This blog is a summarized version of Dragos’s whitepaper, “Improving OT Defense and Response with Consequence-Driven ICS Cybersecurity Scoping,” that can be read here.
As information technology (IT) technologies further integrate into industrial control system (ICS) environments, the increased cyber attack surface has enabled attackers’ ability to cause:
- operational disruptions
- financial damage
- potential impact to human safety
In the new age where tailored cyber attacks specific to the environment are a reality (e.g., TRISIS, the first malware designed to attack safety instrumented systems), defenders must prioritize ICS security strategies to combat ICS-specific attackers.
What is a Cyber Attacker’s Objective?
An attacker’s objective is to identify crown jewels (highest-valued assets that, if compromised, could cause major impact to the organization) and manipulate their normal functions to disrupt the systems’ operations. An attacker’s desired system state takes into account the human element of process control and operator responses to process upsets. A determined attacker will attempt to mitigate the effectiveness of an operator and the pre-configured logical responses to variable states.
How Can Analysts Combat an Attacker’s Objective?
To prepare for and combat attackers, industrial organizations must implement a risk model that prioritizes their ICS crown jewels and understands the attacker’s perspective. Prioritizing crown jewels allows for accurate scoping of ICS security strategies, tailored threat hunting, and performing assessments that analyze and evaluate their overall ICS security postures while keeping malicious actors at the forefront of strategy.
Dragos’ consequence-driven model of identifying ICS crown jewels is an easily applied and repeatable scoping model that helps organizations visualize how an attacker would assess a system to achieve a specific consequence–enabling security analysts to identify starting points for cyber threat hunts, incident response planning, penetration/vulnerability assessments, and cyber security strategies for their ICS environments.
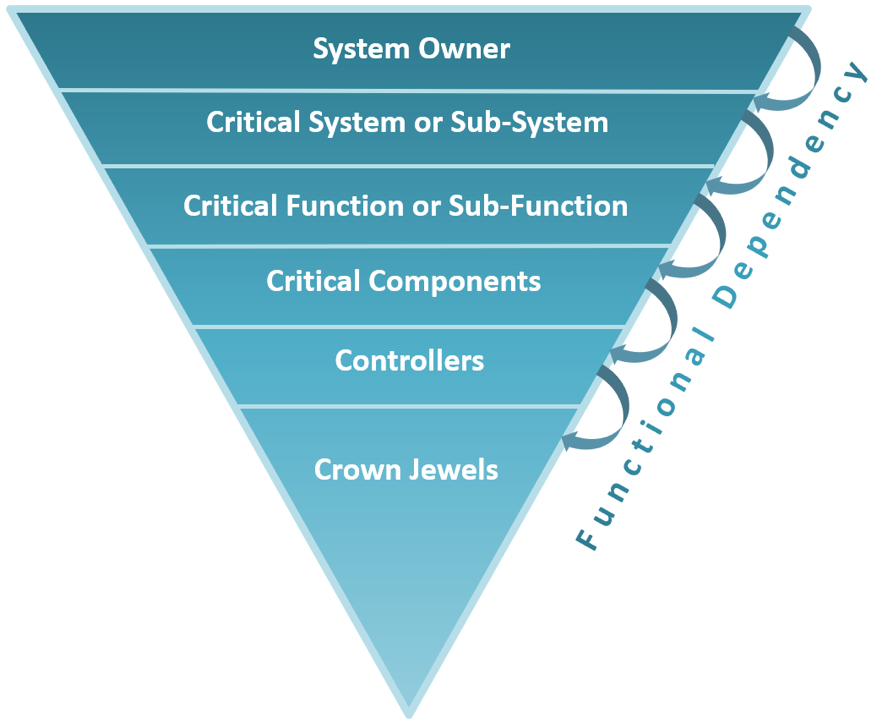
Dragos Crown Jewel Analysis Model
Understanding Each Layer
At each layer, the element(s) contributing most to functional output (primary purpose), functional dependencies (reliance on other systems to fulfill functional output), and level of exposure must be analyzed and understood before progressing to a lower layer.
- Layer 1, System Owner: specific provider within an industry discipline, geographic region, or demographic that may be targeted
- Layer 2, Critical System or Sub-System: collection of assets, facilities, networks, and/or operators that provide a specific, collective function and output (these determine your starting position within the organization)
- Layer 3, Critical Function or Sub-Function: required principal tasks of a system such as heating, cooling, exchanging, pumping, separating, compressing, distributing, storing, etc.
- Layer 4, Critical Components: physical asset required to complete a system critical function (e.g., pumps, valves, motors, piping, suction screens, inlets, etc.)
- Layer 5, Crown Jewels: critical data, logical assets, communication paths, and/or control interfaces required to exercise control over components, and thus, functions (including HMIs, engineering and operator workstations, gateways, controllers, etc.)
For effective ICS cybersecurity strategies, organizations must have well-planned and informed requirements for the protection of their operational environments from cyber attacks–which begins with identifying and prioritizing what must be protected. Progressing through the Dragos’ Consequence-Driven Crown Jewel Analysis Model allows industrial organizations to work from the starting point of identified risks to processes, much in the same way cyber attackers assess the feasibility of affecting system functions–thereby taking into account the attacker’s perspective, anticipating their desired outcome, and preparing defensive strategies to combat them.
Ready to put your insights into action?
Take the next steps and contact our team today.