Information provided here is sourced from Dragos OT Cyber Threat Intelligence adversary hunters and analysts who conduct research on adversary operations and their tactics, techniques, and procedures (TTPs). Dragos OT cyber threat intelligence is fully reported in Dragos WorldView threat intelligence reports and is also compiled into the Dragos Platform for threat detection and vulnerability management.
The third quarter (July – September) of 2024 brought transformative shifts to the ransomware landscape, emphasizing its dynamic and continuously evolving nature. The ransomware threat ecosystem remained highly active in the third quarter, fueled by new groups, rebranding of existing entities, expansion of initial access broker operations, and proliferation of illicitly traded tools. Ransomware operators increasingly demonstrated their ability to pivot in response to disruptions during the third quarter, leveraging technological advancements and strategic realignments to maintain their operations.
This period witnessed a critical shift as dominant groups like LockBit faced significant setbacks due to coordinated international law enforcement actions, including Operation Cronos, which dismantled key infrastructure elements of LockBit. This led to a decline in their activities and forced affiliates such as Velvet Tempest to transition to other groups, including RansomHub.
Concurrently, the ransomware-as-a-service (RaaS) model continued to mature, with an expanded reliance on Initial Access Brokers (IABs) that exploit vulnerabilities, misconfigurations, and stolen credentials that facilitated entry into targeted environments. These brokers acted as force multipliers, enabling ransomware groups to scale their operations by focusing on payload deployment and extortion strategies. In general, this industrialization of ransomware has continuously lowered the barriers to entry for new actors, fostering a competitive and dynamic threat environment, and the third quarter of 2024 was no different.
Adding to this complexity, escalations in geopolitical tensions during the third quarter introduced a new dimension to ransomware threats. Specifically, conflicts in the Middle East and Eastern Europe spurred a rise in hacktivist personas employing ransomware to disrupt industrial operations. Unlike traditional financially motivated ransomware campaigns, these actors appear to prioritize operational sabotage, posing a distinct and potentially catastrophic risk to critical infrastructure.
Sign up for the February 27th OT Cybersecurity Executive Briefing with Dragos CEO Robert M. Lee presenting the results of our latest Year in Review.
Sign Up Today!Emerging Ransomware Threats
In the third quarter of 2024, Dragos observed the emergence of several new ransomware groups impacting industrial organizations and multiple initial access and post-compromise techniques exploiting vulnerable remote and virtual network applications.
Newly observed ransomware groups that impacted industrial organizations in the third quarter are as follows:
|
|
|
These actors consistently attacked industrial sectors, employing several advanced tactics to exploit operationally critical IT systems. Notably, their campaigns seemed to prioritize industries and organizations with a low tolerance for downtime, such as healthcare, financial services, and industrial operations. By focusing on environments where operational disruption can lead to cascading impacts, these groups increased the likelihood of ransom payments, leveraging the criticality of uninterrupted services to pressure victims.
While some of the groups mentioned above represented entirely new entities, others are assessed to be rebranded versions of existing groups, such as APT73, reflecting the adaptability and resilience of ransomware operations. APT73 has been linked to the remnants of LockBit affiliates, repurposing operational techniques while introducing new payloads to evade detection and maintain their foothold in the ecosystem. This demonstrates how ransomware groups continuously evolve their tactics and infrastructure to remain effective and profitable despite increasing scrutiny from defenders and law enforcement.
Ransomware groups such as Fog, Helldown, and RansomHub were particularly active and gained traction by exploiting vulnerabilities in VPNs, and leveraging living-off-the-land techniques.
- Fog ransomware was first observed targeting virtual environments and backup systems critical to industrial operations. By exploiting vulnerabilities in hypervisors and backup solutions, Fog can encrypt virtual machine files and delete backups, significantly disrupting operational continuity.
- Helldown, leveraging tools from LockBit’s leaked builder, has been active in manufacturing sectors, leveraging sophisticated dual extortion techniques. The group has shown a propensity for credential harvesting and lateral movement using default administrative tools, ensuring persistence while maximizing impact.
- RansomHub, a RaaS operation, claimed over 300 victims globally in 2024. It has aggressively targeted industrial organizations in the energy, water management, transportation, and manufacturing sectors. Affiliates of RansomHub, including Velvet Tempest, have demonstrated advanced capabilities, such as deploying customized payloads and exploiting VPN vulnerabilities.
Other good examples that many ransomware operators have seemingly shifted their intrusion TTPs to focus on virtual networking applications are Eldorado and Play ransomware operators, who were observed targeting VMware ESXi environments.
In fact, exploiting remote services and virtual networking applications was quite popular for ransomware operators in the third quarter. According to at least one open source security blog, approximately 30% of ransomware incidents during the third quarter were linked to vulnerabilities in VPN appliances (for example, CVE-2024-40766 affecting SonicWall SSL VPNs) or poorly managed credentials.
To highlight this operational shift:
- From 2021–2023: VPN exploitation was predominantly associated with opportunistic attacks, with actors focusing on unpatched vulnerabilities in devices like Pulse Secure and Fortinet. During these years, VPN access served primarily as an initial foothold for lateral movement or deploying ransomware payloads in high-profile cases like Colonial Pipeline (2021).
- In 2024: Ransomware operators have advanced their tactics by combining vulnerability exploitation with credential-based attacks to bypass multi-factor authentication (MFA) protections. They employ credential stuffing, pass-the-hash attacks, and brute force techniques. Compromised credentials, often sourced from Initial Access Brokers (IABs), have become central to their strategies. For instance, the Akira ransomware group has been observed exploiting vulnerabilities in VPN appliances to gain initial access to networks.
Advanced Lateral Movement and Persistence Techniques
Lastly, Dragos observed multiple ransomware groups that expanded their post-compromise lateral movement capabilities in the third quarter by blending traditional methods with advanced persistence mechanisms:
- Living-Off-the-Land Techniques (LOLTs): Ransomware operators evaded detection by mimicking legitimate network activity using legitimate administrative tools like PowerShell, certutil.exe, and PsExec.
- Abuse of Remote Access Tools: Tools like AnyDesk and Quick Assist continued to be exploited to establish persistent access. This quarter also saw increased use of remote access tools in conjunction with custom scripts designed to disable antivirus protection.
- Targeting Virtual Environments: Groups like Eldorado and Play developed Linux lockers specifically to target VMware ESXi environments. These lockers encrypt critical virtual machine files while disabling active VMs, disrupting business operations with minimal pre-encryption dwell time.
- Integration of Advanced Malware: Groups such as Black Basta shifted to custom malware, employed backdoor tools like SilentNight, tunneling utilities like PortYard, and memory-only droppers like DawnCry to maintain persistence and evade endpoint detection.
Although Dragos is unaware of any direct attacks on operational technology (OT) assets by the newly identified ransomware groups, ransomware-induced downtime in IT environments often halted industrial processes and led to financial losses, production delays, and safety risks. The interconnected nature of IT and OT networks continued to create dependencies that amplified disruptions from a successful ransomware incident.
Further, the emergence of all these new groups during the third quarter of 2024, coupled with established groups like LockBit3.0 facing disruptions from law enforcement actions, illustrated the ever-changing ransomware landscape. While some actors scaled back or rebranded under new names, others introduced novel tactics, techniques, and procedures (TTPs) to evade detection and maximize impact.
Dragos assesses with moderate confidence that ransomware activity targeting industrial organizations will continue to escalate into the future, driven by financially and ideologically motivated actors. The shift from traditional financial extortion to operational sabotage, particularly by hacktivist personas, compounds these risks. This convergence of motivations further blurs the line between cybercrime and cyberwarfare, requiring enhanced defenses for ICS and OT environments.
Ransomware Impacts on Industrial Organizations
In the third quarter of 2024, ransomware attacks continued to significantly disrupt industrial organizations, leading to operational halts, financial losses, and compromised data integrity. Notable incidents included the following:
| CDK Global | Date: June 2024 Ransomware Group: BlackSuit Impact: A ransomware attack incapacitated CDK Global’s services, affecting thousands of car dealerships across the U.S. and Canada. The company paid a $25 million bitcoin ransom to restore operations. The incident led to a substantial decline in share value and disrupted automotive retail operations nationwide. |
| Halliburton | Date: September 2024 Ransomware Group: linked to RansomHub Impact: Halliburton, a leading oilfield services company, experienced a ransomware attack linked to RansomHub group. The breach disrupted operations, affecting the company’s ability to process invoices and manage purchase orders. Halliburton reported a financial impact of approximately $35 million due to the incident. The company confirmed that unauthorized parties accessed and exfiltrated information from its systems. |
| Arkansas City Water Treatment Plant | Date: September 2024 Ransomware Group: BlackSuit Impact: The Arkansas City Water Treatment Plant in Kansas was impacted by a cyber attack, prompting the facility to switch to manual operations as a precaution. The city manager confirmed that the water supply remained safe and uninterrupted, with enhanced security measures implemented to ensure water quality for residents. |
| Transport for London (TfL) | Date: September 2024 Ransomware Group: Unknown Impact: A cyber attack impacted Transport for London (TfL), causing intermittent disruptions to online services for weeks while critical transport systems remained operational. Although the full scope of the attack is unclear, the unavailability of scheduling systems and online platforms days later raised suspicions of ransomware involvement. According to a press release in November 2024, the investigation of this incident is ongoing. |
| Arntz Optibelt Group | Date: August 2024 Ransomware Group: Unknown Impact: A cyber attack disrupted the IT infrastructure of Arntz Optibelt Group, a major manufacturer of high-performance belt drives based in Höxter, Germany. The incident significantly impacted the company’s ability to conduct normal business operations. |
Hacktivism and the Rise of Ransomware-Driven Operations
During the third quarter of 2024, Dragos observed an escalating trend of hacktivist groups integrating ransomware into their operations, signaling a significant shift in tactics and potential impact. Groups such as CyberVolk, Handala, and KillSec leveraged ransomware to amplify the disruption caused by their campaigns, blurring the lines between ideological activism and financially motivated cybercrime.
CyberVolk, in particular, represents a troubling development within the ransomware ecosystem. Operating under the alias “cybervolk_group” on social platforms, the group launched its own RaaS platform in June 2024 and announced the development of its proprietary CyberVolk ransomware in July 2024. This ransomware has been deployed in pro-Russian campaigns targeting critical infrastructure, combining encryption algorithms with advanced payload delivery mechanisms typically seen in financially motivated operations.
Although Dragos has not observed any direct impacts on industrial organizations during the third quarter of 2024, the growing sophistication and operational focus of groups like CyberVolk remain deeply concerning. The integration of ransomware into hacktivist operations represents a dangerous convergence of destructive malware and ideological motives, increasing the likelihood of significant impacts on critical infrastructure sectors in the future. This trend demands heightened vigilance, as it underscores the evolving risks posed by hacktivist groups leveraging ransomware for political and ideological ends.
Regional Impact Observations, Third Quarter of 2024
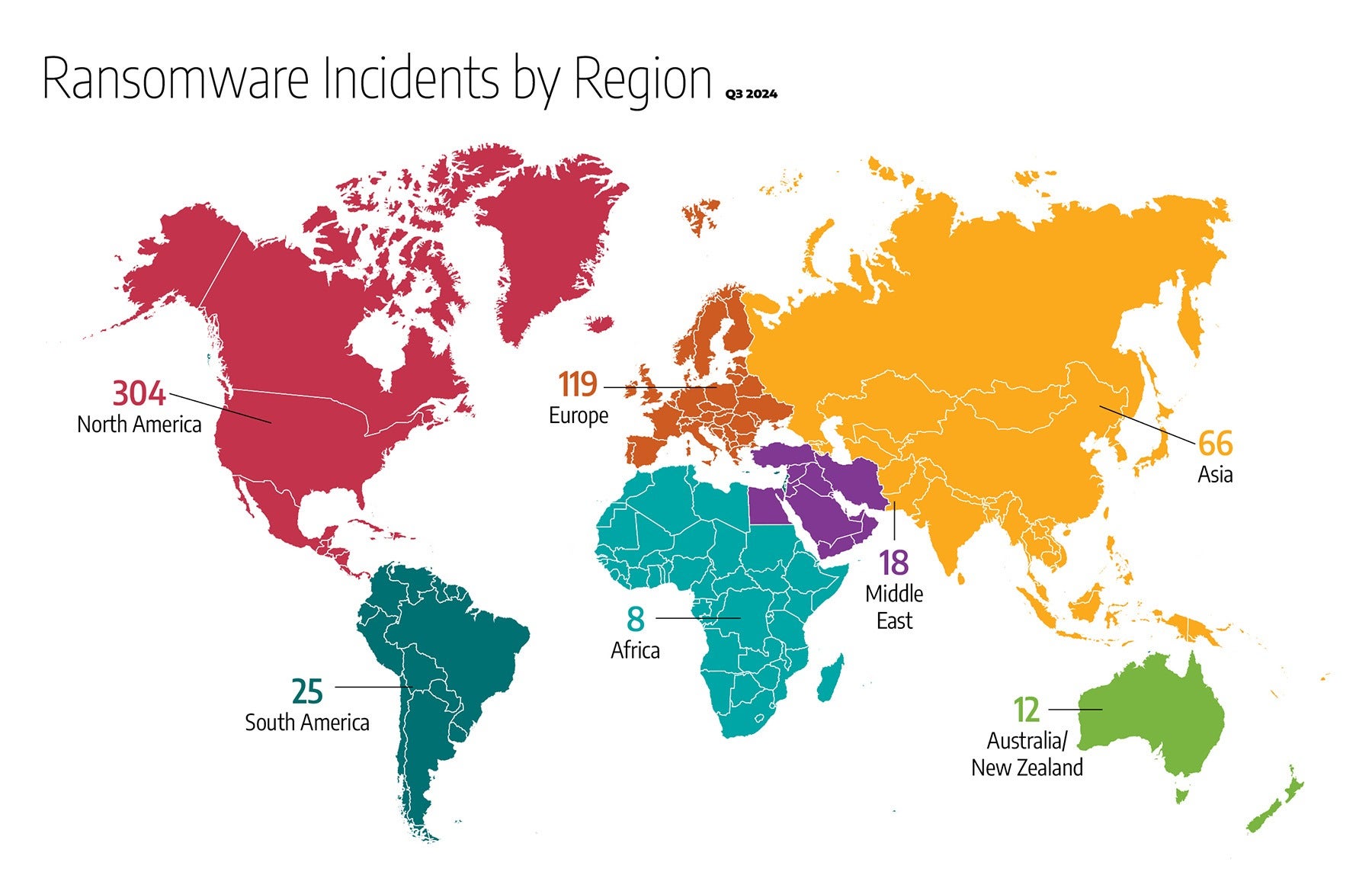
Ransomware incidents in the third quarter of 2024 demonstrated distinct regional variations, with North America continuing to experience the highest volume of attacks. The data reflects the global nature of ransomware threats, with every region affected to varying degrees.
- North America experienced the highest number of ransomware incidents, accounting for 304 attacks (approximately 55% of global ransomware activity). Most of these targeted the United States and Canada, with adversaries focusing on critical sectors such as manufacturing, utilities, and healthcare.
- Europe was the second most impacted region, with 119 incidents (approximately 22% of global ransomware attacks). The United Kingdom, Germany, and Italy were among the most targeted countries, with attacks primarily affecting manufacturing, transportation, and technology sectors.
- Asia witnessed 66 incidents (approximately 12% of global ransomware activity). Significant targeting was observed in Japan, India, and South Korea, particularly within the manufacturing sector.
- South America recorded 25 incidents (approximately 4.5% of global ransomware activity). Brazil and Argentina were key targets, with attackers focusing on government operations and transportation systems.
- The Middle East experienced 18 ransomware incidents (approximately 3% of global ransomware activity).
- Oceania reported 12 incidents (approximately 2% of global ransomware activity). Australia and New Zealand were the primary targets, and the incidents impacted the technology, education, and healthcare sectors.
- Africa accounted for eight ransomware incidents (approximately 1.5% of global ransomware activity).
Industry Impacts, Third Quarter of 2024
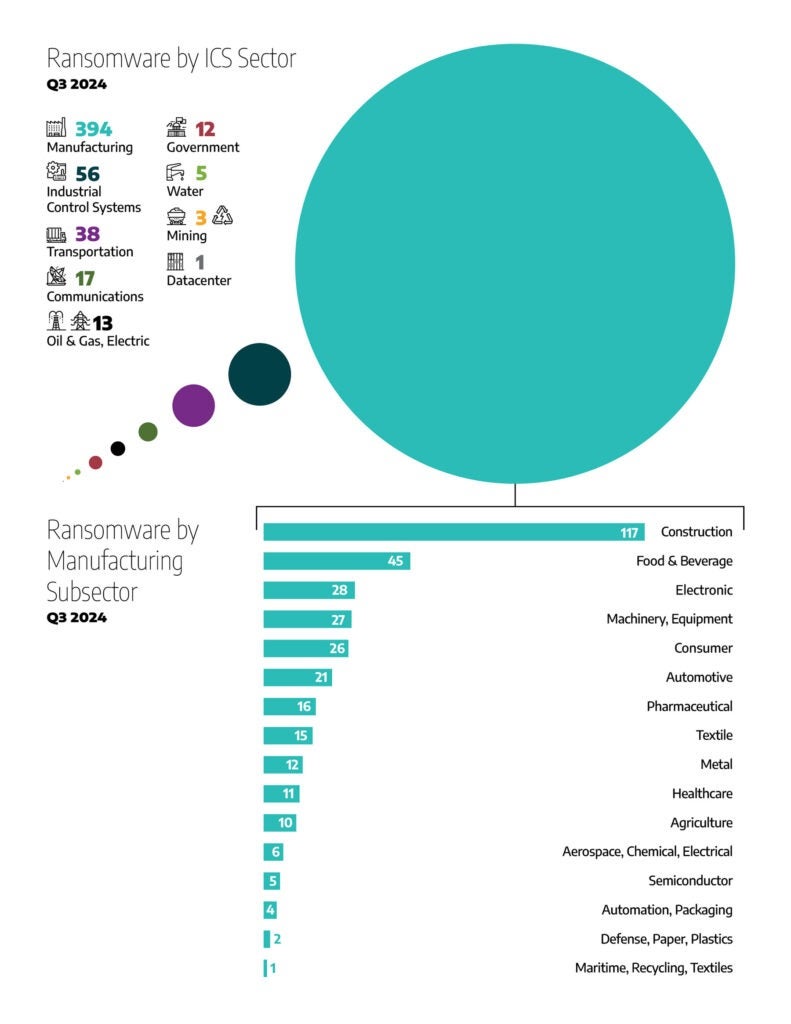
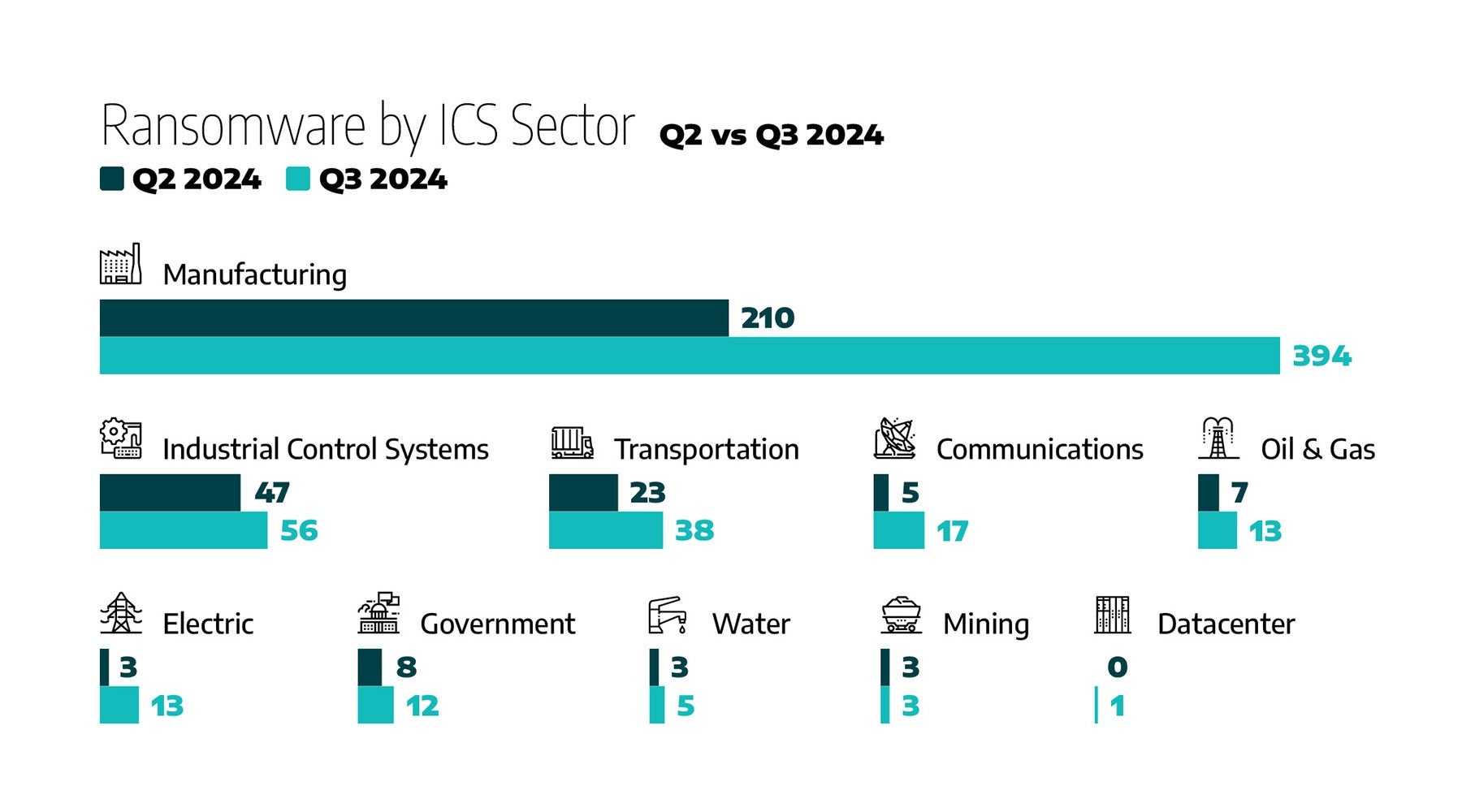
- Manufacturing was the most impacted, with 394 observed incidents, accounting for 71% of all ransomware incidents.
- Industrial control systems (ICS) equipment and engineering experienced 56 incidents, making up approximately 10% of the total incidents.
- Transportation faced 38 incidents, representing 7% of all observed incidents.
- Communications and electric each experienced 17 and 13 incidents, collectively making up approximately 5% of ransomware incidents.
- Oil and natural gas (ONG) recorded 13 incidents, reflecting 2% of the total incidents.
- Government entities faced 12 ransomware incidents, making up 2% of the total incidents.
- Water and wastewater entities faced five ransomware incidents.
- Mining faced three ransomware incidents.
- Datacenters faced one ransomware incident.
In addition to the primary industries and sectors mentioned above, Dragos observed ransomware activity impacting 23 unique manufacturing subsectors in the third quarter of 2024. The percentage breakdown, based on all manufacturing incidents, is as follows:
- Construction: 117 incidents (30% of manufacturing incidents).
- Food & Beverage: 45 incidents (11%).
- Machinery and Equipment: Each had 27 incidents (7% each).
- Electronics: 28 incidents (7%).
- Consumer Goods: 26 incidents (6%).
- Automotive: 21 incidents (5%).
- Pharma: 16 incidents (4%).
- Textile: 15 incidents (4%).
- Metal: 12 incidents (3%).
- Healthcare: 11 incidents (3%).
- Agriculture: 10 incidents (3%).
- Aerospace, Chemical, and Electrical: Each had six incidents (2% each).
- Semiconductor: 5 incidents.
- Automation and Packaging: Each had four incidents.
- Defense, Paper, and Plastics: Each had two incidents.
- Maritime, Recycling, and Textiles: Each had one incident.
As illustrated in Figure 3 below, ransomware incidents during the third quarter of 2024 have significantly increased compared to the previous quarter, with sectors such as manufacturing experiencing heightened activity. This trend highlights ransomware operators’ sustained focus on industries critical to operational continuity and infrastructure
Ransomware Group Trends, Patterns, and Observations During the Third Quarter of 2024
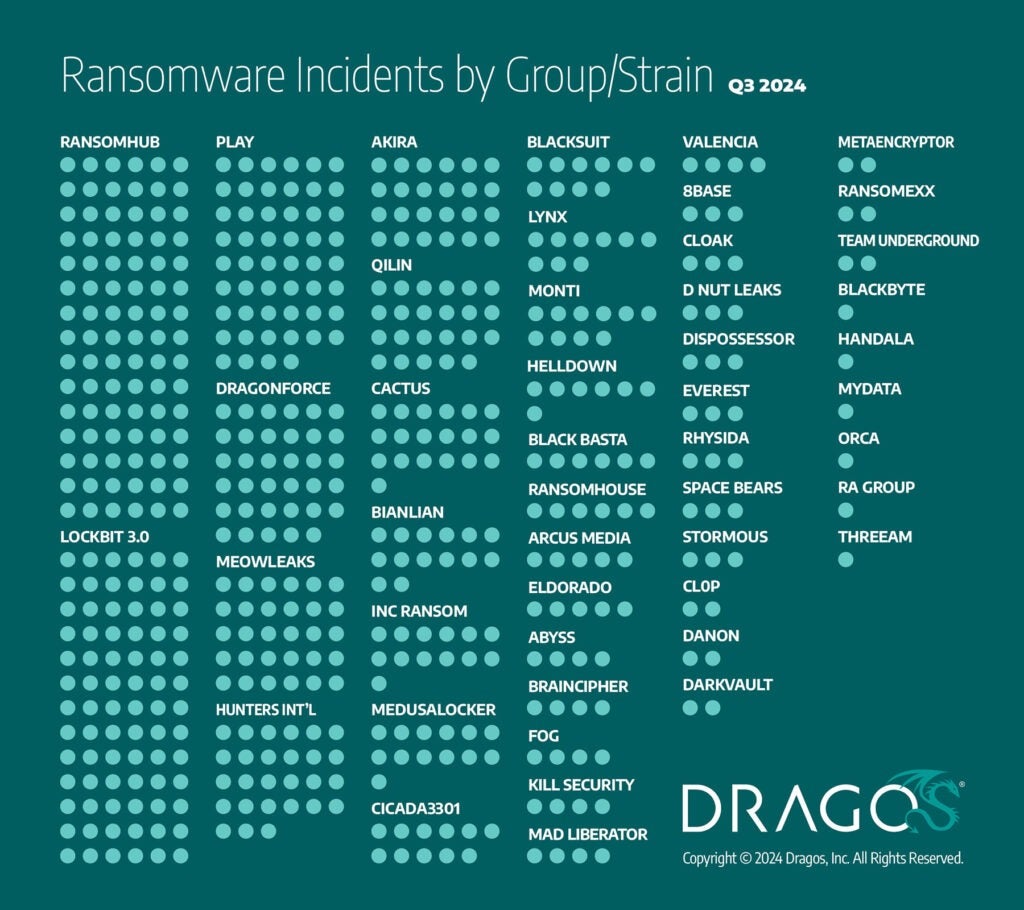
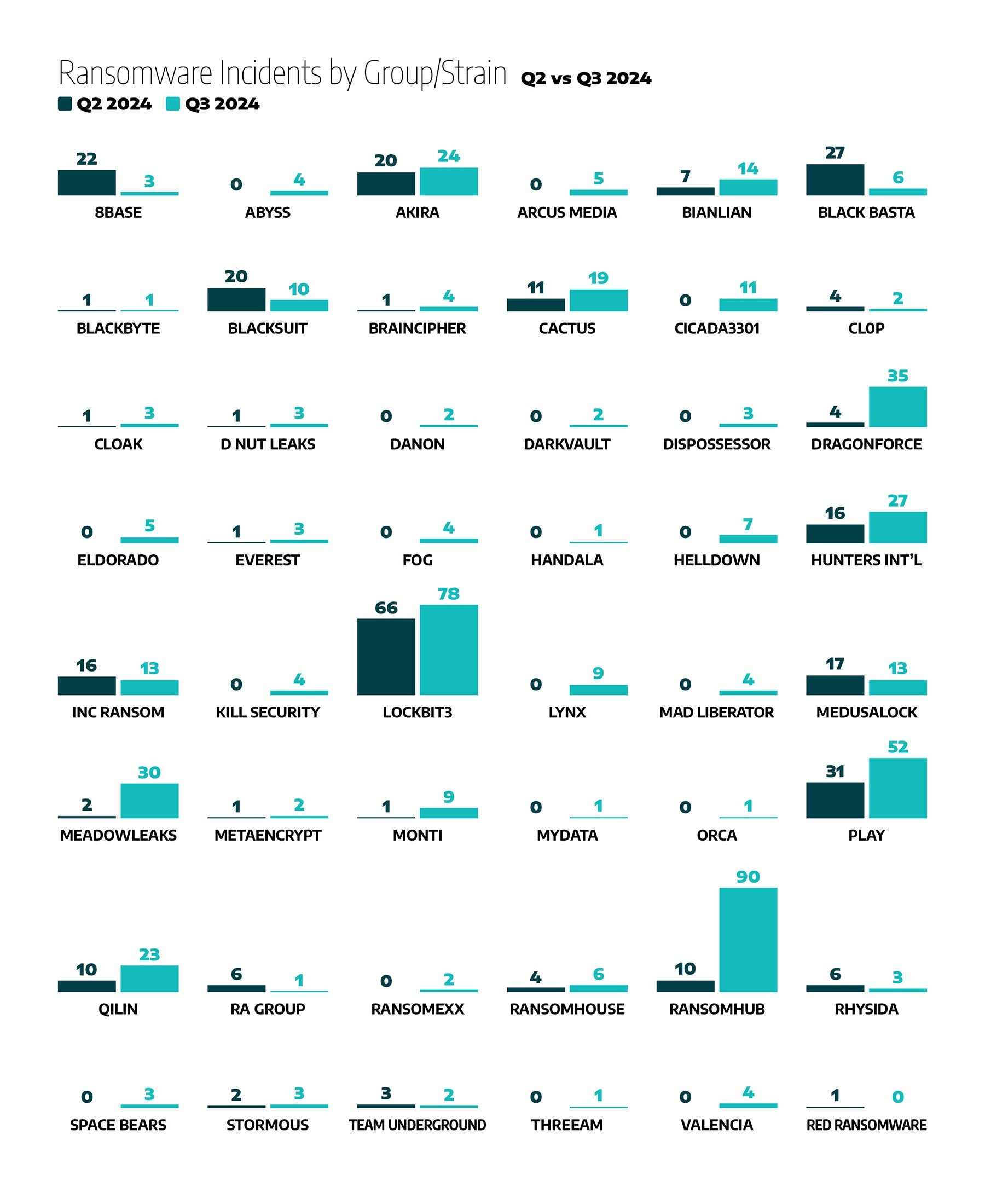
Dragos’s analysis of ransomware activity in the third quarter of 2024 shows significant shifts in the landscape, with some groups demonstrating notable increases in activity. LockBit3.0, RansomHub, and Play emerged as the most active ransomware groups targeting industrial organizations during this period.
- RansomHub was the most active ransomware group this quarter, with 90 incidents, accounting for approximately 16% of all ransomware activity.
RansomHub’s rapid rise in activity can be attributed to its aggressive RaaS model and its ability to attract affiliates following the disruption of competing platforms such as LockBit3.0. Among its most prominent affiliates is Velvet Tempest, which transitioned to RansomHub after previously operating under the LockBit3.0 framework.
Dragos tracks Velvet Tempest as a notable actor within RansomHub’s operations. This affiliate employs advanced tactics to impact industrial organizations, including malvertising campaigns and exploiting VPN vulnerabilities. Since the group activities started impacting industrial organizations in May 2024, RansomHub has been linked to 168 ransomware incidents globally, with a significant concentration of activity in North America and Europe, focusing heavily on the industrial sectors.
The ransomware attack on Halliburton is a prominent example of RansomHub’s focus on industrial organizations. The attack caused widespread disruption to Halliburton’s operations, significantly impacting its ability to process invoices and manage purchase orders. - LockBit3.0 was responsible for 78 incidents, accounting for approximately 14% of observed ransomware events in Q3 2024. The group remains one of the most active ransomware operators globally, targeting various sectors with large-scale campaigns. However, Dragos’s analysis suggests that as many as two-thirds of new victim announcements since February 2024 were duplicated or unverifiable. This tactic is likely an effort to inflate their perceived activity levels and maintain their reputation within the ransomware ecosystem following the significant disruptions caused by Operation Cronos.
- Play: Involved in 52 incidents, representing 9% of ransomware activity. Play continues to target critical infrastructure and industrial organizations.
- DragonForce: Linked to 35 incidents, or approximately 6% of ransomware events.
- Qilin: Accounted for 23 incidents, making up 4% of observed ransomware events.
- Cactus: Responsible for 19 incidents, representing approximately 3% of ransomware activity.
- Hunters International: Reported 27 incidents, accounting for 5% of activity.
- Akira: Involved in 24 incidents, making up 4% of ransomware events.
- BianLian: Linked to 14 incidents, approximately 2% of total ransomware activity.
- MedusaLocker and Inc Ransom: Each accounted for 13 incidents, or approximately 2% each.
Other notable groups:
- BlackSuit: 10 incidents (2%).
- Monti: 9 incidents (2%).
- Lynx: 9 incidents (2%).
- MeowLeaks: 30 incidents (5%).
- Valencia, Mad Liberator, Kill_Security, and Abyss: Each recorded 4 incidents (1% each).
The figure below highlights a marked increase in incidents attributed to many ransomware groups during this period. The data reflects the dynamic and evolving nature of the ransomware landscape, with several groups demonstrating significant growth in activity. Dragos has yet to determine whether the new ransomware groups represent entirely new actors or rebranded preexisting ransomware groups.
In Conclusion
The third quarter of 2024 highlighted the ongoing evolution of ransomware threats. Established groups like RansomHub, LockBit3.0, and Play maintained prominence while new actors emerged to exploit vulnerabilities in IT and OT environments. The industrial sector, particularly manufacturing and ICS equipment and engineering, remained a prime target, with ransomware operators leveraging advanced tactics and exploiting weak credential practices and vulnerabilities in remote access systems.
Organizations must prioritize strong cybersecurity measures to mitigate these threats, including monitoring critical ports, enforcing multi-factor authentication (MFA), maintaining offline backups, and securing remote access. Enhanced personnel training and continuous assessment of network architecture are critical to defending against evolving tactics.
As the ransomware landscape continues to fragment and adapt, proactive defenses, intelligence sharing, and collaboration will remain essential to protecting critical infrastructure and industrial operations.

5 Critical Controls for OT Cybersecurity
Ready to put your insights into action?
Take the next steps and contact our team today.

