The Dragos Threat Intelligence team presented at the RSAC security conference in San Francisco on 26 February 2020. Dragos’ Director of Intelligence Analysis Amy Bejtlich and Cyber Threat Intelligence Analyst Selena Larson presented an open source intelligence (OSINT) primer and described types of information an adversary may target to develop a cyberattack against an ICS-related entity. OSINT is a valuable asset for attackers in the early stages of attack development because this information can enable the development of targeting strategies, initial access opportunities, or develop actions on objectives within the operations environment.
Fundamentally, OSINT is legally collected and publicly available information that informs investigations, reporting, cyberattacks, and defense. It largely aligns with the reconnaissance phase of the ICS Cyber Kill Chain, though the information gathered in this phase can enable further Stage 1 and Stage 2 activities.
Some common sources of OSINT include job listings, social media websites, search engines, news websites, vendor sites, legal resources like financial or court documents, and reconnaissance tools like VirusTotal.
Whether approaching OSINT collection from a defender or attacker perspective, the process remains the same. One must identify sources of information from a variety of publicly available datasets and the information must be collected and processed to identify how to incorporate it into an attack or defense framework. The data must be analyzed to determine the value of the information and operational effectiveness. A report is delivered to relevant stakeholders describing this process and to determine how to take action.
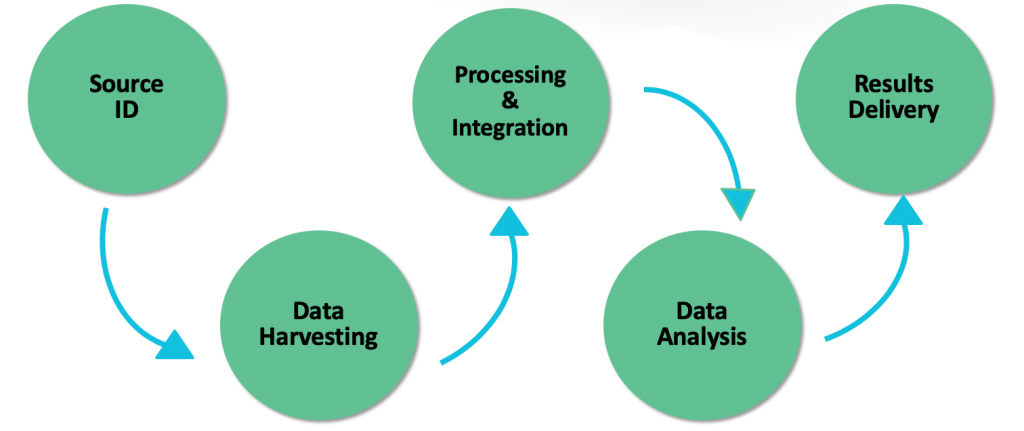
Figure 1: Flow of OSINT Collection and Reporting
Information an adversary might target includes:
- personal information such as a LinkedIn profile,
- critical information that informs an adversary of an attack’s impact on a target’s business or operations,
- accessibility information that informs an adversary of the ability or method to access a target,
- recoverability information that shows how a target can recover from an attack,
- vulnerability information that informs an adversary if a target may be exploitable via publicly-known vulnerabilities,
- effect information that includes the amount of loss a target would have from an attack, and
- recognizability information that shows adversaries the ease of identifying targets for operational gain.
Bejtlich and Larson described OSINT types they found that could be operationalized by an adversary. This included 10-K financial data on a security devices manufacturer, system documentation for a New York-based utility, power plant details from a vendor website, details on a pharmaceutical company’s software and production devices, a third-party database containing sensitive RFP submission data, and open source government data provided by the Energy Information Administration. Multiple case studies were presented, including an activity group that targeted a western energy company and obtained information about generation and engineering and an example of adversaries leveraging LinkedIn phishing campaigns to target employees in the oil and gas and mining industries.
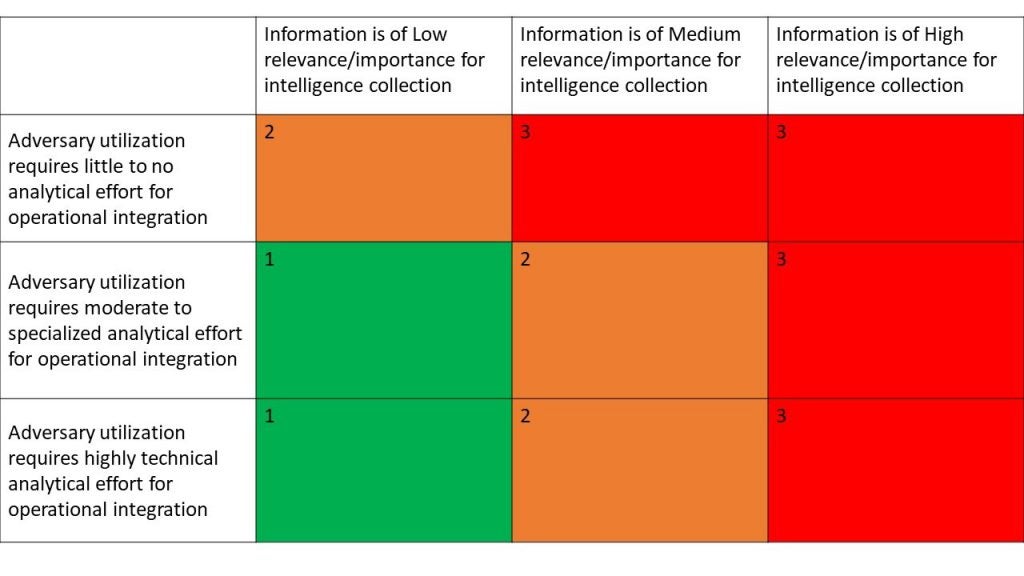
Dragos provided an OSINT Collection Risk and Vulnerability Matrix, created by Senior Adversary Hunter Casey Brooks, that is designed to help defenders scope and assess the value of open source data to an adversary.
Bejtlich and Larson wrapped up the discussion with some recommendations:
- Conduct regular OSINT assessments.
- Identify and limit information available about vendors and partners; documents, schematics, data sheets; job advertisements; credentials in public dumps; and gaps in security architecture.
- Implement authentication gateways to sensitive documents.
- Mandate multifactor authentication and user awareness.
- Document and assess OSINT value to an adversary.
Ready to put your insights into action?
Take the next steps and contact our team today.