It’s hard to believe our fourth annual Dragos Capture the Flag (CTF) is already behind us! Each year we continue to show steady participation from around the globe. I’m always amazed by the number of countries and cities represented by our participants. This year’s event proved no different in the broad representation of international cybersecurity professionals and too seeing many repeat teams or participants joining our annual CTF.
Dragos creates and hosts an annual CTF competition focused on industrial control systems (ICS) and operational technology (OT) designed to test all cybersecurity skill levels, from first time participant to seasoned veteran. The Dragos CTF competition is aimed to educate folks on both common and sophisticated OT tactics, techniques, and procedures (TTPs). Cybersecurity best practices are defined and implemented based on well-known frameworks that are driven home by defensive capabilities. In the offensive world, we refer to this as the “Blue Team,” but the other side that most folks haven’t really had time to play around with is known as the “Red Team.” The Red Team approaches cybersecurity by pushing the limits on networks, domains, applications, and general configurations to identify misconfigurations that could be leveraged by adversaries to exploit a specific target.
Dragos designs our annual CTF competition to give both teams (Blue and Red) an opportunity to educate themselves on common and uncommon offensive TTPs. Learning firsthand what threats might be being used to infiltrate a target environment only helps the Blue Team get stronger.
Check out our OT Cybersecurity Fundamentals blog series to discover more about the distinct challenges of securing operational technology.
Learn MoreWhat Is Capture the Flag?
A Capture the Flag (CTF) event is a great way for cybersecurity practitioners to learn, practice, and develop new skills and knowledge in tackling specific security challenges they may encounter on the job. These skills and knowledge not only apply to red-teamers acting as adversaries in simulated events to test detection and response capabilities, but also apply to blue-teamers playing as the defenders protecting critical assets.
The CTF security challenges are often designed to make participants think outside the box to help develop a deeper understanding of accessible/non-accessible ports, network protocols, and network communications and often leverage user or system misconfigurations.
How the Dragos Capture the Flag Is Created
Before showing the results of this year’s competition, let’s take a step back and describe what it took to deliver you the 2024 Dragos CTF challenge. In the following sections, I’ll explain how we exchanged ideas and how those ideas became the unique challenges for this year’s CTF.
Step 1 – Build a CTF Team
The Dragos CTF is impossible without a team that creates the overarching story, develops challenges, tirelessly tests and validates each scenario to ensure the game flows as expected. Each CTF team member volunteers their time to help make this event possible, and without them the event won’t happen. Thank you to everyone who went above and beyond to make this event possible.
Step 2 – Develop the Comprehensive Story
The CTF team’s first task is to create a story to connect all the OT cybersecurity challenges. The story completion provides the first milestone for the CTF project, allowing Dragos professionals from Services, Intel, Malware Analysis, Customer Success, and more to provide specific ideas for the challenges within certain boundaries. Every idea was evaluated to ensure that it was relevant, fun, and accessible to participants with different experiences and skills. This year, the CTF storyline centered on our annual Dragos Industrial Security Conference (DISC) theme, Back to the Future, specifically on the fictional threat group, Biffs-Budds.
Step 3 – Develop a Realistic MITRE ATT&CK for ICS Path
The fourth edition of the Dragos CTF continues its focus on industrial control systems (ICS) security. We attempted to improve the understanding of the five critical controls for ICS/OT cybersecurity identified by the SANS Institute by exploring multiple scenarios designed to test participants in both offensive and defensive perspectives. Similar to last year, we built this year’s challenge leveraging the MITRE ATT&CK for ICS Kill Chain, including stage 1 and stage 2.
Additionally, we wanted to expose all participants to challenges not found in traditional CTF events that typically only highlight IT security challenges. We followed the fictitious adversary Biffs-Budds through their attack that started with initial access and discovery through to collection, lateral movement, and ultimately pivoting into the ICS environment. Once in the ICS environment, the threat impacted the processes, cutting power to Doc’s time machine by using the following MITRE ATT&CK Navigator:
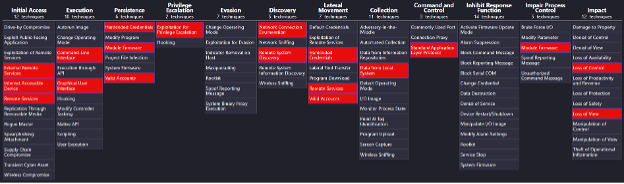
Step 4 – Assess the Feasibility
Once the storyline was accepted, the CTF team evaluated its feasibility to be solved in a CTF environment before building the corresponding artifacts. We needed to think beyond the game content and look at the context from the player’s perspective. We started conceiving ways to expedite the artifact delivery and minimize the chances of misconfigurations. This analysis resulted in the files bundled to download during the challenge. Our purpose was to ensure that artifacts were not interfering with the player’s ability to solve the challenge and that, for a majority of the time, the focus was on the challenge and not the tools. Once we got all artifacts for the different challenges created, we satisfied the second milestone of the project.
Step 5 – Test & Validate (Again, Again, and Again)
The final part in building the CTF consisted of validating and verifying each challenge to be deployed. More Dragos professionals joined the project and ensured that the challenge descriptions, artifacts, hints, and flags were correct, fair, and solvable. After reviewing all 37 challenges, the team started the CTF deployment and conducted a final test before finalizing the competition. It was the fifth and last milestone, meaning we were ready (as much as we’d ever be) for the competitors to join.
Step 6 – Supporting Dragos CTF Participants
Dragos uses Discord, a third-party direct messaging solution, to communicate with individual participants so as not to reveal solutions or hints to other participants that did not request them. Depending on the difficulty of the challenge and the level of progress, the Dragos CTF support team aided in helping participants find the right starting point, the right answer format, or provided general guidance on how to approach a question. Throughout the CTF event, the support team responded to close to 1000 support requests!
2024 Dragos CTF Competition Summary
Now let’s look at who participated in our CTF competition this year and get a breakdown of how well all participants performed and who were the top 5 leaders. Let’s dive in!
Dragos CTF Player Demographics
OT security is a global topic and that was represented by our players. Dragos identified participants competing from around the world, specifically, 74 countries and 822 cities. In addition to the expected strong competition from North America, Europe, and Asia, Dragos noted that other continents (Australia, Africa, and South America) put forward a strong showing, demonstrating their skills across all challenges.
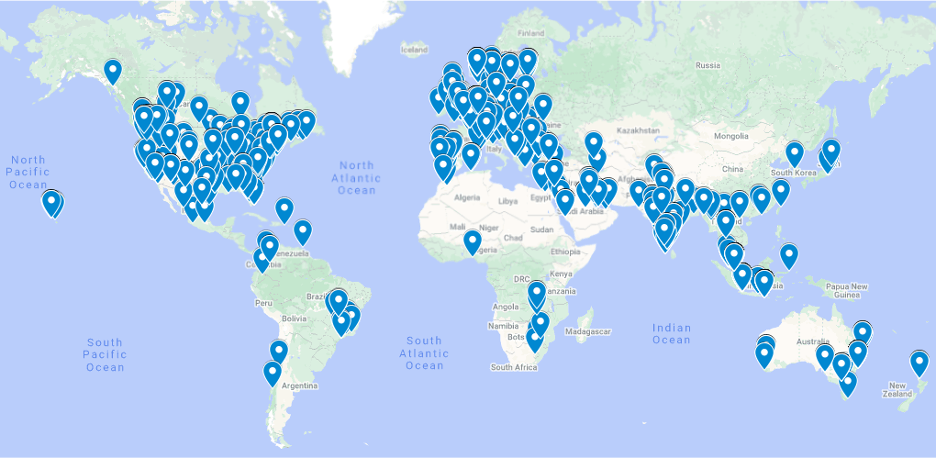
At the end of the 48-hour challenge, only two teams succeeded in completing all challenges in the competition. Many teams showed impressive motivation and exceptional skills in solving our challenges and the feedback shows that we hit the mark – not too easy, not too hard, and not unfair. An overall good mix that our players enjoyed.
Dragos CTF Challenge Breakdown
The Dragos support team received a significant number of support requests via the Discord support server during the CTF event. All requests were handled and solved by the Dragos team – from simple formatting issues to helping individuals learn the nuances of an OT protocol created just for the challenge!
The CTF team puts a lot of focus on challenge scalability to ensure all skillsets are able to participate in the competition. This starts with a large number of Easy and Normal skill level challenges. Together, the Easy and Normal skill level challenges consisted of close to 80 percent of all solves! On the contrary, the Expert and Extreme skill level challenges only accounted for about 6% of all solves (sorry)!
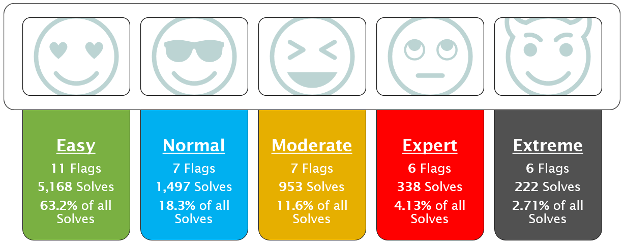
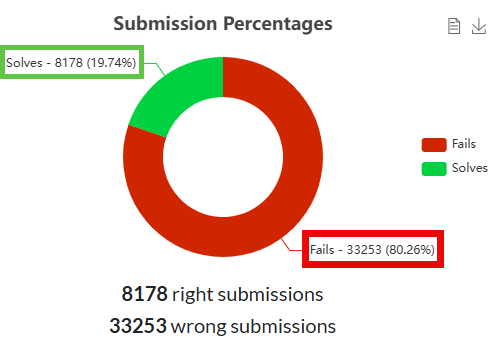
The numbers above only include correct challenge submissions. The CTF event saw a total of 8,178 correct submissions, but we noted a total of 33,252 incorrect submissions. This accounts for 80.26 percent of all challenge submissions.
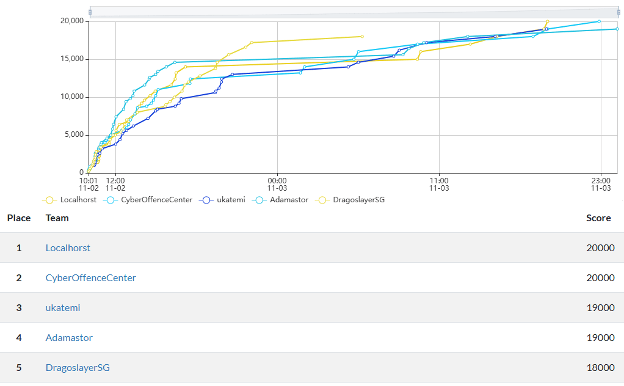
Dragos CTF Leaderboard
819 teams (consisting of 1,249 participants) started the 2024 CTF challenge on an even playing field. When the event concluded 48 hours later, only two teams had completed all 37 challenges (worth a total of 20,000 points). This goes to show how difficult some of the final challenges were, and only one or two unsolved challenges separated first and fifth place teams.
- 1st Place – Localhorst from Germany with 20,000 points. Completing all challenges, with no hints taken, in 33 hours, 3 minutes.
- 2nd Place – also from Germany, CyberOffenceCenter with 20,000 points. Completing all challenges, with no hints taken, in 36 hours, 53 minutes.
- 3rd Place – from Hungary (and last year’s winner), ukatemi with 19,000 points.
- 4th Place – from Portugal, Adamastor with 19,000 points.
- 5th Place – from Singapore, DragoslayerSG with 18,000 points.
Thanks to All Who Participated!
The CTF team would like to thank everyone who took time out of their weekend to participate in the competition, this is not lost on us. The Dragos CTF team loves watching both new and experienced folks play the game; no matter if you solve one or 30 challenges, the key point is learning new concepts and hopefully gain a deeper understanding of OT-specific TTPs. Thank you all for playing and we look forward to Dragos CTF 2025!
Want to Learn More About OT Cybersecurity?
Download this no-nonsense guide to operational technology (OT) terms and OT cybersecurity concepts for IT security pros who want to help their firms bolster the security around their critical infrastructure.

Ready to put your insights into action?
Take the next steps and contact our team today.

