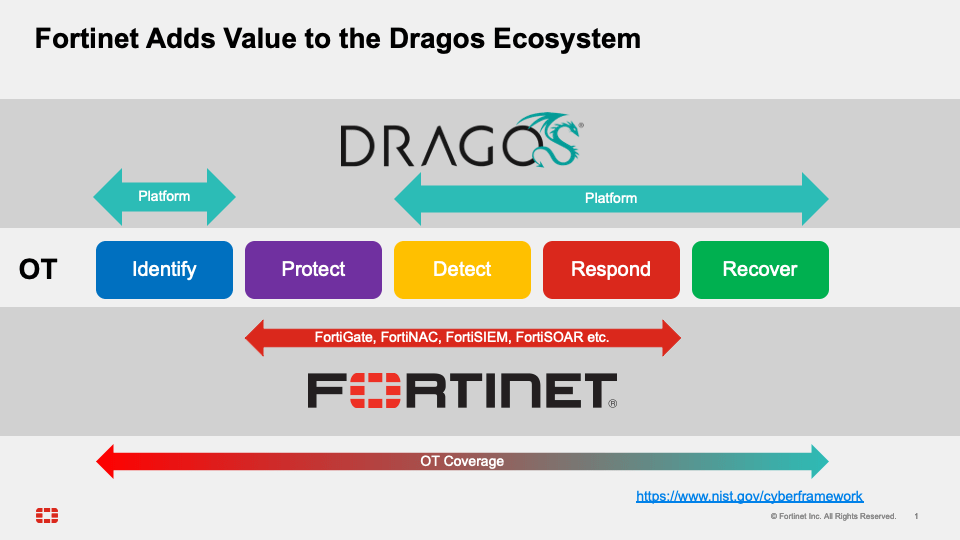
Dragos and Fortinet partner to offer an OT cybersecurity solution that enhances visibility, improves cyber event correlation, and enforces policies with actionable responses. This partnership empowers customers to make more informed decisions when implementing segmentation and preventative controls.
Key Takeaways from Fortinet’s 2024 OT Cybersecurity Report
The convergence of Information Technology (IT) and Operational Technology (OT) has brought new cybersecurity challenges. Fortinet’s “2024 State of Operational Technology and Cybersecurity” report reveals crucial insights into this evolving landscape.
Listen to Key Insights from Fortinet's 2024 Report
Dragos VP of Global Business Development, Matt Cowell, recently joined Richard Springer, Director of OT Product Marketing at Fortinet, on a webinar to explore the key takeaways of this comprehensive report. Check it out!
Watch the WebinarIncreased Number of Cyber Incidents
- 31% of organizations faced 6+ intrusions in the past year (up from 11%)
- Ransomware attacks on industrial organizations increased by 50%
Changing Threat Landscape
- Phishing emails remain the top threat (76% of organizations affected)
- Business email compromise affects 65% of respondents
- Ransomware and wiper attacks jumped from 32% to 56%
Shifting OT Security Responsibilities
- More CISOs now oversee OT security (27% in 2024, up from 17%)
- VP/Directors of Networking Engineering/Operations increasingly manage OT cybersecurity
- These findings indicate that OT security is becoming a higher-priority issue at an executive level
Maturing Security Postures
- 20% of organizations have basic visibility and segmentation (up from 13%)
- 23% use advanced orchestration and automation (up from 13%)
- Organizations are increasingly measuring success based on their ability to respond to and recover from incidents
- The top success metric reported was “response time to security incidents/return-to-service time,” highlighting a shift towards cyber resilience
Persistent Visibility Challenges
- Only 5% claim 100% visibility of OT systems (down from 10%)
- This could indicate a more realistic assessment of their current asset visibility
Growing Impact of Cyber Intrusions
- 52% reported brand awareness degradation
- 55% experienced operational outages
- 43% suffered loss of critical data or intellectual property
Dragos Year in Review: Additional Insights, Similar Trends
See the Dragos OT Cybersecurity Year in Review annual report for more insights on cybersecurity trends affecting industrial organizations.
- 70% of ransomware attacks targeted manufacturing
- 21 unique threat groups identified, including three new ones
- 54% of penetration tests found remote access security issues
- 28% of engagements revealed segmentation or firewall configuration problems
- 70% of OT-related cyber incidents originate from IT environments
5 Recommendations to Improve OT Security
1 | Implement Comprehensive Asset Inventory
- Deploy the Dragos Platform for automated asset inventory of IT, IoT, and IIoT devices on your OT network
- Non-invasive, passive-first monitoring protects operational uptime
2 | Enhance Threat Detection
- Use Dragos Platform’s intelligence-driven detection capabilities
- Stay protected against emerging threats and sophisticated attacks
3 | Implement OT-Specific Vulnerability Management
- Utilize Dragos Platform’s “Now, Next, Never” approach
- Reduce risk and minimize downtime with OT-enriched vulnerability management
4 | Strengthen Incident Response
- Leverage Dragos Platform’s expert-authored playbooks
- Improve response times and minimize breach impacts – tracking your improvements using tabletop exercises
5 | Leverage Collective Intelligence
- Join Dragos Neighborhood Keeper program
- Benefit from anonymously shared intelligence across industries
Fortinet and Dragos Partnership Benefits
Discover more about the Fortinet and Dragos OT cybersecurity solution.
Integrated Security Solution
- FortiGate NGFW integrates with the Dragos Platform
- Offers asset visibility, inventory management, and threat detection
Simplified Deployment
- Addresses challenges in selecting optimal cybersecurity technologies
Enhanced Workflow Automation
- Improves efficiency and response time for security analysts
- Enables human-in-the-loop for effective incident response
Hear from Our Experts
Ready to put your insights into action?
Take the next steps and contact our team today.