Ransomware continues to be one of the most threatening financial and operational risks to industrial organizations worldwide during the third quarter of 2022. Last quarter, Dragos assessed with high confidence that Q3 would witness an increase in ransomware groups’ evolving activities, the disruption of industrial operations, and the appearance of new or reforming ransomware groups. The assessment remains correct, except that Dragos is unaware of any significant industrial disruptions in Q3.
Dragos is aware of multiple new ransomware groups targeting industrial entities during Q3, like SPARTA BLOG, BIANLIAN, Donuts, ONYX, and YANLUOWANG. Until now, Dragos cannot confirm if these groups are reformed from other dissolved ransomware groups, such as Conti, who shut down their operation last quarter. In addition, Dragos observed ransomware trends tied to political and economic reasons, such as the conflict between Russia and Ukraine and Iranian and Albanian political tensions. Dragos observed another trend related to the global crisis of energy supplies and prices, which may have caused Ragnar Locker, AlphaV and possibly other ransomware groups to increase their activities targeting Energy sectors.
Dragos monitors and analyzes the activities of 48 different ransomware groups that target industrial organizations and infrastructures. Dragos observed through publicly disclosed incidents, network telemetry, and dark web posting that out of these 48 groups, only 25 have been active during Q3 of 2022. Dragos is aware of 128 ransomware incidents in the third quarter of 2022 compared to 125 in the previous quarter. The Lockbit ransomware family account for 33% and 35% respectively of the total ransomware incidents that target industrial organizations and infrastructures in the last two quarters, as the groups added new capabilities in their new Lockbit 3.0 strain.
Anti-detection mechanisms, anti-debugging, and disabling Windows defenders are among the features that make Lockbit one of the fastest growing ransomware strains. Last month, an unknown person claimed he had hacked Lockbit servers and leaked Lockbit 3.0 builder, allowing anyone to create ransomware. Dragos assesses with moderate confidence that Lockbit 3.0 will continue to target industrial organizations and pose threats to industrial operations in the last quarter of 2022, whether by the Lockbit gang itself or others who can create their own version of the Lockbit ransomware.
Dragos analyses ransomware variants targeting industrial organizations worldwide and tracks ransomware information via public reports and information uploaded to or appearing on dark web resources. By their very nature, these sources report targets that allegedly pay or otherwise “cooperate” with the criminals. There is, however, no 1:1 correlation between total targeted attacks and those attacks that elicit victim cooperation. Our breakdowns of ransomware activities for this quarter are as follows:
Ransomware By Region
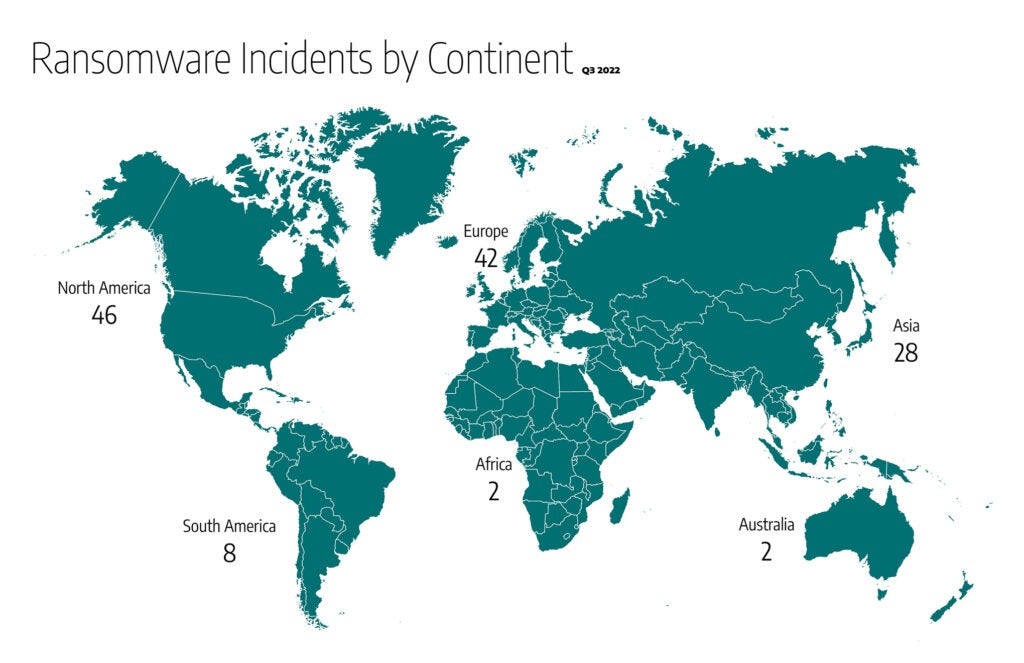
Globally:
- Thirty-six percent of the 128 ransomware attacks target industrial organizations and infrastructures in North America, for a total of 46 incidents, as shown above.
- Europe comes in second with 33 percent, 42 incidents.
- Asia with 22 percent or 28 incidents.
- South America with 6 percent, or 8 incidents.
- Africa and Australia with 2 percent each, 2 incidents each.
Noticeably, the percentage of reported cases in North America jumped to 36 percent compared to 26 percent in the last quarter. The increase in ransomware activities in North America could be tied to the current global political and economic situations.
Ransomware By Sector & Subsector
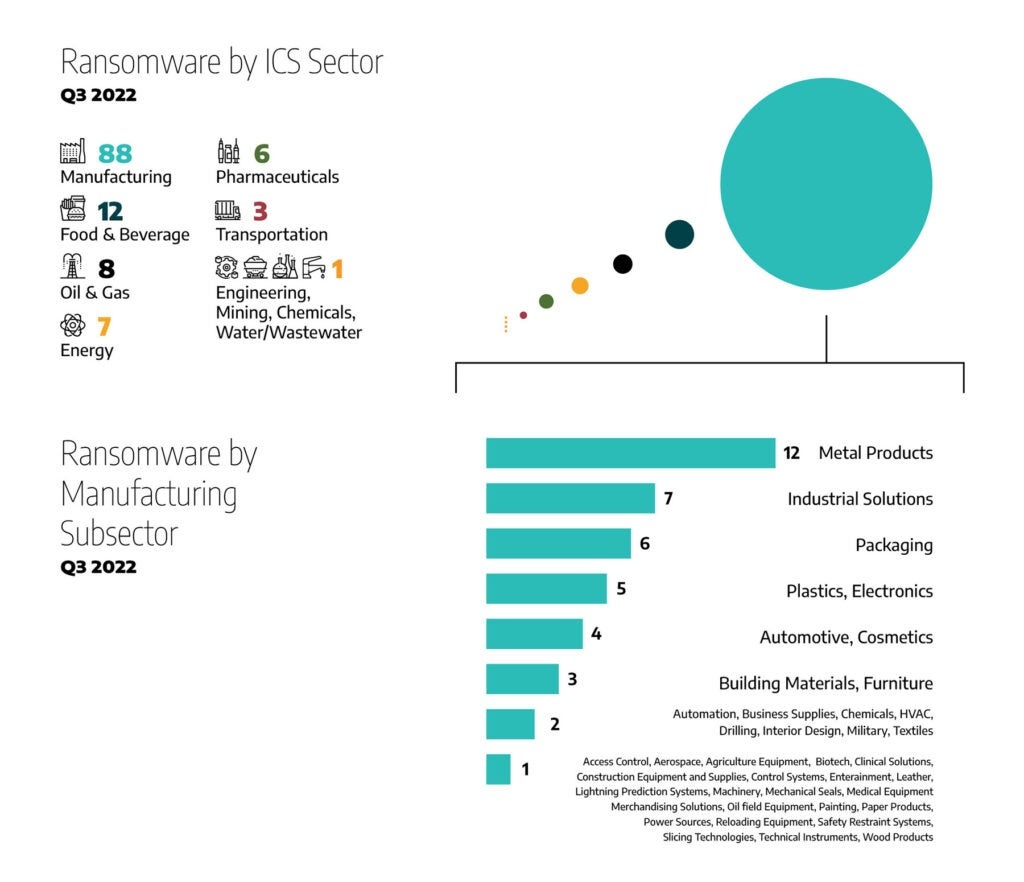
Figure 2 above shows that 68 percent of ransomware attacks target the manufacturing sector (88 incidents), the same percentage reported in Q2. Nine percent of attacks targeted the food and beverage sector (12 incidents) compared to eight percent in the last quarter. The oil and natural gas sector was targeted with six percent of the attacks (8 incidents) and the energy and pharmaceuticals sectors with 10 percent of attacks, with seven and six incidents respectively. The sectors of chemical, mining, engineering, and water and wastewater systems were targeted with one percent or one incident each.
The ransomware attacks that Dragos tracked this quarter targeted 40 unique manufacturing subsectors. These manufacturing subsectors break down as follows.
- 14 percent of victims were in metal products manufacturing (12 incidents).
- 8 percent were in industrial solutions (7 incidents).
- 7 percent were in packaging, 6 incidents.
- The Electronics and semiconductor manufacturing sectors and plastic accounted for 6 percent of attacks each, 5 incidents each.
- Automotive and cosmetics each made up 10 percent of incidents, 4 incidents each.
Ransomware by Groups
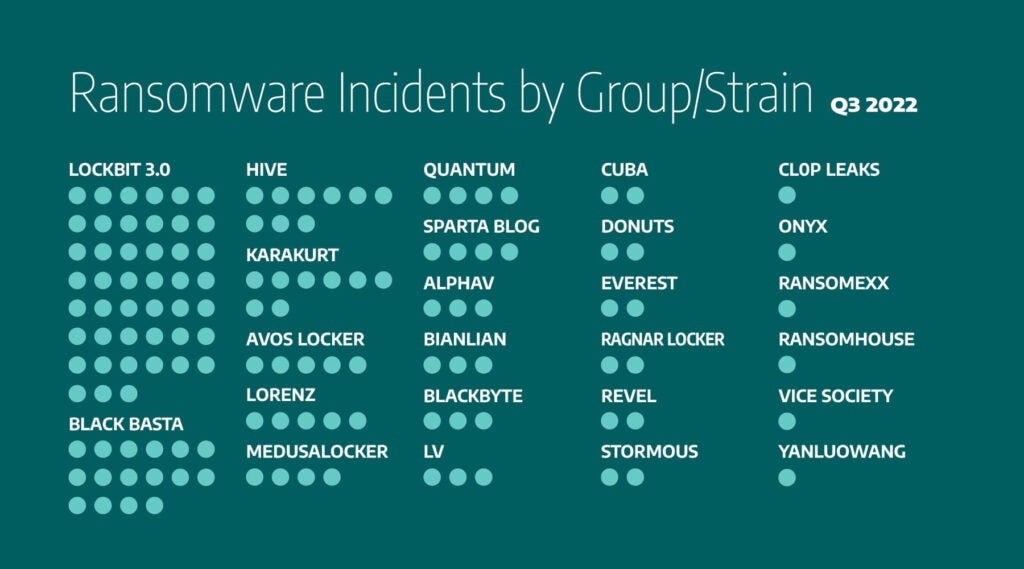
Analysis of ransomware data shows Lockbit 3.0 made 35 percent of the total ransomware attacks in Q3, accounting for 45 incidents; Black Basta comes in next with 11 percent (16 incidents); Hive made 7 percent (9 incidents); KARAKURT made 6 percent (8 incidents); Avos Locker and Lorenz made 5 incidents each or 4 percent. Lockbit 3.0 maintained the same level of operation as Lockbit 2.0 last quarter. Ransomware attacks against manufacturing entities also impact other sectors that depend on manufacturers in their operations or supply chain, such as aerospace, food and beverage, and automotive organizations.
Ransomware Victimology Trends
During Q3 of 2022, Dragos continued to observe trends in the victimology of ransomware groups. This does not, however, determine the permanent focus of these groups, as victimology can change over time. Three more ransomware groups were observed targeting industrial sectors and regions of the world in this last quarter than in Q2 of 2022. Based on our analysis of the Q3 2022 timeframe, Dragos observed that:
- Ragnar Locker has been targeting mainly the Energy sector.
- Cl0p Leaks has been targeting only Water and Wastewater sector.
- KARAKURT has targeted only manufacturing in Q3, while in Q2, it only targeted transportation entities.
- Lockbit 3.0 is the only group that targeted chemicals, drilling, industrial supplies, and interior design.
- Stormous has only targeted Vietnam.
- Lorenz has only targeted the United States.
- Sparta blog has only targeted Spain.
- Black Basta and Hive targeted the transportation sector.
The groups we observed in Q2 but not in Q3 are: Lockbit 2.0, Conti, Snatch, Moses staff, Midas leaks, pandora, and Suncrypt. The following groups were observed in Q3 but not in Q2: Lockbit 3.0, Cl0p Leaks, Medusalocker, Sparta blog, BIANLIAN, DONUTS, ONYX, Revil, and YANLUOWANG.
What’s Next?
In Q4 of 2022, Dragos assesses with high confidence that ransomware will continue to disrupt industrial operations, whether through the integration of OT kill processes into ransomware strains, flattened networks allowing for ransomware to spread into OT environments, or through precautionary shutdowns of OT environments by operators to prevent ransomware from spreading to OT systems. Due to the changes in ransomware groups and the leaking of the Lockbit 3.0 builder, Dragos assesses with moderate confidence that more new ransomware groups will appear in the next quarter, as either new or reformed ones.
Ready to put your insights into action?
Take the next steps and contact our team today.
