This week, news broke that hackers successfully infiltrated the network of a nuclear power plant in India. Dragos investigated this event over the last few days, and here is what we know so far.
Several social media posts indicated a potential compromise of an Indian nuclear power station taking place between early September and late October 2019. On October 30 the Nuclear Power Corporation of India Limited (NPCIL) confirmed a malware infection and said the infected computer was on the administrative network. This network, NPCIL officials said, was isolated from the “critical internal network.” According to NPCIL, the Indian Computer Emergency Response team alerted officials to the compromise on September 4.
The initial social media post on October 28 describing the infection said an unnamed adversary obtained domain controller access at the Kudankulam Nuclear Power Plant (KKNPP) in Tamil Nadu. Domain controllers are responsible for authentication and user authorization within an entity’s entire domain. Domain controllers essentially serve as a gatekeeper and map of the network. With access to this crucial part of the network attackers can steal data and make changes to a target system. While it is possible that the adversary achieved domain controller access during this event, insufficient evidence exists to indicate this occurred, and such compromise is not necessary to execute the commands observed within available malware samples.
Dragos identified five samples that appear to be related to the infection events that function as payloads or droppers for a remote access tool (RAT). The samples align with malware known as DTrack, a RAT that can be used to steal data and enable control over an infected system. Researchers first disclosed DTrack in late September 2019, and identified the tool targeting Indian financial institutions and research centers. DTrack is loosely connected to an earlier observed malware family, ATMDTrack, used for robbing ATM machines.
The samples Dragos identified were slightly different from past DTrack variants. Our investigation confirms a targeted intrusion toward the NPCIL and KNPP based on the malware containing hard-coded private IP addresses and specific credentials relating to the facility. The analysis indicated remote access capabilities specific to the target environment. The image below includes malware code snippets of file movement commands using known credentials and system commands including a private IP address. The “KKNPP” username provided in the malware sample aligns with the Indian nuclear power plant.
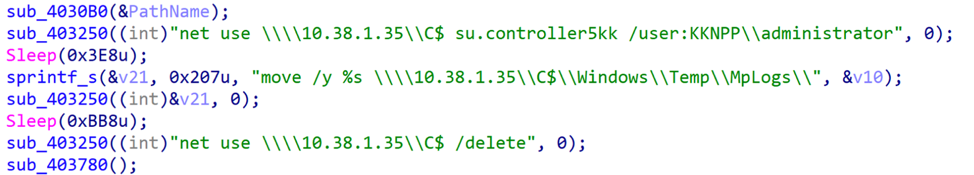
Figure 1: Code snippets of malware sample including known credentials (user:KKNPP)
The identified malware has no ICS-specific components which would interact with any control system. At this time, there is no indication attackers successfully compromised the networks responsible for control and operation of sensitive processes in the operations (OT) network. All reasonable analysis suggests no nuclear operations or safety breach occurred as a result of this infection.
The successful breach of IT as opposed to OT is an important distinction: if properly segmented, malware only impacting enterprise or administration at a nuclear facility would not enable an adversary to manipulate plant operations. Successful cyberattacks at nuclear power plants are some of the most difficult attacks to achieve and a variety of safety-focused physical and digital controls have contributed to environments that naturally lend to more cybersecurity.
In well-architected industrial networks, safety critical systems are restricted from other networks and control networks are connected to a demilitarized zone (DMZ) which acts as a secure subnetwork and buffer zone between operations and enterprise networks through which all traffic between them must be authorized to bypass.
The successful compromise of a nuclear power facility is concerning, and Dragos will continue to monitor the incident and associated infrastructure and attack behaviors. However, at this time there is no indication this specific event led to or could have caused a disruptive or destructive event within ICS.
Ready to put your insights into action?
Take the next steps and contact our team today.