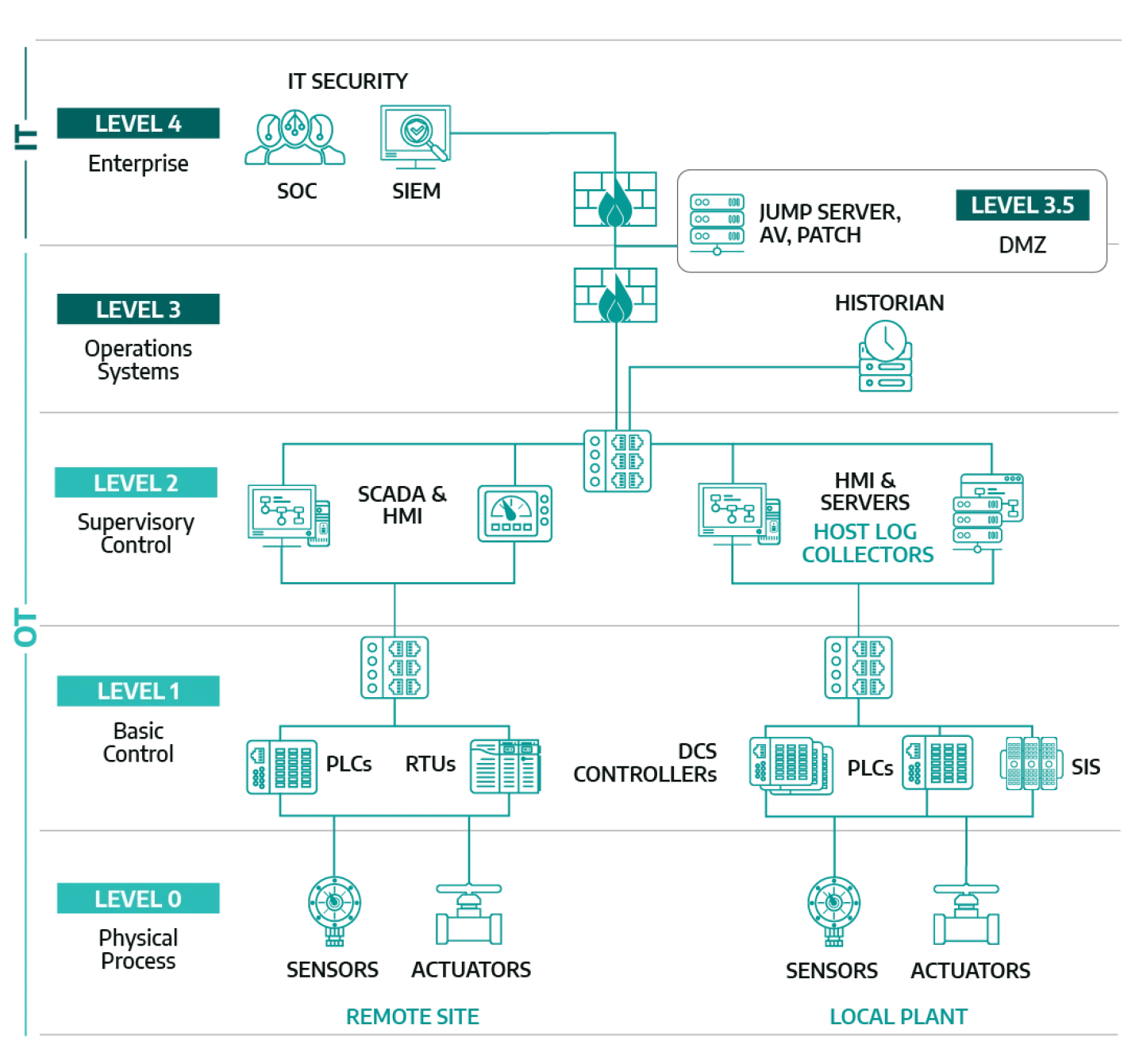
One of the best ways for IT cybersecurity pros to understand OT environments is to get a basic grasp of the Purdue Model, an architectural reference model that maps out the relationships of both IT and OT networks in an industrial setting.
Like the ISO 7-layer model, the Purdue Model breaks things down into levels—in this case it is five layers from Level 0 to Level 4. Level 4 is all enterprise IT systems that veteran cybersecurity pros understand well. Below that level, you’ll find the OT networks that make up the fabric of industrial automation and control systems.
- Operations Management: include systems that support managing workflows and scheduling across plant operations.
- Supervisory Control: includes systems used broadly (and often remotely) to monitor and control physical processes.
- Basic Control: includes systems used to sense and manipulate the physical process at the 1:1 device level.
- Safety and Protection: includes safety instrumented systems (SIS) that will trigger shutdowns when unsafe conditions are detected; they’re often logically separated from basic control.
- Process: the machinery that governs the actual physical process.
Within that structure, operational technology (OT) comprises both hardware and software designed to monitor, control, and manage industrial operations. This technology underpins the functionality of various sectors, including manufacturing, utilities, and transportation. Central to OT networks are operational technology components such as:
- Programmable Logic Controllers (PLCs): industrial computers designed to control processes. PLCs are ruggedized and adapted for high reliability, ease of programming, and process fault diagnosis. PLCs replace hard-wired relay logic systems and are used in assembly lines, machines, and robotic devices.
- Remote Terminal Units (RTUs): microprocessor-controlled electronic devices that interface with physical objects in the field. RTUs connect to a distributed control system (DCS) or SCADA system, transmitting telemetry data to a master system and receiving control messages. RTUs are used for monitoring and controlling devices in industries like energy, oil and gas, and water treatment.
- Industrial Control Systems (ICS): Electronic control systems used for industrial process control. Industrial Control Systems range from small modular controllers to large interconnected distributed control systems (DCSs). ICSs receive data from sensors, compare it with setpoints, and control processes through final control elements (e.g., valves). They are crucial in industries like chemical processing, power generation, and manufacturing.
- Distributed Control Systems (DCS): Computerized control systems for industrial processes. Unlike centralized controllers, DCSs distribute autonomous controllers throughout the system. They increase reliability, reduce installation costs, and allow local control functions near the process plant. DCSs are commonly used in continuous process plants where high reliability and security are essential.
- Human-Machine Interfaces (HMIs): User interfaces or dashboards connecting a person to a machine, system, or device. Operators use HMIs to optimize processes by visualizing real-time information about industrial processes. HMIs visually display data, track production time, monitor machine inputs/outputs, and oversee key performance indicators (KPIs).
- Supervisory Control and Data Acquisition (SCADA) systems: SCADA systems are used to monitor and control industrial processes. They collect data from remote sensors, display it on operator screens, and allow control actions. SCADA systems are commonly used in large continuous process plants where reliability and security are critical.
- Internet of Things (IoT) and Industrial IoT (IIoT) devices: IoT refers to interconnected devices (e.g., sensors, actuators, and smart devices) that communicate over the internet. IIoT extends this concept to industrial applications. IIoT devices collect data, enable predictive maintenance, and enhance efficiency in manufacturing, energy, and transportation sectors.
These devices and systems facilitate the efficient operation of power plants, manufacturing facilities, oil refineries, and more, ensuring the stability and reliability of critical infrastructure.
Industrial control systems (ICS) are pivotal in OT networks, orchestrating industrial processes through a network of controls, systems, and devices. The increasing merger of IT and OT landscapes, alongside rising cyber threats, highlights the need for stringent ICS security. Effective security measures should encompass continuous monitoring, IT/OT threat detection, and risk-based vulnerability management, ensuring a robust defense against potential disruptions and attacks.
SCADA systems play a vital role in many OT network environments, enabling the remote monitoring and control of industrial processes. Given their critical function in operations that span vast geographic areas, SCADA systems require strict security protocols to ward off threats from malicious actors.
The landscape of securing OT network architecture is evolving, driven by the IT-OT convergence and sophisticated cyber threats. Modern challenges necessitate advanced OT security solutions that provide contextualized visibility, security, and control over IT and OT networks. Understanding OT systems components and security implications is crucial for implementing effective protection measures.
Key components of an effective OT security program include five critical controls:
- OT-Specific Incident Response Plan: Have an operations-informed incident response plan with a focus on system integrity and recovery capabilities during an attack.
- Defensible Architecture: Design architectures that support visibility, log collection, asset identification, segmentation, industrial DMZs, and process-communication enforcement.
- ICS Network Visibility & Monitoring: Enable continuous network security monitoring of the ICS environment using protocol-aware toolsets and system of systems interaction analysis capabilities.
- Secure Remote Access: Identify all remote access points and allowed destination environments and implement on-demand access and multi-factor authentication (MFA) where possible.
- Risk-Based Vulnerability Management: Understand the cyber digital controls in place and device operating conditions to make risk-based vulnerability management decisions regarding your OT environment.
Operational technology is indispensable for the continuity and efficiency of critical industrial operations. As the integration of digital technologies with physical processes continues to deepen, understanding and securing OT network architecture becomes paramount. By understanding operational technology components and systems that constitute OT networks and implementing comprehensive security measures, organizations can navigate the complexities of the modern IT-OT landscape with confidence, ensuring the resilience and reliability of critical infrastructure.
Dragos and SANS ICS have created an OT Cybersecurity Glossary & Quick Start Guide for IT security professionals to help those more familiar with IT environments understand more about OT cybersecurity priorities.
Download Now