The Dragos Industrial Security Conference (DISC) is an annual event celebrated on November 5th that provides attendees with some of Dragos’s best research through multiple cybersecurity presentations focused on industrial control systems (ICS) and operational technology (OT). Last year, Dragos offered the event’s first Capture the Flag (CTF) contest, and considering its immense success, we decided to offer it again this year. The main goal was to give back to the global OT and InfoSec community by providing free access to a series of fun and engaging challenges.
But before showing the results of this year’s competition, we would like to take a step back and describe how it all started several months prior to DISC. In the following sections, we will explain how we exchanged ideas and how those ideas became the unique challenges for Dragos’s DISC CTF.
What Is Capture the Flag (CTF)?
A Capture the Flag (CTF) event is a great way for cybersecurity practitioners to learn, practice, and develop new skills and knowledge in tackling specific security challenges they may encounter on the job. These skills and knowledge not only apply to red-teamers acting as adversaries in simulated events to test detection and response capabilities but blue-teamers playing as the defenders protecting critical assets.
The CTF security challenges are often designed to make participants think outside the box to help develop a deeper understanding of accessible/non-accessible ports, network protocols, and network communications and often leverage user or system misconfigurations.
Want to play in the next Dragos CTF?
Sign up now for the next Dragos CTF, a 48-hour virtual event scheduled from November 2-4, 2023.
Register to PlayHow We Built the DISC CTF
The second edition of DISC CTF also focused on industrial control systems. We attempted to improve the understanding of the five critical controls for ICS/OT cybersecurity identified by the SANS Institute by exploring multiple scenarios connected directly or indirectly. Additionally, we wanted to expose all participants to challenges not found in traditional (i.e., only IT security) CTF events. Consequently, we decided to concentrate on six main categories:
| Category | Relevance |
| Phishing E-Mail Analysis | Most OT breaches are still involving IT and general office equipment |
| ICS Protocol PCAP Analysis | With OT components being networked their traffic becomes relevant for Prevention, Detection and Response |
| Digital Forensics | OT components often require special consideration and unusual approaches to forensics |
| Engineering & Network Diagrams Analysis | Assessments and activities in OT environments require a detailed understanding of networks and the corresponding process documentation |
| Application Exploitation – Buffer Overflow Analysis | OT vulnerability management is different and patching vulnerable applications is not always possible. Let’s exploit them! |
| PLC Programs and Logic Files Analysis | Industrial components often have a specific programming language that many professionals consider something new and challenging |
Project Milestone 1 – Develop the Storyline
Our next task was to create a story to connect all the challenges. The Dragos team looked at current events (e.g., Pipedream and the rise of CHERNOVITE, the 19th ICS-focused threat group that Dragos tracks) and used these as inspiration for the CTF background. The story completion provided the first milestone for the CTF project, allowing Dragos professionals from several teams to provide specific ideas for the challenges within certain boundaries. Every idea was evaluated to ensure that it was relevant, fun, and accessible to participants with different experiences and skills.
Project Milestone 2 – Assess the Feasibility
Once an idea was proposed and accepted, our team evaluated its feasibility (i.e., can it be solved in a CTF environment?) before building the corresponding artifacts. We needed to think beyond the game content and look at the context from the player’s perspective. Therefore, we started conceiving ways to expedite the artifact delivery and minimize the chances of misconfigurations. This analysis resulted in the files bundled to download before the contest and the Virtual Machine (VM) with specific PLC tools. Our purpose was to ensure that artifacts were not interfering with the player’s ability to solve the challenge and that, the majority of the time, the focus was on the challenge and not the tools. Once we got all artifacts for the different challenges, we reached the second milestone of the project.
Project Milestone 3 – Test the Challenges
The final part consisted of validating and verifying each challenge to be deployed for the CTF. More Dragos professionals joined the project and ensured that the challenge description, artifacts, hints, and flags were correct, fair, and solvable. After reviewing all 42 challenges, the team started the CTF deployment and conducted a final test before starting the competition. It was the third and last milestone, meaning we were ready for the competitors.
How We Supported DISC CTF Participants
As not to reveal solutions or hints to other participants that did not request them, Dragos used direct messaging to communicate with the individual teams. Depending on the difficulty of the challenge and the level of progress the Dragos’s team aided in finding the right starting point, and the right answer format or provided general guidance on how to approach a question.
DISC 2022 CTF By the Numbers
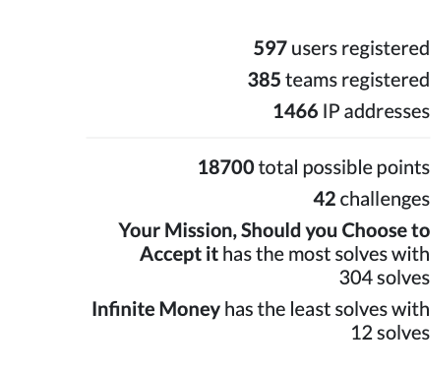
In 2022, we doubled the number of players compared to last year’s CTF. We had 597 registered players that found themselves together in 385 teams. Here’s a quick summary of the final results of this year’s DISC CTF.
Player Demographics
OT security is a global topic and that is also represented by our players. Players logged in from every continent but the arctics. In addition to the expected strong competition from North America, Europe, Asia, and Australia showed their skills in securing, hacking, digital forensics, and programming OT components and networks. This year the Dragos’s team added even more and completely new challenges, raising the count to 42 – some teams even had the answer to everything.
At the end of two days, 9 teams succeeded in completing the competition. Among those was also one team with a single member – one person that solved all questions on their own. Impressive! Many teams showed impressive motivation and exceptional skills in solving our challenges and the feedback shows that we hit the mark – not too easy, not too hard, and not unfair. An overall good mix that our players enjoyed.
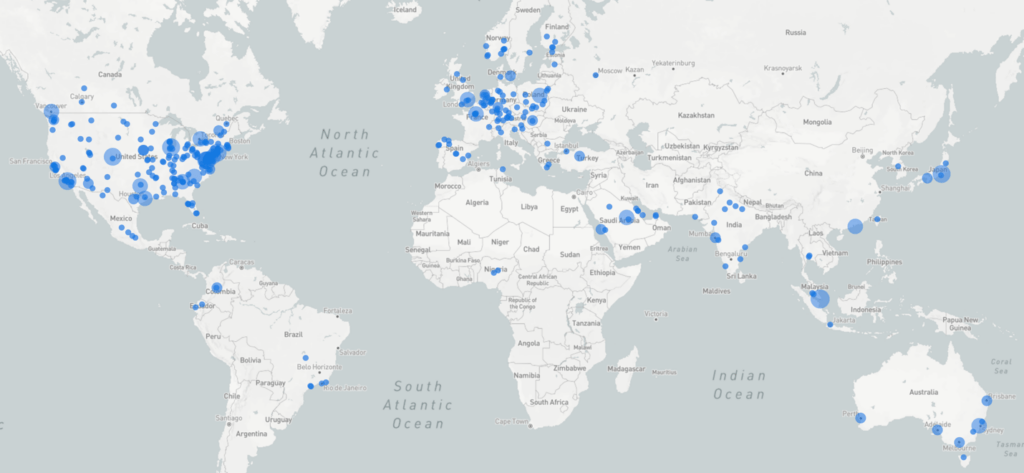
Although it is not possible to ensure that each IP used by the participants during the competition represents a real player (or their real location), it is interesting to note that sources registered are also well distributed with clusters in North America and Europe.
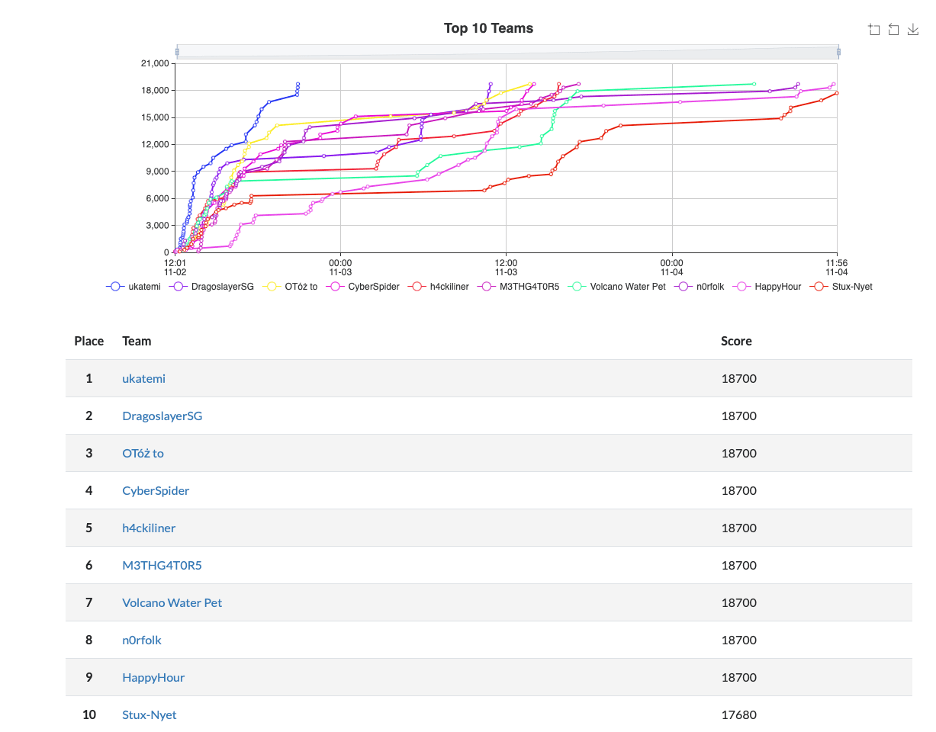
The Leaderboard – Top 5 Completions
Below is a summary of our Top 5 teams, the completion times, and the corresponding country. Each of the Top 5 teams came from a different country showing skills and interest in OT security around the globe. Our winning team, ukatemi, comes from Hungary and they completed all 42 challenges in record speed. They gained all 18,700 possible points within 8 hours and 55 minutes after opening the CTF.
- ukatemi – 8 hours (h), 55 minutes (m) [Hungary]
- DragoslayerSG – 22h, 52m [Singapore]
- OTóż to – 25h, 42m [Poland]
- CyberSpider – 26h, 1m [USA]
- H4ckiliner – 27h, 49m [Germany]
Below we highlight the top 10 teams and the scores achieved.
A Breakdown of Challenges
We received over 500 support requests via the Discord support server during the CTF event. All requests were handled and solved by the Dragos’s team – from simple formatting issues to helping debug flawed PLC code on the player’s side.
The challenge that had the least number of solves was in the PLC Programming category. This is no surprise since it was a very novel category and new to many players.
The challenges that had the highest number of solves were in the Phishing E-Mail category. This was expected, since phishing is the Initial Access in many intrusions. It is also common for players to have good skills in analyzing these types of e-mails . A few statistics about our flags show that the most difficult challenge was only solved by one out of every 33 teams. The easiest flag though was solved by 3 out of 4 teams registered for our CTF.
Here’s a quick list of most and least solved flags in this year’s CTF.
| MOST SOLVED FLAGS | LEAST SOLVED FLAGS |
|
|
Sign up for Dragos CTF 2023!
Ready to put your insights into action?
Take the next steps and contact our team today.

