This blog is part one of a 3-part blog series adapted from Principal ICS Security Analyst Austin Scott’s DEFCON 2019 presentation. The full DEFCON slide presentation can be viewed here:
ICS Assessment Type Definitions
In this three-part blog article, I will detail:
- The differences between traditional ICS Assessments and an ICS Purple Team
- Potential challenges when working in an ICS environment
- How Purple Team Engagements can provide a more holistic approach to an ICS assessment
An Industrial Control System (ICS) Purple Team is a Grey-box, collaborative assessment between the Red Team and the Blue Team rather than a Black-box adversarial assessment. An ICS Blue Team differs from an IT Blue Team as it is comprised of not just the ICS cybersecurity team (if one exists) but also involves the site Operations team, Engineering team and IT team. Operators understand their network far better than an external assessment team could within the span of a 1-week engagement, so recruiting them into the penetration testing effort is advantageous. They enjoy the experience of taking an adversarial view of their own network and the opportunity to learn from ICS penetration testing experts. Building trust and a stronger customer relationship is often a byproduct of collaborative assessment.
Introduction
As a member of the Dragos Threat Operations Center (TOC), I am frequently engaged to perform cybersecurity assessments on Industrial Control System (ICS) environments. In my experience, the capabilities of ICS Blue Teams (network defenders) can vary wildly depending on the level of maturity of the organization.
Some TOC customers can detect our attacks in real-time and fine-tune their collection, ICS network detection and end-point event logging capabilities. Conversely, other customers lack logging and detection capabilities and are interested in finding as many problems as possible to secure remediation budget. In either case, the TOC has found that taking a collaborative approach (often referred to as Purple Teaming) when performing assessments has numerous benefits such as:
- Reduction of operational risk
- Production of more findings
- Well-tailored recommendations
- Opportunities for cross-organization collaboration and communication
- A more holistic assessment of the organization’s ICS vulnerabilities, collection resources, detection capacities and response planning
Cybersecurity Assessment Types
Definitions of different cybersecurity assessment types can vary depending on who you ask. In my experience, no two cybersecurity assessments are ever alike, and it is rare for an ICS cybersecurity assessment to neatly fit into any of these strict definitions. Nevertheless, it is essential to cover some general definitions here to highlight how the ICS-based assessments differ from their IT-based cousins.
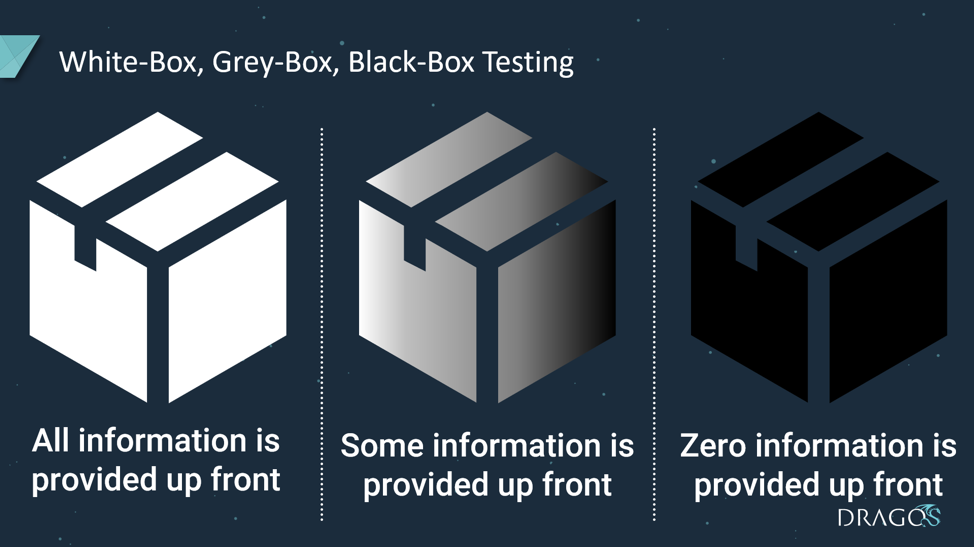
Cybersecurity assessment types are typically categorized in shades of boxes. In a “White-box” assessment, all the data is shared prior to or during the assessment. In a “Black-box” assessment, none of the data is shared prior to or during the assessment. “Grey-box” testing simulates an activity group that has maintained access to a network for an extended amount of time. The time an activity group spends in an environment is referred to as “dwell time”. For example, the activity group XENOTIME had a considerable amount of dwell time in a target ICS network. This dwell time allowed them to gain the in-depth knowledge required to develop their plant safety-system malware TRISIS. As we typically only have a week to perform these assessments and activity groups can dwell in an ICS networks for years, it usually makes sense to take a grey-box or even white-box assessment approach.
Let’s continue by discussing the three typical types of assessments we perform.
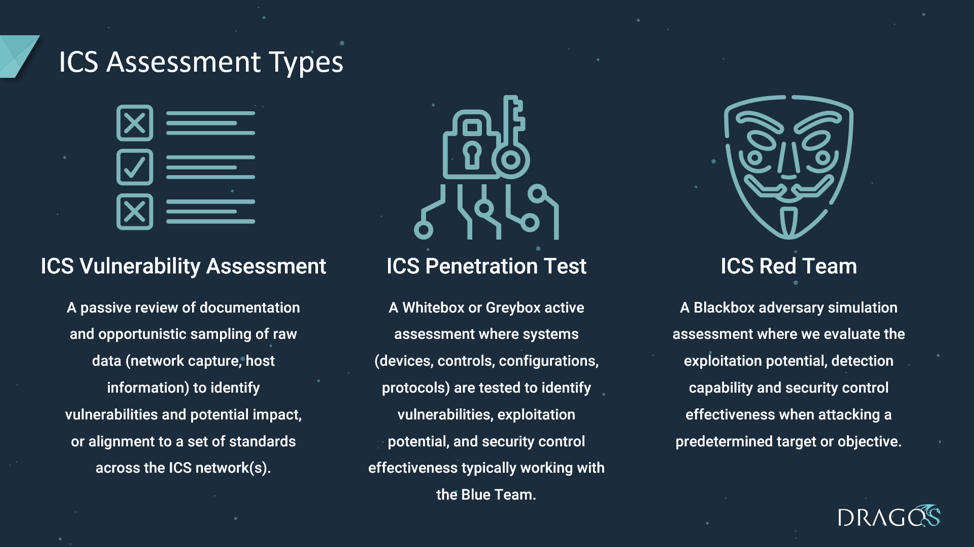
ICS Vulnerability Assessment
A passive, White-box review of documentation, and opportunistic collection of raw data (network capture and host information) which allows us to identify vulnerabilities and potential impact, or alignment to a set of standards across the ICS network(s).
ICS Penetration Test
A White-box or Grey-box active assessment where systems (including devices, controls, configurations, and protocols) are tested to identify vulnerabilities, exploitation potential, and security control effectiveness. This test type is typically conducted by working with the Blue Team.
ICS Red Team
A Black-box adversary simulation assessment where we evaluate exploitation potential, Blue Team detection capability, and security control effectiveness when attacking a predetermined target or objective. A Red Team assessment should include elements of physical security, electronic exploitation and social engineering.
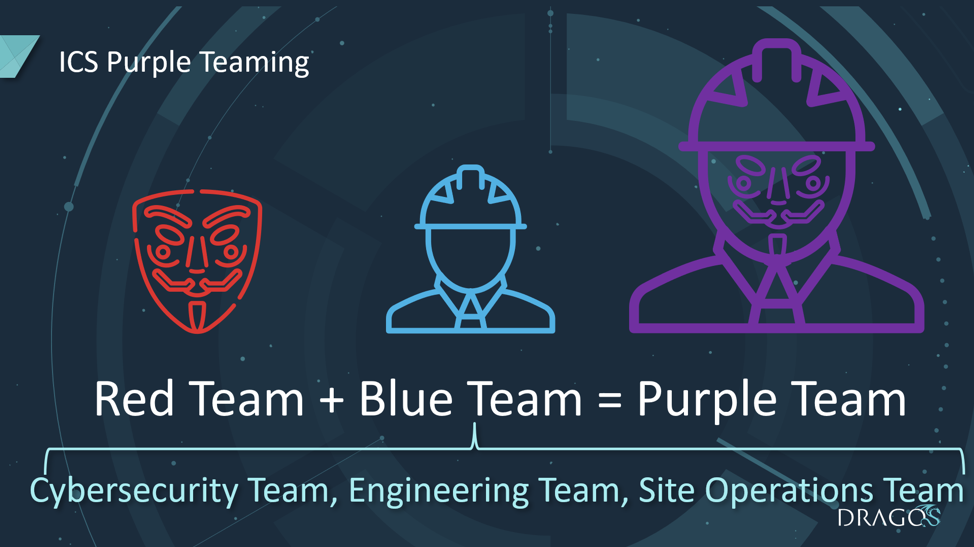
ICS Purple Team
An ICS Purple Team is a collaborative assessment between the Red Team and the Blue Team rather than an adversarial assessment.
It is important to note that the ICS Blue Team is comprised of not just the ICS cybersecurity team (if one exists), but often involves the site Operations team, Engineering team and IT team. It is nearly impossible to book all of the resources that are critical to the continued operation of a plant for an entire week-long (or multi-week) engagement. However, it is sufficient to have them available at critical times or on-call during the assessment.
Is Purple Teaming Cheating?
Some might argue that Purple Teaming is “cheating.” Providing information that may or may not be available to a real-life attacker does give the Red Team an advantage and does take some of the sport out of the exercise. The ultimate goal of any cybersecurity assessment should be maximizing cyber risk reduction. If all parties involved are not working toward that common goal, I would consider that to be a lost opportunity to reduce cyber risk.
Red Team and Blue Team Roles in a Purple Team Assessment
Here is how Purple Team collaboration works to everyone’s advantage:
The Blue Team assists the Red Team with pertinent information which can help them to progress through the network more quickly and efficiently. Gathering this information could take an activity group weeks or months to figure out on their own but is provided to the Red Team on the spot as required. Sometimes, automated defense mechanisms are tripped by the Red Team and they find themselves quarantined from the network. In these cases the Blue Team will work unblock the Red Team so that the assessment can progress further into the network.
The Red Team assists the Blue Team by communicating their enumerations, attacks, network pivots and privilege escalations in real-time. Furthermore, the Red Team can assist the Blue Team in fine-tuning and troubleshooting their detection mechanisms by making recommendations for detection improvements and running the attacks multiple times.
Is a Purple Team Assessment Always the Right Answer?
An ICS Purple Team approach is not well suited for every situation. Many organizations lack the maturity to even perform the most basic levels of collection, detection, and response to incidents. There are often situations where a customer is not prepared for the Red Team to produce many critical findings. For example, after completing a multi-year or multi-million dollar cybersecurity upgrade, the Blue Team may be looking for a way to show senior leadership a return on their investment. At the end of the day it’s up to the customer to decide the type of assessment that would be most beneficial to the direction and the maturity level of their organization.
Ready to put your insights into action?
Take the next steps and contact our team today.
