It’s 2 AM, and your night-shift network security analyst has just received an alert. A computer on the IT network has transferred a suspicious executable to an engineering workstation inside your ICS network. Your analyst has solid training in IT security, but she is new to ICS operations, and she’s uncertain what the potential implications of this behavior might be in an industrial environment. The rest of her team is sound asleep. Now what?
Effective knowledge transfer can be a tricky problem. IT and ICS security professionals often have a different frame of reference and set of skills, and they each may be faced with problems in either realm at inopportune times and under significant pressure. In the most stressful situations, effective training and well-documented processes and procedures are absolutely essential to reliable and uniform response.
So how do we help your analyst in the scenario above? She’s already a well-trained IT security professional, but she needs some help performing analysis in the ICS environment. In a best-case scenario, a specialist in ICS security has written some guidance for her to follow. These playbooks instruct her to gather and analyze relevant data, how to triage the alert, and how to determine if the activity monitored was malicious or benign.
A good security operations environment provides playbooks for many tasks – both routine and emergency. Not only does this aid each analyst in performing tasks they have less expertise in, but it ensures every analyst completes tasks uniformly and can reach a similar conclusion. Playbooks are tools which help security analysts perform their job in a consistent way, while learning more about IT and ICS security in the process.
The Dragos Platform places a heavy focus on playbooks for both hunting and incident response. We endeavor to avoid a scenario in which we tell a customer’s analyst that something is “strange” or “wrong,” yet fail to provide context or applicable next steps. Each threat hunting or incident response case opened in the platform may be loaded with one or more playbooks. Individual threat behavior analytics fire in the platform and are tied to specific playbooks, which aid analysts in response and investigation.
In addition to new analytics, our experienced Threat Operations Center team provides a new set of playbooks with each content pack release for the Dragos Platform. Of course, we understand that every operational environment has its own nuances and internal procedures, so we make it simple for customers to add and modify playbooks as they deem appropriate via the platform’s playbook app.
So, what exactly does a playbook in the Dragos Platform contain? At the most basic level, it contains a step-by-step list of directions. To account for varying experience levels, each step may be expanded to show more detailed help in performing the directed action. Playbooks may also link to relevant event data, query-focused data sets (we’ll be discussing these in an upcoming blog!), or asset information, which may be useful in conducting analysis. The end goal is to provide as much concise guidance and education to any analyst using our platform as possible.
In our recent blog, “Threat Analytics and Activity Groups,” Joe Slowik detailed several analytics implemented in the Dragos Platform which may be indicative of known adversary behaviors. For example, one analytic associated with DYMALLOY threat actor group activity detects screenshots transferred out of an ICS network. (This is noteworthy because an adversary may be conducting reconnaissance on ICS devices.) While it is essential to notify analysts that this behavior has occurred, they may not understand the potential risks involved, or how to triage the event. This is where the playbook associated with this analytic comes into play. It instructs the analyst to perform a series of tasks:
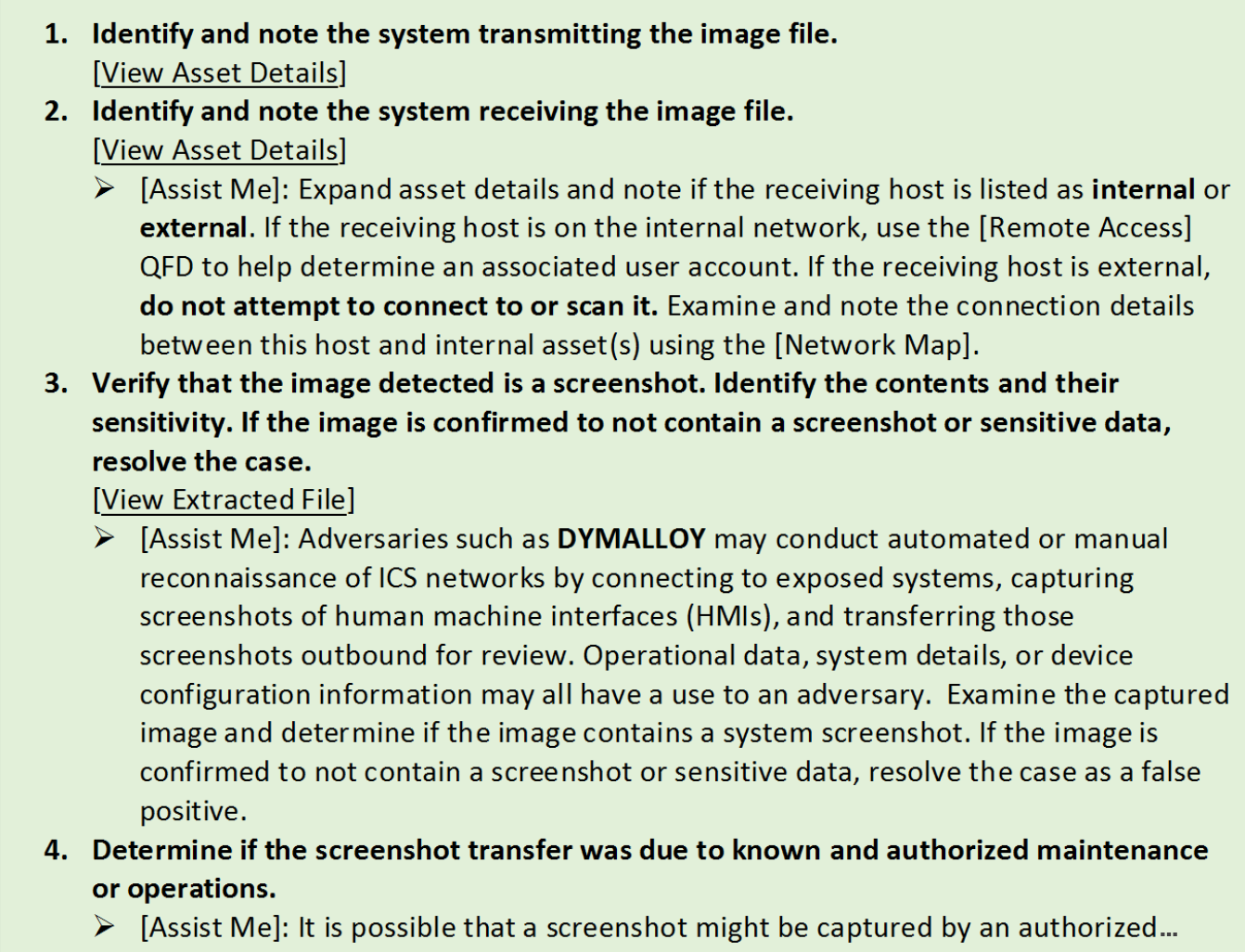
As you can see, not only does the playbook provide links to relevant evidence and system details, it also provides additional elaboration on tasks on request. If an analyst is confused about why they are performing a task, or needs tips on how best to perform it, he or she can expand the task to get additional help.
Security Operations in any industry can be stressful work – even more so in industrial environments that provide the services which civilization relies on. It’s incredibly important security analysts be provided with good training and comprehensive tools like playbooks to help them perform their best.
Ready to put your insights into action?
Take the next steps and contact our team today.
