This blog is the second in a series of blogs published by Dragos covering the requirements, documents, and key concepts of the ISA/IEC 62443 series of cybersecurity standards. In our first blog, we provide a general overview of the ISA/IEC 62443 series. This blog offers a detailed overview of the documents within the series, and is followed by a third blog that covers the key concepts and approaches of ISA/IEC 62443.
The goal of the ISA/IEC 62443 series is to improve the reliability, integrity, and security of IACS using a risk-based, methodical process. The benefits of using a standards-based approach include reducing the likelihood of a successful cyberattack, reducing the complexity of systems by using a common set of requirements among stakeholders, and improving the security throughout the system lifecycle.
The standards describe a set of common terms and requirements that can be used by asset owners, product suppliers, and service providers to secure their control systems and the equipment under control, outlining a comprehensive framework for design, planning, integration, and management of secure systems.
ISA/IEC 62443 is a functional standard – the series sets objectives for security performance but does not define how these objectives should be met. The series is referenced throughout the NIST Cybersecurity Framework (CSF), and most recently, within the CISA Cybersecurity Performance Goals (CPGs.) The CPGs extensively reference ISA/IEC 62443-2-1 and ISA/IEC 62443-3-3 in almost every category, including account security, device security, data security, governance and training, vulnerability management, supply chain/third party, and response and recovery.
Adoption of any level of ISA/IEC 62443 is optional and dependent upon a risk assessment of the network. Dragos offers technology, infrastructure, and professional services support to translate the objectives within ISA/IEC 62443 into actionable pieces of your cybersecurity plan, customized for your environment and risk profiles.
Connect with a Dragos Expert
Learn more about our OT cybersecurity technology, services, and threat intelligence offerings.
Contact UsToday’s blog will give you a detailed overview of the documents found within the series of standards. In Part 1 of this blog series, we explained why the standards are important for asset owners.
Summary View of the ISA/IEC 62443 Series of Standards
The ISA/IEC 62443 series of standards and technical reports is arranged in four groups, corresponding to the primary focus and intended audience.
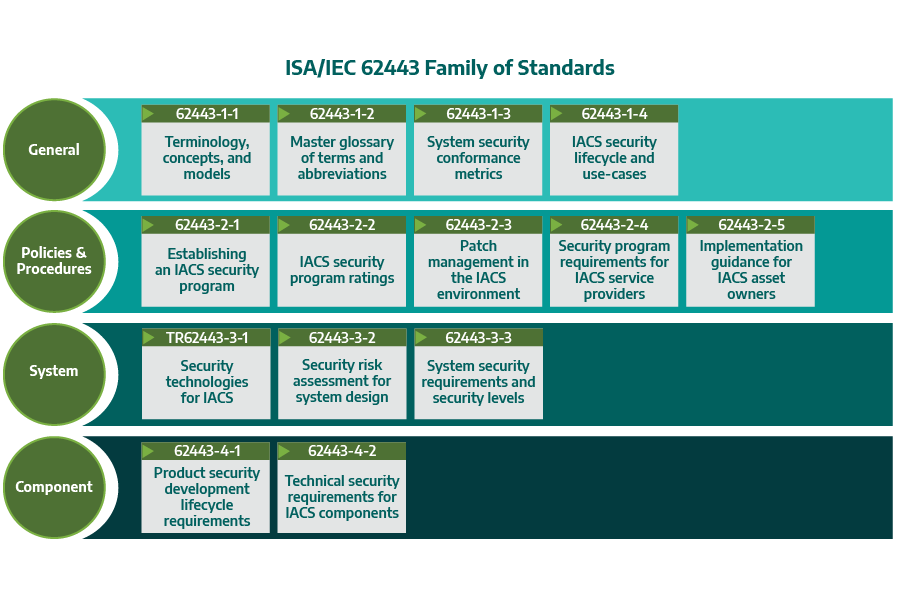
Group 1: General – This group includes documents addressing topics that are common to the entire series.
- Part 1-1: Terminology, concepts and models introduces the terminology, concepts and models used throughout the series. The intended audience includes anyone wishing to become familiar with the fundamental concepts that form the basis for the series.
- Part 1-2: Master glossary of terms and definitions is a list of terms and abbreviations used throughout the series. The master glossary will likely be delivered in an online format.
- Part 1-3: System security conformance metrics describes a methodology to develop quantitative metrics derived from the process and technical requirements in the standards.
- Part 1-4: IACS security lifecycle and use cases provides a more detailed description of the underlying lifecycle for IACS security, as well as several use cases that illustrate various applications.
Group 2: Policies and Procedures – The documents in this group focus on the policies and procedures associated with IACS security.
- Part 2-1: Establishing an IACS security program describes what is required to define and implement an effective IACS Security Program. The intended audience includes asset owners who have responsibility for the design and implementation of such a program.
- Part 2-2: Security Program Ratings provides a methodology for evaluating the level of protection provided by an operational IACS against the requirements in the ISA/IEC 62443 Series of standards.
- Part 2-3: Patch management in the IACS environment provides guidance on patch management for IACS. The intended audience includes anyone who has responsibility for the design and implementation of a patch management program.
- Part 2-4: Security Program requirements for IACS service providers specify requirements for IACS service providers such as system integrators or maintenance providers.
- Part 2-5: Implementation guidance for IACS asset owners provides guidance on what is required to operate an effective IACS Security Program. The intended audience includes asset owners who have responsibility for the operation of such a program.
Group 3: System Requirements – The documents in this group address requirements at the system level.
- Part 3-1: Security technologies for IACS describes the application of various security technologies to an IACS environment. The intended audience includes anyone who wishes to learn more about the applicability of specific technologies in a control systems environment.
- Part 3-2: Security risk assessment for system design addresses cybersecurity risk assessment and system design for IACS. The output of this standard is a Zone and Conduit model and associated Risk Assessments and Target Security Levels. These are documented in the Cybersecurity Requirements Specification. This standard is primarily directed at asset owners and system integrators.
- Part 3-3: System security requirements and security levels describes the requirements for an IACS system based on security level. The principal audience includes suppliers of control systems, system integrators, and asset owners.
Group 4: Component Requirements – This group includes documents that provide information about the more specific and detailed requirements associated with the development of IACS products.
- Part 4-1: Secure Product development lifecycle requirements describes the requirements for a product developer’s security lifecycle. The principal audience includes suppliers of Control System and Component products.
- Part 4-2: Technical security requirement for IACS components describes the requirements for IACS Components based on security level. Components include Embedded Devices, Host Devices, Network Devices and Software Applications. The principal audience include suppliers of Component products that are used in control systems.

Align with ISA/IEC 62443
Ready to put your insights into action?
Take the next steps and contact our team today.