We’re excited to announce the release of our 8th Annual OT Cybersecurity Year in Review report. This annual report reveals the ground truth of what’s happening across the operational technology (OT) and industrial control systems (ICS) cyber threat landscape. Additionally, we offer strategic guidance on how to address these threats and build a better cyber defense.
We are proud to deliver the eighth version of our annual OT/ICS cybersecurity report. Eight years ago, we saw a need in the industrial community and an opportunity to fill an information gap. Industrial organizations were increasingly under threat of cyber attack yet struggled to find the insights they need to know how to defend against these threats. Information like how adversaries executed their industrial cyber attacks, what security gaps they exploited, and what defenders needed to do to stop them. Given that gap and armed with the data and insights from Dragos OT experts, we published our first-ever Year in Review report in 2017. Every year since, we’ve been tracking how industrial cyber threats evolve – how they get in, what they target, and where the defenses are failing within industrial environments – and sharing it with the broader OT/ICS community.
This year’s report addresses how OT cybersecurity threats are escalating, how adversaries are adapting, and what defenders should do in response. While adversaries are becoming aware of the impact they can achieve against easy-to-access industrial control systems (ICS), many industrial organizations continue struggling with OT security fundamentals.
Read on to learn more. Or, get your copy of the full report.
Tracking Adversaries Focused on OT
Driven by geopolitical conflicts, adversaries across the spectrum are actively compromising OT networks, collecting intelligence, and pre-positioning for disruptive action. Dragos tracks 23 threat groups targeting industrial organizations, nine of which were active, with two new threat groups detailed in this year’s report.

New Threat Group Activity
BAUXITE (U.S., Europe, Australia, the Middle East – Targeting Oil & Gas, Water & Wastewater, Chemical Manufacturing)
BAUXITE is capable of Stage 2 ICS Cyber Kill Chain and has demonstrated the ability to compromise PLCs and deploy custom backdoors on OT devices. The group shares technical overlaps with CyberAv3ngers, a pro-Iranian hacktivist persona. Recent campaigns have targeted Sophos firewalls, exposed ICS devices, and industrial remote access solutions, with clear disruptive intentions.
GRAPHITE (Eastern Europe & the Middle East – Targeting Energy, Government, Logistics)
GRAPHITE, which has technical overlaps with APT28, is suspected of aligning with broader state-backed geopolitical objectives. Throughout 2024, the group engaged in near-constant spear-phishing campaigns, exploiting known vulnerabilities and deploying custom malware to steal credentials and access industrial networks.
Existing Threat Group Activity
VOLTZITE (U.S., Guam – Targeting Electric, Water, Telecom, Defense)
VOLTZITE has technical overlaps with Volt Typhoon and is among the most dangerous adversaries targeting OT environments. This threat group exfiltrates GIS data, OT network diagrams, and ICS operating instructions that could be used to develop targeted attacks. Their ability to blend into trusted networks using compromised SOHO routers makes detection especially difficult.
KAMACITE (Ukraine, Eastern & Central Europe – Initial Access for ICS Attacks)
KAMACITE serves as an initial access provider for OT-targeting groups, including ELECTRUM. The group leveraged the Kapeka backdoor to infiltrate European oil & natural gas (ONG) companies and deployed LummaStealer malware during high-profile industry events. Their shift toward targeting third-party vendors presents new risks for ICS supply chains.
ELECTRUM (Ukraine, Germany – Electric Sector Disruptions & ICS Wipers)
ELECTRUM is a long-standing OT threat group and the first threat group tracked by Dragos. It remains a key player. In 2024, this group was linked to the KyivStar telecommunications attack and the new AcidPour wiper, capable of wiping embedded devices in OT environments, was introduced. This group’s focus on ICS attacks makes it one of the most disruptive threats to industrial operations.
The 2025 OT/ICS Cybersecurity Report also details observed activities of Temporary Activity Threat Groups (TATs) that have impacted operational technology and industrial control systems.
Analyzing the Deployment of ICS Malware
Unlike general-purpose IT malware, ICS malware is purpose-built to impact industrial control systems, making it an immediate operational risk to industrial and critical infrastructure. In 2024, Fuxnet and FrostyGoop, the eighth- and ninth-known ICS malware families, respectively, were discovered.
Fuxnet Disables Russian Monitoring Devices
Fuxnet was deployed against Moscow’s municipal sensor networks, reportedly disabling thousands of monitoring devices. The malware:
- Overwrites firmware on sensor gateways, rendering them inoperable.
- Exploits default credentials and poor access controls, a reminder that basic cybersecurity hygiene remains critical.
While Fuxnet was narrowly tailored to a specific target, its tactics, and techniques provide a blueprint for future ICS malware development, making it a concern for industrial defenders worldwide.
FrostyGoop Disrupts Heating Services in Ukraine
Discovered by Dragos in January 2024, FrostyGoop was used in an attack on the energy supply for district heating systems in Ukraine, leading to heating outages for over 600 apartment buildings during sub-zero temperatures.
Key details include:
- Uses Modbus TCP for direct interaction with ICS devices, a first-of-its-kind attack technique.
- Bypasses standard antivirus tools, demonstrating the need for OT-native threat detection.
FrostyGoop highlights the growing adversary focus on exploiting standard ICS protocols like Modbus, CIP, OPC/UA, and S7Comm. These trusted but insecure protocols are frequently left unmonitored, providing adversaries with an undetected attack path.
Assessing the Industrial Ransomware Threat
Dragos documented 1693 ransomware attacks targeting industrial organizations in 2024, an 87 percent increase in ransomware attacks over the previous year. Manufacturing remains the hardest-hit sector, but ransomware’s expansion into energy and critical infrastructure is a growing concern.
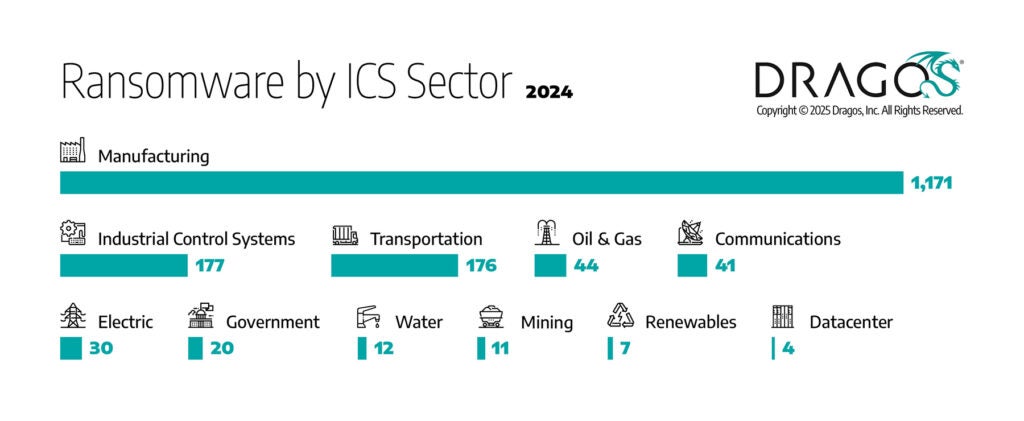
Ransomware is not just an IT problem. Of the ransomware incidents Dragos responded to in 2024, 75 percent led to a partial shutdown of operational technology and 25 percent led to a full shutdown of operational technology.
Using the “Now, Next, Never” Vulnerability Management Framework
Managing vulnerabilities in OT environments requires a risk-based approach, rather than traditional IT patching strategies. The “Now, Next, Never” vulnerability management framework helps organizations prioritize risks based on their real-world impact and exploitability in industrial operations.
This year, Dragos reported:
- 6 percent of OT vulnerabilities fall into the “Now” category – Critical issues requiring immediate remediation, often due to active exploitation, significant impact, or direct exposure.
- 63 percent of OT vulnerabilities fall into the “Next” category – High-priority issues that should be addressed in a planned timeframe to reduce risk before attackers exploit them.
- 31 percent of OT vulnerabilities fall into the “Never” category – Low-priority vulnerabilities that do not pose an immediate risk and should not be a focus of remediation unless circumstances change.
Benchmarking Security Gaps in Industrial Organizations
While some progress has been made in securing industrial environments, major gaps persist that are leaving OT networks vulnerable to ransomware, ICS malware, and advanced threat actors. The 2025 OT Cybersecurity Year in Review report highlights key areas where organizations continue to struggle:
Incident Response for OT Is Poorly Defined or Untested
- Many industrial organizations do not have an OT-specific incident response plan, making response efforts slow and uncoordinated during an attack.
- Most ICS engineers and OT personnel are not trained in cyber incident response, leaving them ill-equipped to recognize or contain cyber threats.
- Organizations struggle to understand what caused a cyber incident. Limited forensic data collection in OT environments means that after an incident, organizations don’t have the insights they require to know what happened—or if the threat is still present.
OT Network Segmentation Is Inconsistent and Often Ineffective
- Many organizations believe they have proper IT/OT network segmentation, but routine penetration tests reveal hidden connections bridging IT and OT.
- Flat networks remain common, allowing attackers to pivot freely between enterprise and industrial environments.
- Misconfigured firewalls and poorly managed DMZs expose critical OT assets to threats they were never designed to withstand.
OT Visibility Remains Alarmingly Low
- Many organizations lack real-time monitoring of OT networks, making it challenging to detect adversary activity.
- Even when a cyber incident occurs on IT systems, defenders often cannot determine if OT environments were compromised.
- Legacy OT protocols (e.g., Modbus, DNP3, OPC-UA) remain unmonitored, allowing adversaries to operate undetected.
Insecure Remote Access Is a Persistent Risk
- 65 percent of sites assessed had insecure remote access conditions, including default credentials, unpatched VPNs, and exposed RDP sessions.
- Third-party vendors and contractors continue to be a major weak point, with some organizations unaware of all remote connections into their OT networks.
- Many OT environments still rely on outdated “trust-based” remote access policies, instead of role-based, monitored, and segmented access controls.
OT Vulnerability Management Is Still Reactive, Not Proactive
- 70 percent of vulnerabilities identified were deep within OT networks, making them difficult to patch without disrupting operations.
- 22 percent of network-exploitable vulnerabilities were perimeter-facing, providing adversaries with a direct attack path into OT environments.
- Many organizations still treat OT vulnerabilities like IT vulnerabilities, failing to apply risk-based prioritization to focus on real-world threats.
Organizations that address the issues in these key areas referenced above are better equipped to detect, mitigate, and respond to the growing threats against industrial operations.
The Path Forward: Prioritize OT Cybersecurity Now
Dragos’s 8th Annual OT Cybersecurity Year in Review provides critical insights and actionable intelligence to help organizations defend their OT environments. Eight years of threat groups impacting critical infrastructure. Eight years of watching security gaps get exploited when organizations are flying blind. Eight years of watching defenders turn insights into action – strengthening their organizations and protecting the communities they serve.
Download the report to ensure your organization is ready for the challenges ahead.

Ready to put your insights into action?
Take the next steps and contact our team today.
