This blog is part three of a three-part blog series adapted from Principal ICS Security Analyst Austin Scott’s DEFCON 2019 presentation. The full DEFCON slide presentation can be viewed here:
Executing ICS Purple Teaming for the Win
In this conclusion to the three-part series on ICS Purple Teaming, I will highlight the key advantages of ICS Purple Teaming and how a successful ICS Purple Team assessment is executed.
The Purple Team Advantage
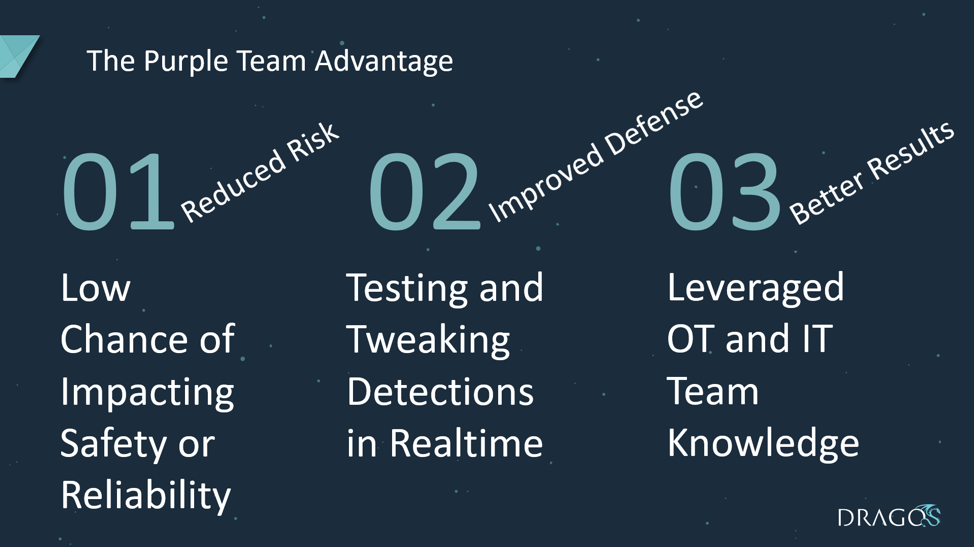
Risk Reduction Through Communication and Transparency
Constant and highly transparent communication greatly reduces the risk of an operational disturbance. In addition, this can help reduce the project risk if there happens to be an unrelated outage or issue at site during the assessment (issues and outages are quite common in many processes). If the operations team has a clear understanding of what the assessment team was doing at the time, the assessment team is not likely to take the blame. It is only natural to blame problems on a new element that has been introduced to a complex system. When things go wrong on site during an ICS cybersecurity assessment, the assessment team can expect to be questioned about it.
Improved Detection
Working closely and in real-time with the Blue Team enables active validation of event collection and detection capabilities of the ICS environment. Opportunities to execute enumerations, attacks, network pivots and privilege escalations against ICS environments and validate collection and detection in real-time are rare. The Blue Team should seek to gain as much value from the assessment as possible. Executing scenarios multiple-times, the collection of PCAPs and performing event collection and analysis enables the Blue Team to validate or tune their capabilities.
Yielding Better Results Through Knowledge Sharing
Operation teams spend years learning their plant. In time an operations team learns the rhythm of their process–the values, sights, smells, sounds that are normal (and those that are not). They learn the site-specific implementation of the technologies that have been deployed. They learn the custom code running in their PLCs and Controllers and the code running on their HMI, SCADA or DCS system. They learn the network connections, the serial connections, and the wireless radio links that allow data to flow throughout the environment. It can take years to fully understand the inner-workings of a complex ICS system. During a one-week or even a multi-week engagement, the ICS assessment team has an extremely limited window to learn the intricacies of a complex system of systems. Leveraging the considerable knowledge of the operations team opens up a myriad of possible new findings.
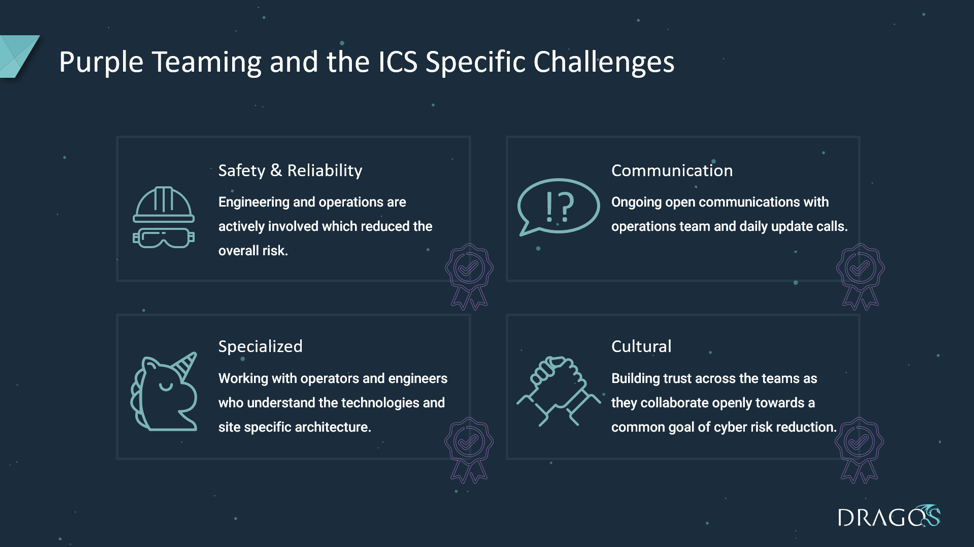
Preparing for a Purple Team Exercise
When entering into an ICS Purple Team project, it is important to understand and document the following:
- Planned Red Team Tactics and Tools
- Detection Methods
- Investigation Tools
- Triage Capabilities
A clear objective statement should be formulated, which covers the expected outcome of the engagement. For example, <company name> would like to determine if our current OT detection capabilities consisting of: Windows event logging and centralized management; Windows Defender and CrowdStrike’s Falcon endpoint protection; and the Dragos Platform’s passive OT network monitoring are capable of collecting, detecting, and responding to XENOTIME-like activity group behaviors in our plant’s environment.
Executing a Purple Team Assessment
During the Purple Team Assessment, each tactic that is used and the opportunities for detecting it should be documented. The success or failure of the detection should also be captured along with the corresponding PCAPs or event-related data. If new rules need to be created or tuned during the assessment, the Red Team tactics can be run multiple times to validate these changes.
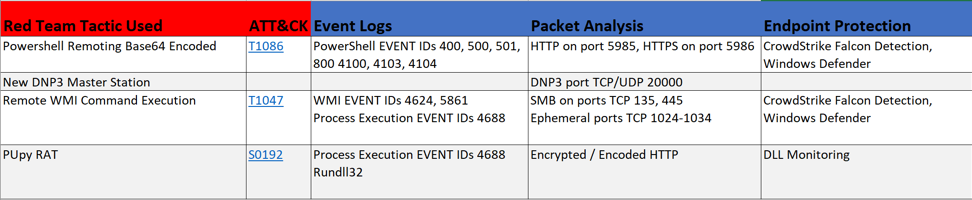
At the end of the Purple Team Assessment, the gaps in the Blue Team capabilities and vulnerabilities in the ICS environment uncovered should be documented in a final report. Recommendations on how to improve upon the Blue Team’s capabilities and address vulnerabilities should be provided in the report.
Conclusion
Our investigation into ICS Purple Teaming has demonstrated that not only does a Purple Team style engagement reduce risk to ICS environments, it also identifies gaps in the detection and response capabilities of the environment. Ultimately, a Purple Team approach can provide a more holistic assessment than a typical Vulnerability Assessment or Red Team engagement, as it is able to identify vulnerabilities, gaps in collection, blind spots in detection, and shortcomings in incident response capabilities.
Ready to put your insights into action?
Take the next steps and contact our team today.
