In 2022, breakthrough evolution in the development of malware targeting industrial control systems (ICS), scaled ransomware attacks against manufacturing, and geopolitical tensions brought increased attention to the industrial cyber threat landscape. As in previous years, the ICS/OT community has managed a growing number of vulnerabilities, many without the right mitigations needed to reduce risk and maintain operations. Meanwhile electric grids, oil and gas pipelines, water systems, and manufacturing plants continued to struggle with more complex regulatory environments that demand marked progress in shoring up defenses.
The 2022 Dragos ICS/OT Cybersecurity Year in Review provides an on-the-ground understanding of what is happening in the industrial space. The sixth edition of Dragos’s comprehensive report contains the latest threat intelligence on adversary activity targeting operational technology (OT) and recent ICS-specific malware discoveries, data to inform vulnerability management practices, and cybersecurity benchmarks for industries.
Download the 2023 OT Cybersecurity Year in Review Report
The 2023 OT Cybersecurity Year in Review report provides a panoramic view of the most significant cyber trends, threats, and lessons learned during cybersecurity events from the past year.
Get Your Free Copy!PIPEDREAM, the Seventh ICS-Specific Malware
PIPEDREAM is the seventh known ICS-specific malware, following STUXNET, HAVEX, BLACKENERGY2, CRASHOVERRIDE, TRISIS, and Industroyer2. It has the potential for disruptive and destructive cyber attacks. Dragos and our third-party partners discovered and analyzed its capabilities before it was employed. In present form, adversaries could leverage PIPEDREAM to target equipment in multiple sectors and industries. Given the modular nature of PIPEDREAM, adversaries could adapt the malware capabilities to compromise and disrupt a broader set of targets in the future.
PIPEDREAM is the first scalable, cross-industry ICS attack framework. It targets three ubiquitous software components and demonstrates the risks of modern component-based software supply chains where single exploits and vulnerabilities have the potential for sweeping cross-industry impact.
Maintaining an accurate asset inventory and threat detections based on knowledge of real industrial adversary behaviors as part of an ICS Network Visibility program makes it easier to spot destructive threats like PIPEDREAM. It is therefore concerning that a full 80 percent of Dragos service engagements still lack visibility across OT networks – making detections, triage, and response incredibly difficult at scale. Monitoring East-West ICS networks with ICS-protocol aware technologies is necessary to spot PIPEDREAM in your ICS/OT environments.
Two New Threat Groups Discovered
Dragos identified two new ICS Threat Groups targeting industrial control systems and operational technology in 2022: CHERNOVITE and BENTONITE. Both threat groups demonstrate sophistication and adaptability, and one group is the developer of malware capabilities that achieve Stage 2 of the ICS Cyber Kill Chain and execute an ICS attack.
CHERNOVITE
- The CHERNOVITE Threat Group is the developer of PIPEDREAM, the seventh ICS-specific malware and a modular cross-industry toolkit. To develop PIPEDREAM, CHERNOVITE demonstrated a not yet seen before breadth of knowledge of ICS protocols and intrusion techniques available to produce an effect in OT environments. Dragos assesses with high confidence that CHERNOVITE is highly motivated, well-funded, and skilled in software development methods. CHERNOVITE has developed the capabilities to achieve Stage 2 of the ICS Cyber Kill Chain and execute an ICS attack.
BENTONITE
- BENTONITE is a new threat group increasingly and opportunistically targeting maritime oil and gas (ONG); ,state, local, tribal, and territorial (SLTT) governments; and, manufacturing sectors since 2021. BENTONITE conducts offensive operations for espionage and disruptive purposes, targeting vulnerabilities in internet-exposed assets to facilitate access.
Threat Group Updates
The 2022 Dragos ICS/OT Cybersecurity Year in Review includes findings from Dragos threat hunters on the activity of six known ICS Threat Groups targeting industrial organizations.
- KOSTOVITE – Targets energy in North America and Australia
- KAMACITE – Targets many industrial sectors in Europe, including Ukraine, and the U.S.
- XENOTIME – Targets oil and gas, electric in the Middle East and North America
- ELECTRUM – Targets electric in Europe, including Ukraine
- ERYTHRITE – Targets multiple industrial sectors in the U.S and Canada
- WASSONITE – Targets multiple industrial sectors in South/East Asia and North America
The techniques used by threat groups to gain initial access signal the importance of having Secure Remote Access in ICS/OT environments, and yet 44 percent of service engagements included a finding about shared credentials in OT systems, the most common method of lateral movement and privilege escalations. Where multi-factor authentication (MFA) is not possible, consider alternate controls such as jumphosts with focused monitoring on connections in and out of OT networks.
Industrial Risk of Ransomware
Ransomware is cited as the top financial and operational risks to industrial organizations. Out of the 57 ransomware groups targeting industrial organizations and infrastructures, Dragos observed, through public incidents, network telemetry, and dark web resources, that only 39 groups were active in 2022. Dragos identified 605 ransomware attacks against industrial organizations in 2022, an increase of 87 percent over last year. Manufacturing claimed the highest share, a staggering 72 percent, but ransomware attacks spanned many industries, including food and beverage, energy, pharmaceuticals, oil and gas, water, mining, and metals.
Ransomware represents a top cyber risk to industrial organizations, particularly those without a Defensible Architecture. OT security strategies often start with hardening the environment—removing extraneous OT network access points and maintaining strong policy control at IT/OT interface points. Dragos service engagements included a finding about improper network segmentation in 50 percent of cases and a finding of external connections from OEMs, IT networks, or the Internet to the OT network in 53 percent, showing there is still a long way to go to defend against ransomware risks.
The State of ICS/OT Vulnerabilities
In 2022, the number of reported ICS/OT vulnerabilities showed a material increase of 27 percent, which demonstrates the increased attention and focus on the risks to industrial infrastructure by security researchers. The Dragos Threat Intelligence team analyzed 2170 common vulnerabilities and exposures (CVEs) during 2022, up from 1703 CVEs in 2021.
While patching an IT system like a worker’s laptop is relatively easy, shutting down a plant has huge costs. Knowing what to do and when to do with vulnerabilities is a critical component of an effective Risk-Based Vulnerability Management program.
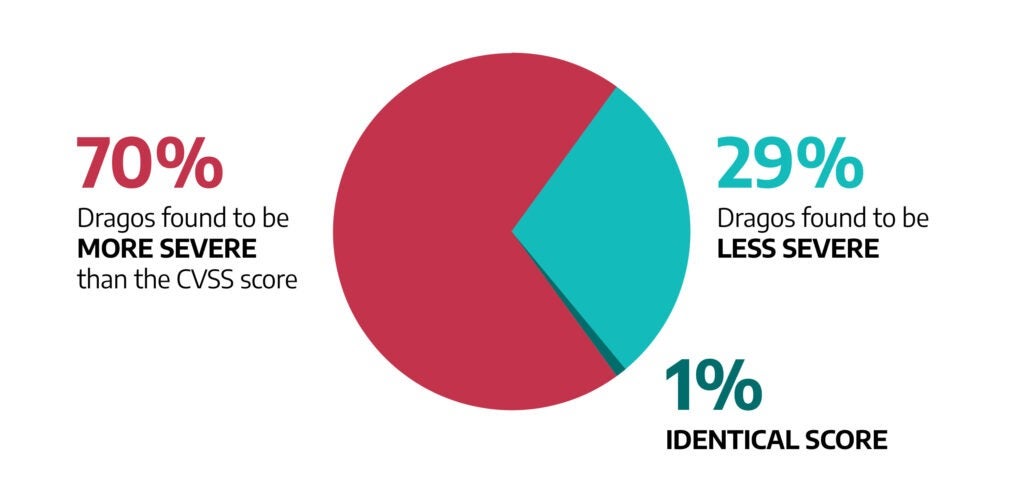
For each CVE, Dragos independently assesses, confirms, and provides corrections to help with prioritizing vulnerabilities and implementing mitigations that reduce risk and maintain operations in ICS/OT environments.
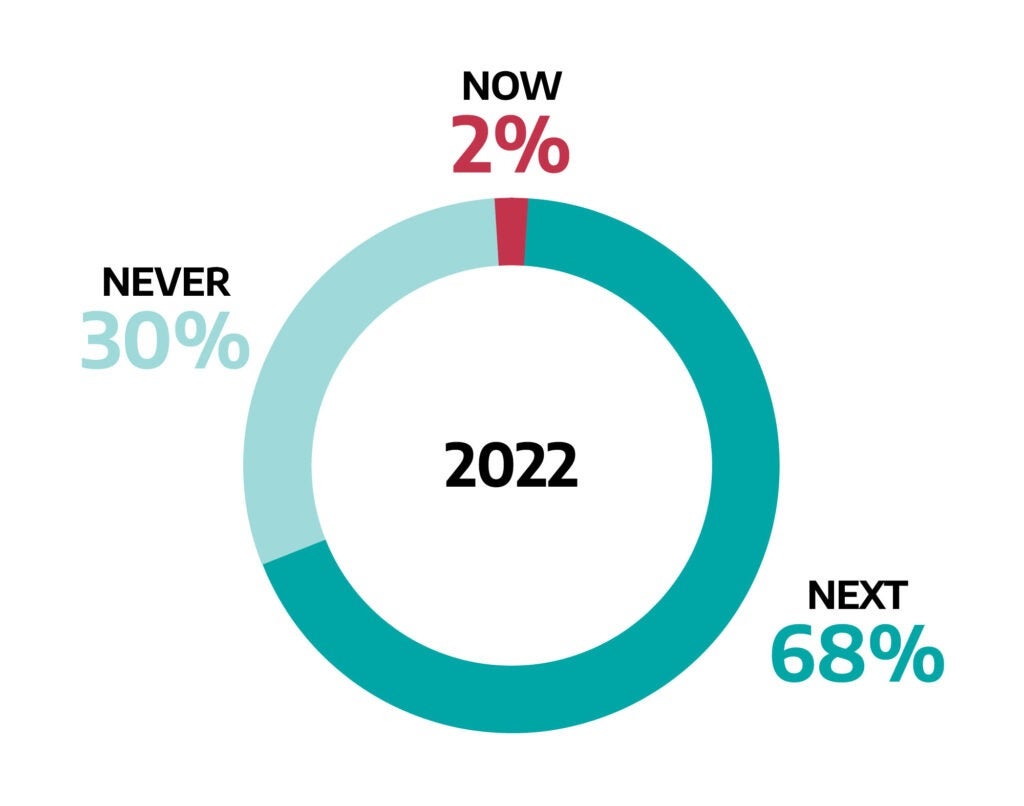
Acting Now, Next, Never
Dragos researchers assess vulnerabilities to account for how easily and frequently they are exploited by adversaries and how impactful a compromise could be in the context of ICS/OT environments. Dragos categorizes them by Now, Next, and Never to help avoid wasting resources on unnecessary remediation and focus OT asset owners and defenders toward their most critical risks.
Be proactive about having a well-thought-out ICS-Specific Incident Response plan (IRP) that is distinct from IT’s. OT involves different devices, communication protocols, adversary behaviors, and vulnerability management practices. Cyber attacks can result in physical impacts and investigations require a different set of tools. Create a dedicated plan that includes the right points of contact and next steps for specific scenarios at specific locations.
Lessons Learned from the Frontlines
For the last six years, Dragos has leveraged our Professional Services team to develop an on-the-ground understanding of the realities facing the industrial community and to bring back insights and lessons learned from the field. Dragos reports to four key findings that we continue to track year over year since 2019.
- 80 percent of Dragos services engagements had limited to no visibility into their ICS/OT environment, showing no significant change from 2019.
- 50 percent of services engagements identified issues with network segmentation with poor security perimeters, a 27 percent decrease over the previous year.
- Dragos engagement that included findings of external connections to OT in 2022 dropped significantly from 70 percent to 53 percent.
- 54 percent of Dragos services engagements included findings related to shared credentials, up from 44 percent in 2021.
Impact of Oil & Gas Pipeline Regulations
Over the last year, the U.S. Transportation Security Administration (TSA) worked with pipeline owners and operators to understand how they could revise Pipeline-2021-02B to better meet the goal of improving the overall cybersecurity resilience of pipeline organizations.
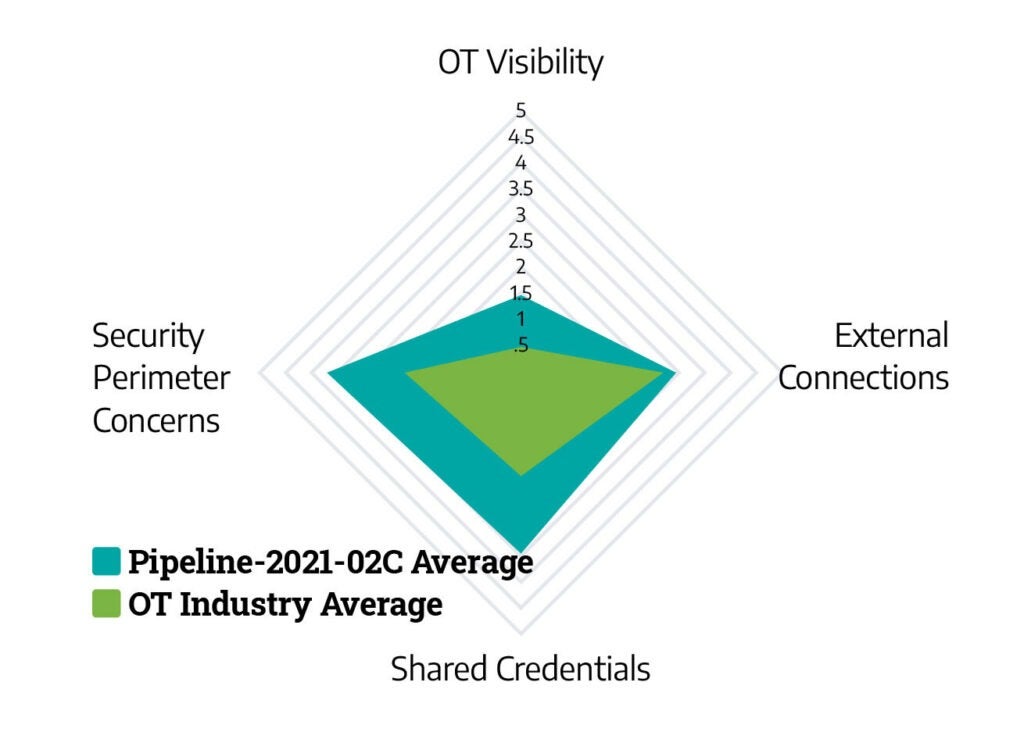
Pipeline-2021-02C contains many of the same requirements as Pipeline-2021-02B, including the need for a cybersecurity assessment program. Dragos was able to compare common findings and trends of those within scope of Pipeline-2021-02C and the OT industry overall, and the results are promising.
Download the Full Report
The Dragos 2022 ICS/OT Cybersecurity Year in Review report will help you identify your critical industrial threats, prioritize vulnerabilities, and improve your ICS/OT cybersecurity posture with year-over-year data and insights.

See Our Latest Year in Review
Ready to put your insights into action?
Take the next steps and contact our team today.