In the fourth quarter (October to December) of 2024, the ransomware threat landscape presented an increasingly dynamic ecosystem, with multiple ransomware groups refining their techniques, expanding their capabilities, and forming new alliances, ultimately intensifying attacks on industrial organizations.
Adversaries consistently exploited newly disclosed vulnerabilities in critical technologies such as Veeam Backup & Replication and Cleo Managed File Transfer (MFT) solutions, enabling them to gain rapid initial access or inflict high-impact disruptions. Social engineering remained a common initial access vector, allowing attackers to bypass perimeter defenses and establish footholds in industrial environments. Notably, collaborations between financially motivated operators and nation-state affiliates further blurred the lines between cybercrime and geopolitics. They contributed to an uptick in sophisticated ransomware incidents across water treatment, energy distribution, and manufacturing.
Throughout Q4 2024, newly branded or rebranded ransomware groups proliferated. Several leveraged leaked source code or formed partnerships with established adversaries, rapidly adopting advanced tactics, techniques, and procedures (TTPs). In addition, many public resources indicated that nation-state adversaries openly aligned with ransomware operators, obscuring distinctions between financially driven and geopolitically oriented attacks. Collectively, these developments underscore a convergence of operational and strategic interests, resulting in increased theft of sensitive industrial data and both intended and unintended disruptions to industrial operations, ultimately causing prolonged downtime, safety risks, and financial losses for affected organizations. Therefore, Dragos assesses with low confidence that ransomware groups operating under the ransomware-as-a-service (RaaS) model create opportunities for financially, ideologically, or politically motivated adversaries to advance espionage, sabotage, and financial objectives. By leveraging these platforms, adversaries minimize detection and maintain operational continuity, complicating the efforts of law enforcement agencies to identify and impose sanctions.
During Q4 2024, Dragos did not identify any new ransomware variants specifically tailored to industrial control systems (ICS) environments. ransomware adversaries continue to cause various operational impacts on industrial organizations as manufacturing plants, water treatment facilities, and energy providers witnessed forced production halts, manual failovers, or supply chain interruptions from ransomware-induced shutdowns. In many cases, significant portions of the victim’s IT infrastructure had to be taken offline to prevent further damage, directly affecting OT processes and causing substantial disruptions.
During this quarter, Dragos observed the expansion of established ransomware groups and the emergence of new or rebranded operators focused on industrial environments. Adversaries frequently exploited VPN appliances, firewall firmware, and backup management solutions to secure initial access, underscoring a continued reliance on low-barrier intrusion points. Ransomware operators demonstrated proficiency in targeting Windows, Linux, and ESXi systems and leveraged cloud-centric extortion methods to exfiltrate data and coerce victims. Although Dragos has not yet observed cloud-centric tactics directly impacting ICS, ransomware groups’ growing adoption of legitimate cloud services signals a shift that could further complicate detection and incident response in operational settings.
Register for the OT/ICS Cybersecurity Executive Briefing on February 27th, where Dragos CEO Robert M. Lee presents the findings from our 8th Annual Year in Review report.
Sign Up Today!Emerging Ransomware Groups and Activity in Q4 2024
Dragos’s Q4 2024 analysis highlights the emergence and rebranding of several relatively new, self-proclaimed RaaS groups, of which only limited publicly available information exists. By correlating TTPs, affiliate associations, and declared motivations, whether financial or ideological, Dragos has observed that multiple ransomware groups are leveraging leaked source code, such as LockBit, and tapping into established affiliate networks. While some represent opportunistic offshoots of existing operations, others demonstrate rapid technical maturity, selectively targeting industrial organizations and healthcare services known for having a low tolerance for downtime.
BianLian and RansomHub
BianLian continued evolving from traditional file encryption toward data extortion-centric attacks while simultaneously forging alliances with RansomHub. This collaboration illustrates how smaller or disrupted groups pivot to more established RaaS platforms, heightening global activity and attacking volumes against industrial operations. As BianLian shifted to extortion-based tactics, RansomHub provided the necessary resources, such as advanced intrusion tooling to exploit vulnerabilities in VPN appliances and remote desktop services.
DragonForce and Interlock
DragonForce, an emerging RaaS platform focused on double extortion strategies in the manufacturing and transportation sectors, was willing to engage quickly with affiliates that possess specialized intrusion capabilities. Interlock, in contrast, made its mark by targeting FreeBSD systems within critical infrastructure environments, an uncommon but potentially damaging vector if left unaddressed. These efforts mirror a broader trend of adversaries bypassing standard Windows defenses to disrupt essential services.
Termite
Termite exemplifies how adversaries seeking to shorten development cycles and broaden their capabilities can leverage publicly leaked ransomware source code. Its advanced encryption routines and aggressive process termination capabilities pose heightened risks for manufacturing and downstream oil and gas industries. Notably, Dragos observed that Termite focused on supply chain-related enterprises, an increasingly valuable target for adversaries hoping to generate maximum operational disruption.
Key Operational Techniques and Tactics
Cloud-Centric Extortion
Dragos’s ongoing research shows an uptick in ransomware adversaries using cloud platforms to exfiltrate data before executing ransomware encryption. These adversaries frequently adopt Azure Storage Explorer and AWS S3 Transfer Acceleration, blending malicious activity with legitimate cloud traffic to evade detection. Although Dragos has not observed any OT-focused compromise resulting directly from these cloud-centric intrusion methods, adversaries who gain a foothold through such tactics can potentially escalate their attacks, impacting OT environments or critical IT systems that support industrial operations.
Living-Off-The-Land (LoTL) Techniques and Persistence
Multiple ransomware groups continued to leverage “living-off-the-land” (LoTL) techniques by utilizing built-in Windows binaries (e.g., certutil.exe, PowerShell) to side-load or memory-inject malicious code, evading typical signature-based detection approaches. Notably, BlackBasta used specially crafted QR codes embedded within Microsoft Teams messages to trick employees into downloading remote monitoring tools, thereby creating post-exploitation footholds (i.e., establishing persistent access that allows adversaries to continue moving laterally, gathering intelligence, and re-infecting systems even if the initial intrusion is detected).
Ransomware groups consistently aimed to retain long-term access within victim environments, even after addressing initial disruptions. Dragos observed an increasing trend among ransomware adversaries exploiting legitimate remote monitoring and management (RMM) tools (e.g., AnyDesk, Microsoft Quick Assist) to maintain footholds across segmented networks.
Ransomware Impacts on Industrial Organizations
In the fourth quarter of 2024, ransomware attacks continued to significantly disrupt industrial organizations, leading to operational halts, financial losses, and compromised data integrity. Notable incidents included:
Refinadora Costarricense de Petróleo (RECOPE)
- Date: November 2024
- Impact: RECOPE, Costa Rica’s state-owned energy provider, was forced to operate fully on manual processes after a ransomware attack disabled the digital systems supporting payment processing and fuel sales. Although no shortages or supply interruptions were reported, the loss of automated workflows markedly increased transaction times, caused personnel to rely on paper-based records, and remediation required assistance from external specialists.
Stoli Group
- Date: August 2024 (December 2024 Update)
- Impact: The beverage manufacturer Stoli Group experienced extensive IT infrastructure disruptions following a ransomware attack, eventually leading to bankruptcy filings for its U.S. subsidiaries. The incident rendered core systems, such as enterprise resource planning (ERP), forced employees to rely on manual data entry and undermined normal operations across Stoli’s global footprint. This large-scale change from digital workflows severely affected production schedules, supply chains, and overall financial performance.
Pittsburgh Regional Transit (PRT)
- Date: December 2024
- Impact: A ransomware attack delayed bus and rail services for hours across Pittsburgh, affecting thousands of daily commuters. The interruption to key scheduling and ticketing platforms caused extended wait times, forced route alterations, and limited travelers’ ability to purchase new tickets or refill transit cards.
Regional Impact Observations, Fourth Quarter of 2024
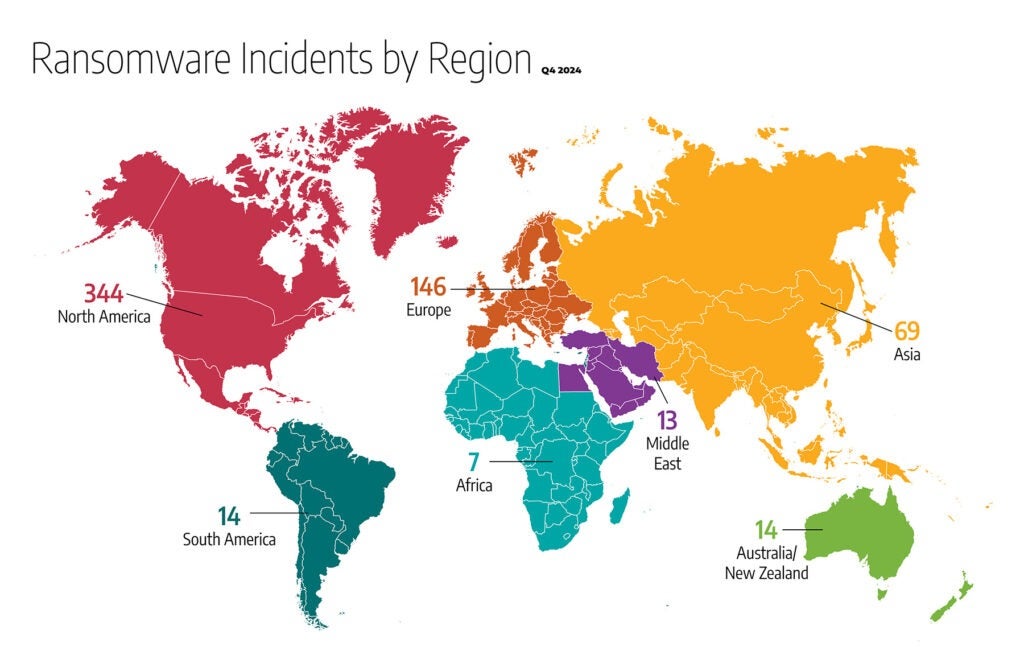
Ransomware incidents in the fourth quarter of 2024 continued to vary by region, with North America remaining the most frequently targeted area. As in previous quarters, the data demonstrates a global scope for ransomware threats, affecting diverse geographies and multiple sectors.
- North America: 308 reported incidents (approximately 51% of global ransomware activity). The United States accounted for most of these attacks.
- Europe: 168 incidents (approximately 28% of global ransomware activities). The United Kingdom, Germany, and Italy remained top targets, with attacks primarily affecting manufacturing and transportation.
- Asia: Approximately 70 incidents (about 12% of global ransomware activities).
- South America: 19 incidents (approximately 3% of global ransomware activity). Brazil registered most attacks in the region, with most operations focusing on food and beverage manufacturing and transportation systems.
- Middle East: 13 incidents, roughly 2–3% of global ransomware events.
- Oceania: 14 total incidents (nearly 2–3%). Australia and New Zealand were the primary targets.
- Africa: 7 incidents, representing under 2% of global incidents. South Africa and Tunisia accounted for the most reported attacks.
Industry Impacts, Fourth Quarter of 2024
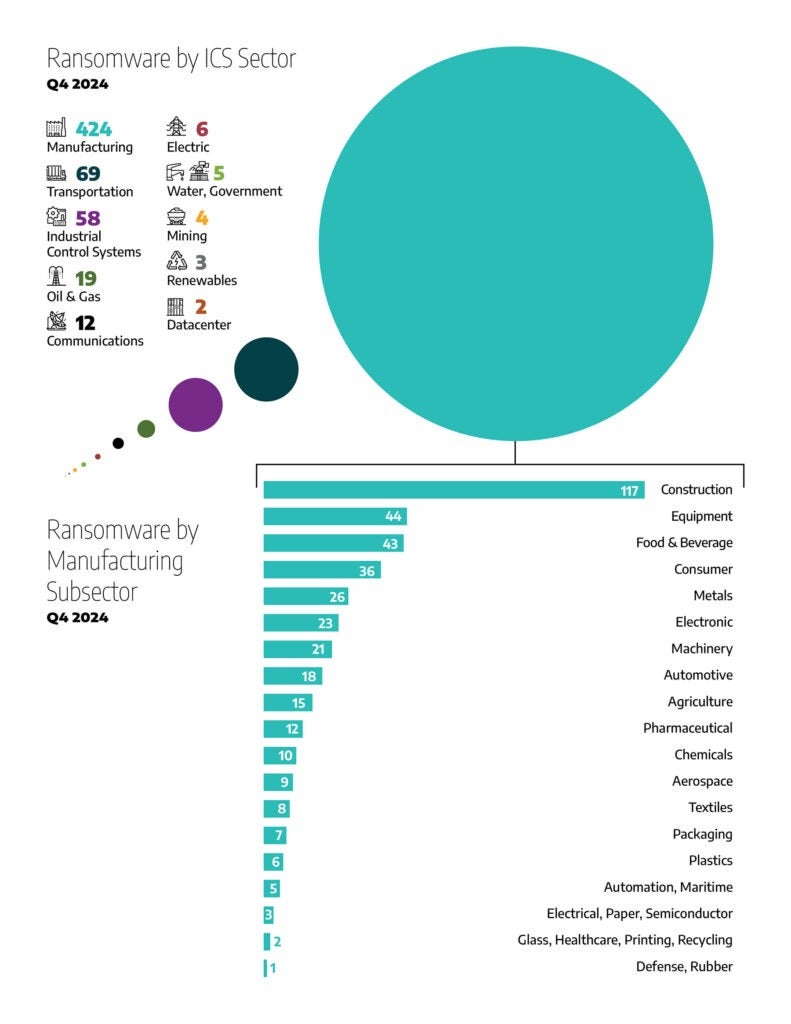
- The manufacturing sector remained the most impacted sector, with 424 observed incidents, accounting for 70% of all ransomware activity.
- Industrial control systems (ICS) equipment and engineering experienced 58 incidents, representing 10% of total activity.
- The transportation sector encountered 69 incidents (around 11%).
- Oil and natural gas (ONG) recorded 19 incidents (~3%).
- Government and water sectors each faced 5 incidents (~1% each).
- Mining reported 4 incidents.
- The renewables sector faced 3 incidents.
- Datacenters experienced 2 incidents.
In addition to these primary industries and sectors, Dragos observed ransomware activity affecting multiple subsectors within manufacturing (424 total incidents). The percentage breakdown, based on all manufacturing incidents, is as follows:
- Construction: 117 incidents (28% of manufacturing).
- Equipment: 44 incidents (10%).
- Food & beverage: 43 incidents (10%).
- Consumers: 36 incidents (8%).
- Metals: 26 incidents (6%).
- Electronics: 23 incidents (5%).
- Machinery: 21 incidents (5%).
- Automotive: 18 incidents (4%)
- Agriculture: 15 incidents (~4%).
- Pharma: 12 incidents (~3%).
- Chemicals: 10 incidents (~2%).
- Textiles: 8 incidents (~2%).
- Others (including Aerospace, Electrical, Automation, Packaging, Paper, Plastics, Defense, Printing, Recycling, Rubber, Semiconductor, Healthcare, Maritime, and Glass): The remaining percentage of manufacturing incidents is distributed in smaller numbers across these industries.
Ransomware Groups Trends, Patterns, and Observations During the Fourth Quarter of 2024
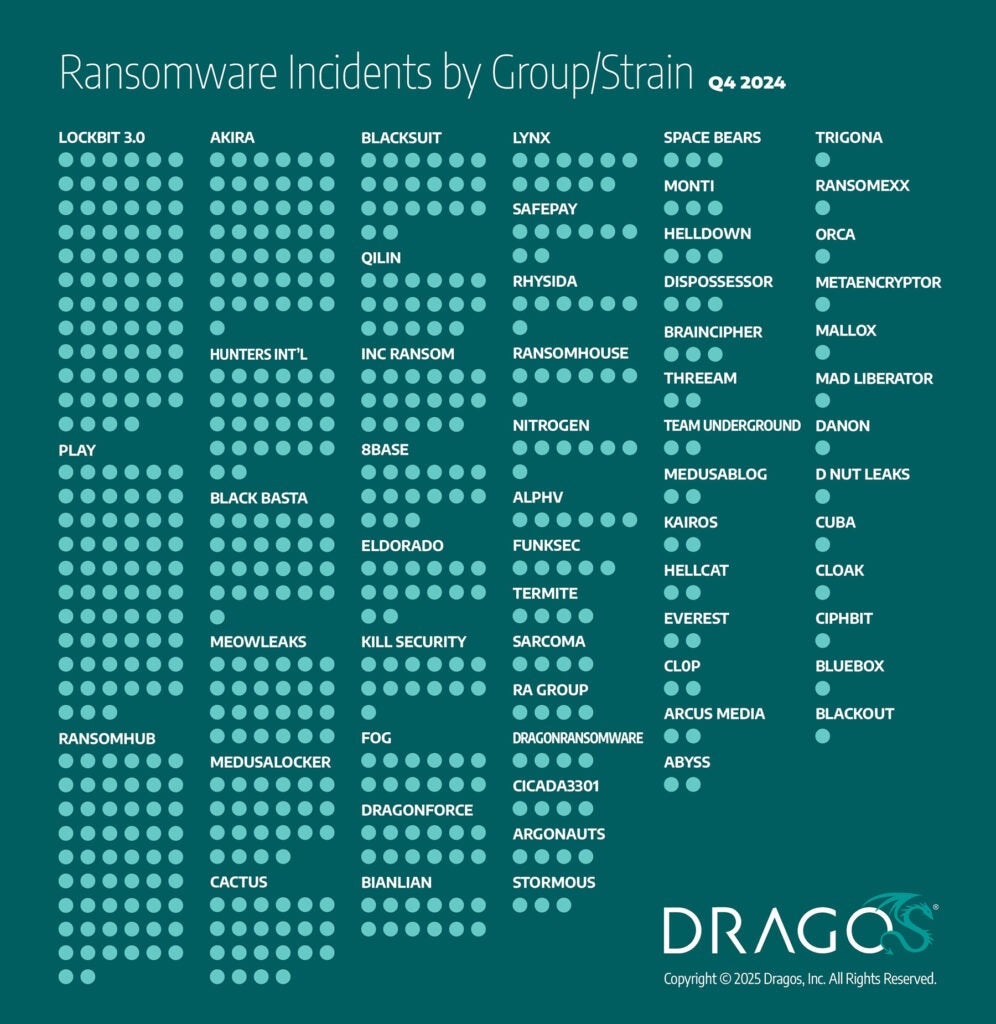
Dragos’s analysis of Q4 2024 ransomware activity indicates further fragmentation in the ecosystem. Several groups demonstrated notable prevalence:
- LockBit3.0: Accounted for 70 incidents (~12%), maintaining a high level of activity despite law enforcement disruptions earlier in 2024.
- Play: Linked to 63 incidents (~10%). The group continues to focus on critical infrastructure and industrial victims.
- RansomHub: Reported 56 incidents (~9%), an aggressive RaaS model attracting affiliates from disrupted operations; heavily targets industrial organizations.
- Akira: Accounted for 43 incidents (~7%), known for double extortion tactics and cross-platform expansions.
- Hunters International: Involved in 26 incidents (~4%), Dragos observed increased activities involving exploiting remote access vulnerabilities.
- BlackBasta: Linked to 25 incidents (~4%). The group continues to deploy sophisticated social engineering and RMM-based infiltration.
- MeowLeaks: 24 incidents (~4%) reported in the fourth quarter. Dragos a double extortion approach, which often emphasizes large-scale exfiltration of data to pressure victims into paying the ransom.
- MedusaLocker & Cactus: Involved in 22 incidents each (~4% each).
- BlackSuit: Accounted for 20 incidents, some of which caused operational impacts on water treatment and automotive suppliers.
- Qilin & Inc Ransom: 17 incidents each.
- 8Base: 15 incidents.
- Eldorado: 14 incidents.
- Kill Security (Killsec): 13 incidents.
- Fog, DragonForce, and BianLian: 12 incidents each.
- Lynx: 11 incidents.
- SafePay: 8 incidents.
- Rhysida, RansomHouse, Nitrogen: 7 incidents each.
- ALPHV: 6 incidents.
- FunkSec: 5 incidents.
- Termite, Sarcoma, RA Group, Dragon Ransomware, Cicada3301, and Argonauts: 4 incidents each
- Additional groups accounted for fewer than 4 incidents in Q4.
In Conclusion
During Q4 2024, ransomware groups shifted tactics and alliances at a rapid pace. Established operators such as RansomHub, LockBit3.0, and Play retained their dominance, while newly emerged or rebranded threats utilized modern infiltration methods and affiliate networks. Their focus on IT vulnerabilities, including unpatched VPN appliances, firewall firmware, and backup management solutions, led to operational disruptions in industrial environments. The industrial sector, particularly the manufacturing, transportation, and ICS equipment and engineering sectors, remained a primary target as adversaries employed advanced tactics and leveraged weaknesses in remote access solutions and credential practices.
Organizations should prioritize key cybersecurity measures such as enforcing multi-factor authentication (MFA), monitoring critical ports, maintaining offline backups, and strengthening remote access controls. In addition, enhanced personnel training and periodic network architecture reviews are vital for staying ahead of continually adapting ransomware techniques.
As the ransomware ecosystem continues to fragment and adapt, proactive defenses, threat intelligence sharing, and collaborative mitigation efforts will be essential to safeguarding critical infrastructure and industrial operations into the next quarter and beyond.
Download the 2025 OT/ICS Cybersecurity Report, our 8th Annual Year in Review, to get a complete view of the ransomware landscape in 2024.

Ready to put your insights into action?
Take the next steps and contact our team today.


