While international law enforcement’s relentless efforts have resulted in arrests and the dismantling of ransomware operations, the battle against ransomware groups continues unabated. During the fourth quarter of 2023, we witnessed a slight decline in reported incidents yet saw a surge in actions that kept the ransomware threat landscape dynamic.
Ransomware groups consistently adapt by evolving their strategies, embracing new techniques, and even reconfiguring or rebranding their operations to bolster their earnings and evade detection. Yet, international law enforcement has achieved noticeable results in fighting ransomware operations, including arresting members of ransomware groups, such as the arrest of a Ragnar Locker developer in Paris, and dismantling their infrastructure. Additionally, the U.S. Justice Department, in collaboration with international agencies including Germany, Denmark, and Europol, disrupted the activities of the AlphaV ransomware group. The U.S. Federal Bureau of Investigation’s (FBI) developed a decryption tool that aided over 500 victims, preventing approximately $68 million in ransom payments. This operation is part of a broader initiative to combat major ransomware operations and apprehend key figures involved in global cyber disruptions.
As ransomware groups have consistently demonstrated their capacity to innovate and refine their methods, active groups such as LockBit, BlackCat, Royal, and Akira adopted new techniques known as remote encryption or remote ransomware during the last quarter. This technique involves compromising an endpoint connected to the victim’s network and using it to launch the ransomware attack within the victim’s environment, thereby increasing the likelihood of a successful attack. As Dragos assessed with moderate confidence in last quarter’s blog, ransomware groups continue to prioritize zero-day vulnerabilities in their operations. This strategic focus was evident in the actions of the LockBit ransomware group as they exploited a vulnerability known as ‘Citrix Bleed’ (CVE-2023-4966) during their attacks. LockBit leveraged this flaw to hijack authenticated sessions, gaining temporary access to various targets, including Boeing’s parts and distribution business.
However, ransomware groups have expanded beyond technical innovations as they continue to adapt and refine their methods. They actively engage with the media to shape the narrative surrounding their activities, courting journalists, and providing press releases, FAQs, and interviews to manipulate public perception. This calculated approach allows ransomware gangs to amplify their notoriety and exert pressure on victims, ultimately enhancing their profitability. This evolving trend presents a fresh set of challenges for cybersecurity defenders and incident responders, who must incorporate effective communication strategies into their response plans to counter these cyber criminal tactics.
The threat landscape has also grown more complex due to ransomware groups’ willingness to collaborate. While these collaborations may not directly impact industrial sectors, they are a worrisome development. Notably, instances of collaboration among ransomware groups, such as BianLian, White Rabbit, and Mario Ransomware teaming up to target financial services firms, underscore a concerning trend of cyber criminal networks working together for mutual gain. This growing cooperation poses potential risks to critical infrastructure and industrial sectors as cyber criminals continue to share tactics, techniques, and potentially even vulnerabilities that could be leveraged in future attacks.
In the fourth quarter of 2023, Dragos’s assessment of increased business-impacting ransomware attacks against industrial organizations was validated, with incidents exhibiting more severe impacts when compared to earlier quarters. An example of this was the Lockbit attack in October 2023, which exploited the Citrix Bleed vulnerability, targeting Boeing’s core operations in parts and distribution. Furthermore, the Qilin ransomware group’s November cyberattack on Yanfeng, a Chinese automotive part company supplying interior components to global carmakers, disrupted operations to the extent that Stellantis had to halt production at its North American plants.
In addition, Dragos noticed other ransomware incidents that impacted the operations of multiple organizations, such as the following:
- Paris Wastewater Agency (SIAAP).
- The American apparel company VF Corporation.
- The MPM Medical Supply company.
Dragos analyzes ransomware variants used against industrial organizations worldwide and tracks ransomware information via public reports and information uploaded or appearing on dark websites. By their very nature, these sources report victims that were listed as targets and those that pay or otherwise “cooperate” with the criminals, and they do not necessarily match one-to-one with all incidents that took place in this last quarter.
Two interesting observations from the fourth quarter of 2023 compared to the previous quarters were observable decreases in active ransomware groups and ransomware incidents impacting industrial organizations. Specifically, of the 77 ransomware groups that have historically attacked industrial organizations and infrastructure, only 32 of the groups were active in the last quarter, and the number of ransomware incidents went from 231 to 204 over the same period. As of this blog, Dragos is uncertain about the cause of this decrease in ransomware incidents between the third and fourth quarters of 2023.
Although the number of ransomware incidents and dark web postings in the fourth quarter of 2023 was slightly less than in the third quarter of 2023, the overall impact of these ransomware attacks against industrial organizations remains significant.
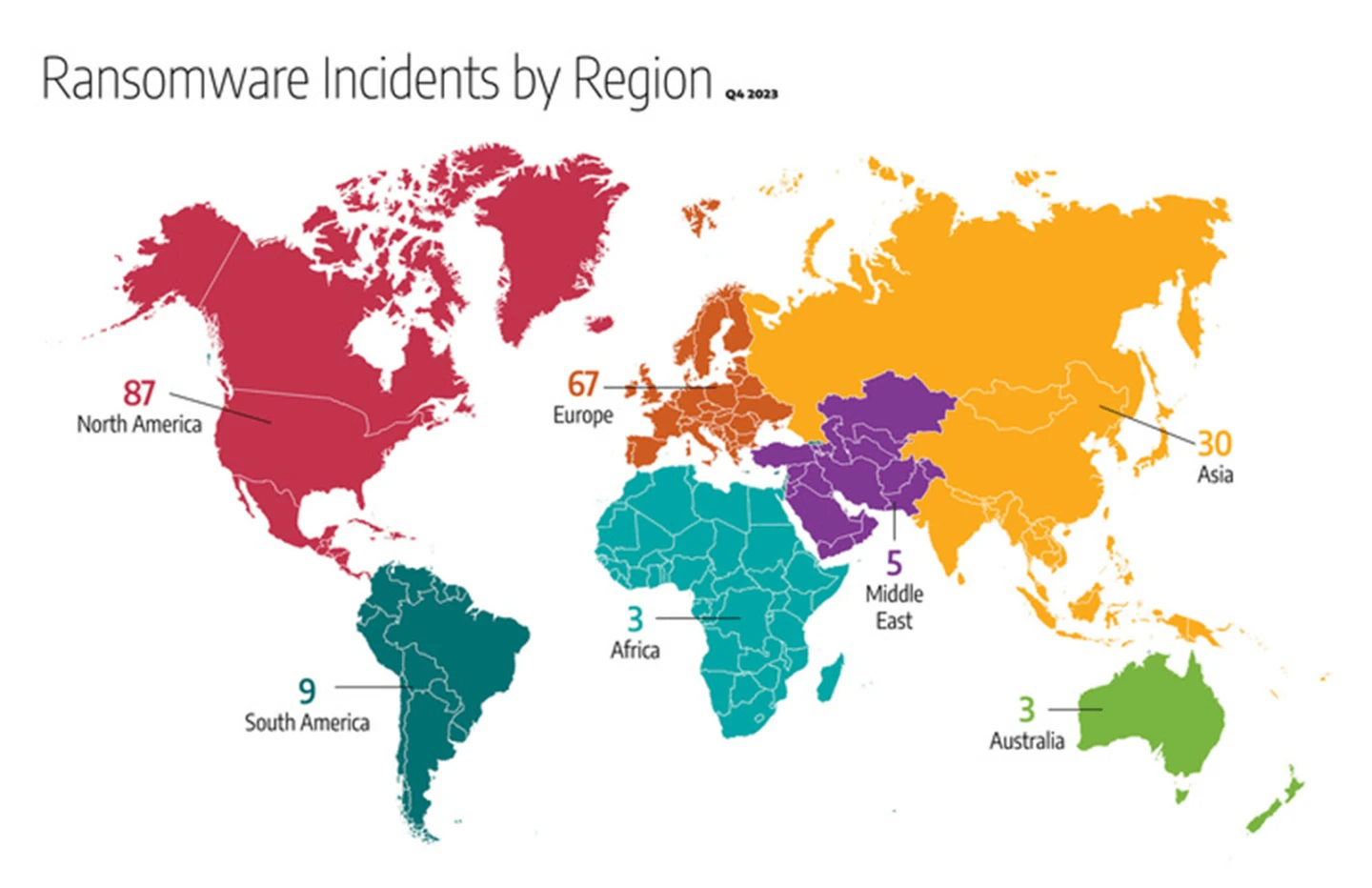
- There were 87 ransomware incidents (roughly 43 percent of the observed 204 global ransomware attacks) that impacted industrial organizations and infrastructure in North America, compared to 91 incidents in the previous quarter. Within North America, the U.S. received over 37 percent of all ransomware incidents, similar to last quarter.
- Approximately 32 percent of global ransomware incidents (67 in total) impacted Europe, roughly the same percentage as observed in Q3 2023.
- Asia is next with 14.4 percent, or 30 incidents.
- South America had 4.4 percent, totaling 9 incidents.
- The Middle East had 2.5 percent, totaling 5 incidents.
- Africa and Australia had 3 percent, totaling 3 incidents, each.
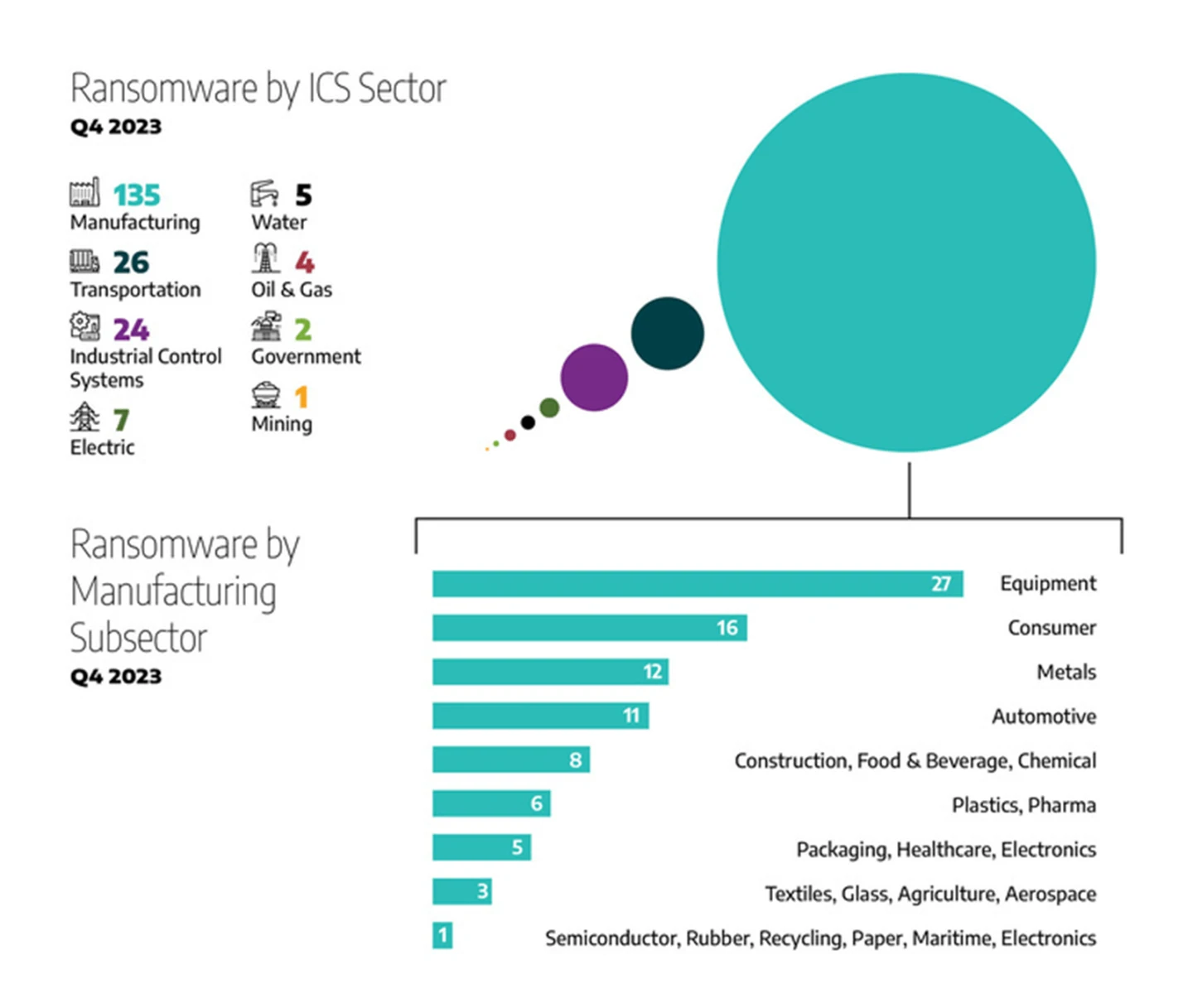
Manufacturing was the most impacted industry during the fourth quarter of 2023, with 135 observed incidents in total, or 66.1 percent. The breakdown by sector is as follows.
- The transportation sector was impacted 26 times, for a total of 12.7 percent of all observed incidents, which is a 50 percent increase compared to the previous sector.
- The industrial control systems (ICS) equipment and engineering sector had 11.7 percent of alleged attacks (24 incidents).
- The electric sector was impacted by 3.43 percent of the alleged attacks (7 incidents).
- The water and wastewater sector were the victim of 2.45 percent of alleged attacks (5 incidents).
- The oil and natural gas sector had 1.9 percent of alleged attacks (4 incidents).
- The mining and government sectors had less than one percent of the global alleged attacks each.
In addition to the primary industries and sectors mentioned above, Dragos observed 22 unique manufacturing sub-sectors impacted by ransomware during the fourth quarter of 2023. Their percentage breakdown as a part of all manufacturing incidents, follows:
- Equipment: 20 percent (27 incidents)
- Consumer: 12 percent (16 incidents)
- Metals: 9 percent (12 incidents)
- Automotive: 8.1 percent (11 incidents)
- Food and beverage, Contraction, and Chemical: 8 percent (6 incidents)
- Pharmaceuticals, Electronic, and plastic: 4.4 percent (6 incidents)
- Packaging and Healthcare: 3.7 percent (5 incidents)
- Aerospace, Glass, Agriculture, and Textile: 2.2 percent (3 incidents)
- Rubber, Maritime, Paper, Recycling, Rubber, and Semiconductor: less than one percent (1 incident)
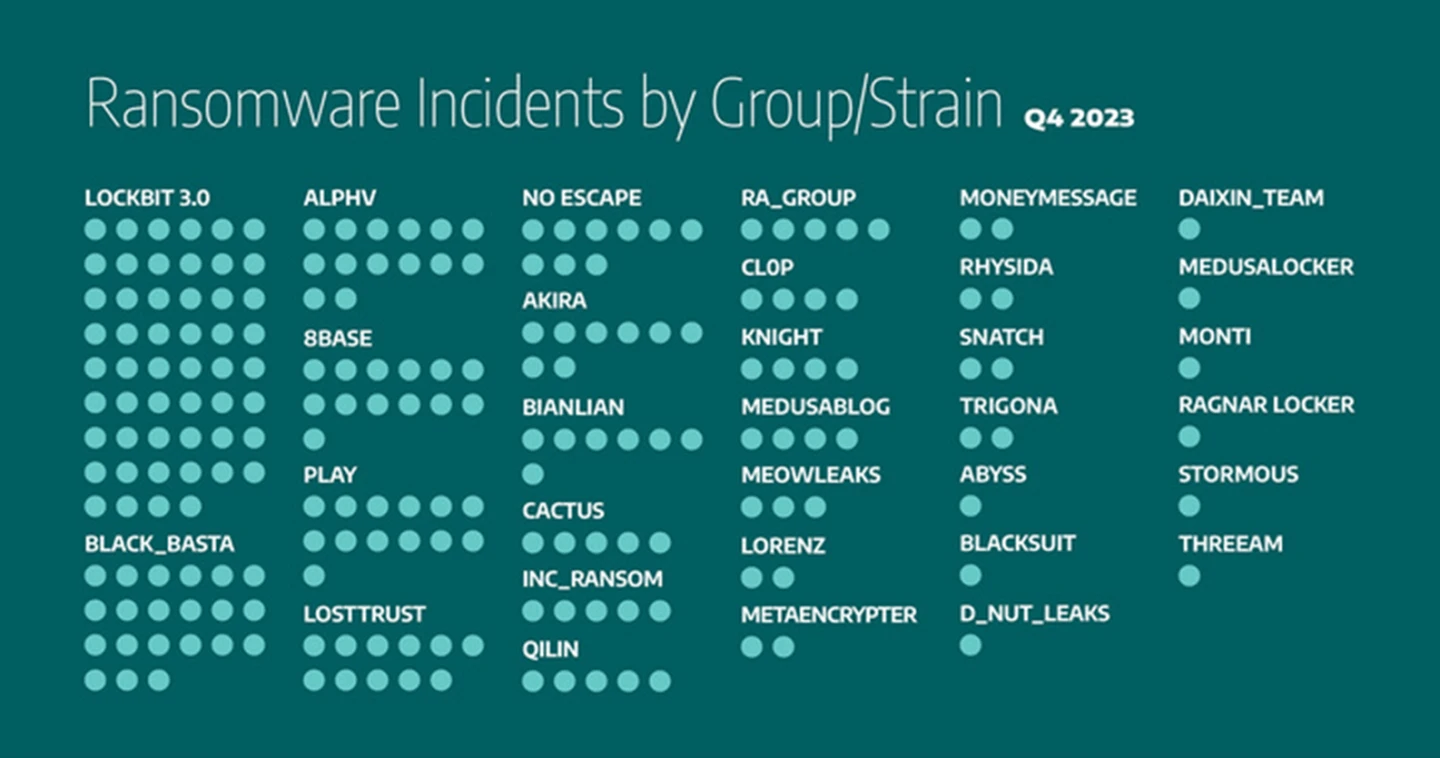
Dragos’s analysis of numerous ransomware data from the fourth quarter of 2023 indicates that the Lockbit 3.0 group was behind the most attacks against industrial organizations, with 25.5 percent (or 52 incidents) of observed ransomware events. The BlackBasta ransomware was the second with 10.3 percent (or 21 incidents). The following rounds out the observed ransomware group trends for the fourth quarter of 2023:
- AlphV was responsible for 6.8 percent of incidents (14 incidents).
- 8Base and Play: 6.3 percent each (13 incidents each)
- Losttrust was responsible for 5.4 percent of incidents (11 incidents).
- Noescape was responsible for 4.4 percent of incidents (9 incidents).
- Akira was responsible for 3.9 percent of incidents (8 incidents).
- Bianlian was responsible for 3.4 percent of incidents (7 incidents).
- Cactus, Inc Ransom, Qilin, Medusablog, and Regroup: 2.4 percent each (5 incidents each)
- Cl0p and Knight: 1.9 percent each (4 incidents each)
- Meowleaks was responsible for 1.4 percent of incidents (3 incidents).
- Lorenz, Metaencryptor, Money message, Rhysida, Snatch, and Trigona: less than one percent each (2 incidents each)
The remaining ransomware groups were responsible for one percent or less of incidents.
The groups that Dragos observed in the third quarter but not in the fourth quarter of 2023 are as follows:
- Cloak
- Ciphbit
- Rancoz
- Ransomed
- Mallox
- Everest
- Cuba
Dragos observed the following ransomware groups for the first time in the fourth quarter of this year:
- Knight
- Meowleaks
- Threeam
- Losttrust
- Metaencryptor
- Moneymessage
It is still being determined if these new groups are in fact new or if they are reformed or rebranded from other ransomware groups.
Looking forward, Dragos assesses with moderate confidence that the ransomware threat landscape will continue to evolve, marked by the emergence of new ransomware variants. These developments are expected as ransomware groups strive to refine their attack methodologies, likely keeping zero-day vulnerabilities as a key component in their operational toolkit.
Additionally, Dragos assesses with low confidence that ransomware groups may increasingly develop and deploy ransomware specifically designed to disrupt operational technology (OT) processes. This potential shift in focus towards OT processes could be driven by the continuous attempts of ransomware groups to exert greater pressure on victims to pay ransoms. By targeting critical OT processes, these groups could significantly amplify the impact of their attacks on industrial organizations. Such disruptions would not only affect operational capabilities but also compromise safety, thereby increasing the urgency and potentially compelling victims to meet ransom demands more readily.
This evolving strategy reflects a concerning trend in the ransomware landscape, where the consequences of attacks extend beyond data loss and financial impact to directly threaten the core operational integrity of targeted organizations.