In the fourth quarter of 2021, Dragos assessed with high confidence that ransomware would continue to disrupt OT operations into 2022.1 So far in Q1 2022, that assessment holds true. While Dragos does not have substantive evidence that the quantity of ransomware incidents has increased over last year, a recent surge of ransomware initial access campaigns show that specific ransomware groups like Conti are more active this year than last.2,3 Additionally, several globally significant events indicate ransomware may pose a greater risk for operational disruption and impacts than it did last year. This blog looks at ransomware targets by region, industry sector and ransomware group in the first quarter of 2022.
First among these risk-changing events is the Russian invasion of Ukraine on 24 February, 2022, which increased the likelihood of impactful cyber activity related to both industrial infrastructure of the combatants and, arguably, the industrial infrastructure of material supporters of those parties in conflict. The infamous Conti ransomware group declared alignment with the Russian Federation via their Dedicated Leak Site (DLS) and threatened that if a cyber-attack or other warfare were directed by any entities against Russia they would use “all possible resources to strike back at the critical infrastructure of an enemy.”4 The Arabic speaking ransomware group Stormous also announced its support for the Russian government.5
The relatively unsophisticated, but effective, tactics of the LAPSUS$ theft extortion group demonstrated that even the largest organizations with mature information security regimes are at risk of intrusion and exfiltration. In March LAPSUS$ posted screenshots of internal software tools tied to a number of major corporations, including Vodafone, NVIDIA, and Samsung. It also publicly announced that it had stolen source code from Microsoft. Dragos assesses with low confidence that the LAPSUS$ intrusions may influence ransomware actors to adopt similar techniques that are more resistant to anti-malware defenses. Dragos is aware of anti-malware resistant Conti ransomware campaigns in April 2022 that ostensibly improve upon their hybrid social engineering call center-based infection campaigns that took place in 2021.6
Dragos analyzes ransomware variants targeting industrial organizations worldwide and tracks ransomware information via public reports, and information uploaded or appearing on dark web resources. These sources by their very nature under report targets that pay or otherwise “cooperate” with the criminals and therefore do not match 1:1 with incidents.7,8,9
Even though the number of ransomware attacks and dark web postings in the first quarter of 2022 is slightly less than the number in Q4 2021, the impacts of these ransomware attacks are larger. Noticeably, ransomware attacks disrupted the operations of multiple giant organizations, their suppliers, and subsidiaries. An example of such disruption is the possible Conti-related ransomware attack in February 2022 that targeted Kojima Industries Corp, which supplies Toyota’s plastic parts and electronic components.10,11 The incident suspended Toyota plant operations for several days. Concurrently, Dragos observed internet telemetry of a common Conti-controlled Emotet Tier 2 node in Command and Control (C2) with networks of several other global automakers.12 A ransomware attack by the Hive group in March of 2022 partially impacted some of the services of Rompetrol, a Romanian oil firm.13 In February, security researchers at Crowdstrike discovered a ransomware variant called “HermeticRansom” with destructive capabilities targeting multiple Ukrainian entities.14 Dragos assesses with moderate confidence that adversaries will use HermeticRansom to target other entities.
Ransomware By Geographic Region
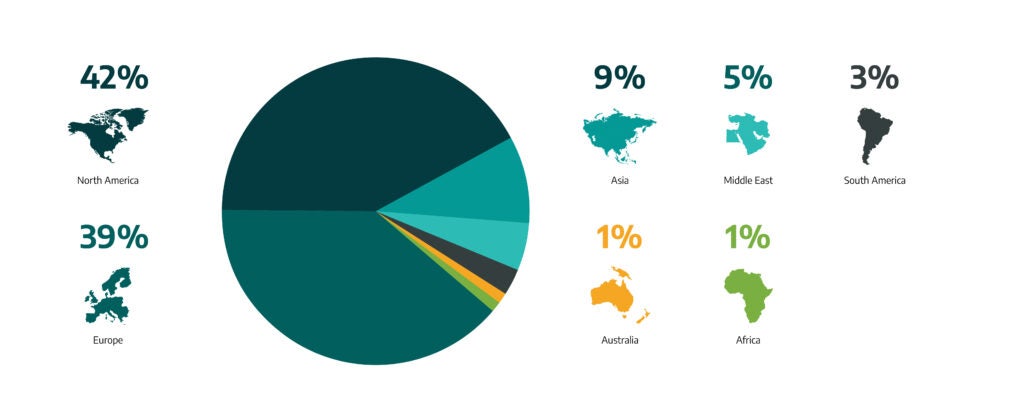
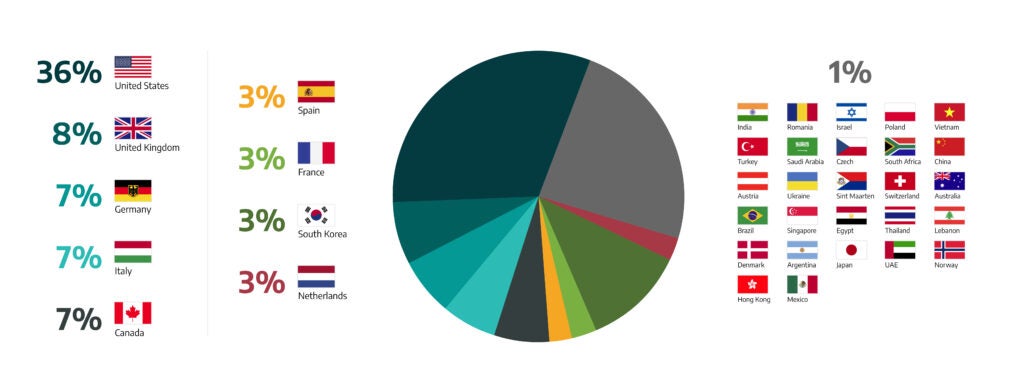
Figure 1 above tracks Ransomware targets by continent and shows that 81 percent of all attacks targeted Europe and North America. Globally, 45 percent of the ransomware attacks target industrial organizations and infrastructure in North America (36% of that in the U.S.); Europe comes second with 41 percent; Asia with 10 percent; the Middle East with 6% percent; South America with 2 percent; and 1% for Africa and Australia tied for 1 percent. The U.S. was the most targeted country for ransomware with 36% followed by the UK with 7% of all targeted attacks. Figure 2 below shows an overall breakdown by country. After the Netherlands at 3% all of the others had 1% of targeted attack efforts. This is shown in Figure 2 below.
Ransomware Attack Targets By Sector
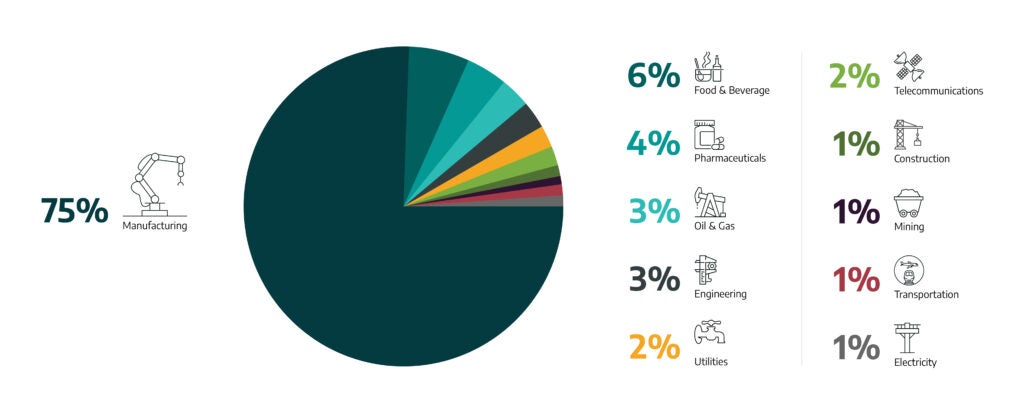
As Figure 3 below shows, 75 percent of all ransomware attacks that Dragos tracked in Q1 2022 targeted the manufacturing sector. Six percent of these attacks targeted the food and beverage sector, 4 percent targeted pharmaceuticals, 3 percent targeted oil and natural gas, 3 percent targeted engineering. Two percent targeted utilities and 1 percent targeted mining.
Targeted Ransomware Attacks by Group
Dragos analyzes and monitors the activities of 37 ransomware groups that targeted industrial organizations and infrastructure. Dragos observed through publicly disclosed incidents, network telemetry, and dark web postings that out of these 37 groups only 22 groups have been active during Q1 2022.
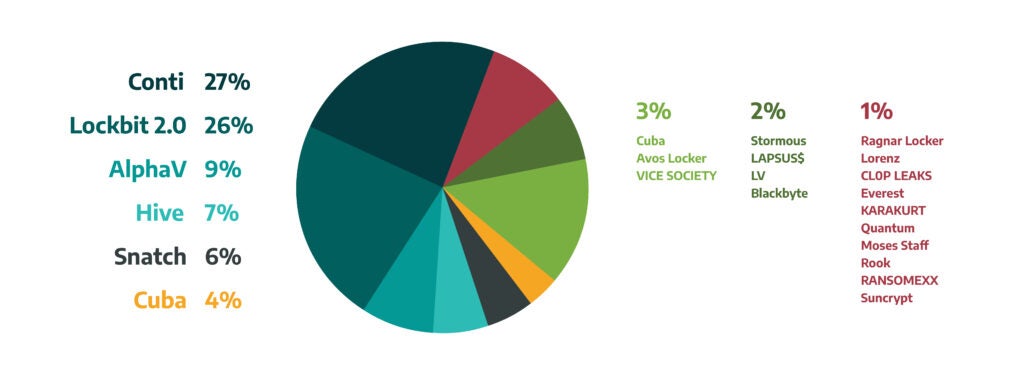
Dragos’s analysis of ransomware data shows Conti made 27 percent of the total ransomware attacks in Q1; Lockbit 2.0 comes next with a 26 percent; AlphaV, also known as BlackCat, made 9 percent; Hive made 7 percent (see Figure 4). Conti and Lockbit 2.0 maintained nearly a similar percentage of the total ransomware incidents compared to the last quarter of 2021. Whereas the Conti and Lockbit 2.0 groups continue to target different vertical markets, most of their victims are within the manufacturing sector. Attacks against manufacturing entities often impact other sectors that depend on manufacturers in their operations or supply chain such as, aerospace, food and beverage, and automotive organizations.
During Q1 of 2022, Dragos observed trends in the victimology of the ransomware groups. This does not, however, determine the permanent focus of these groups as victimology can change over time. Based on our analysis of the Q1 2022 timeframe Dragos observed that:
- Suncrypt and Quantum have been targeting only Food and Beverages entities.
- RansomeXX and Rook have been targeting only Pharmaceuticals.
- The utilities sector has been mainly targeted by Avos Locker and Blackbyte.
- The telecommunications sector has been mainly targeted by LAPSUS$.
- Lorenz, LV, Moses Staff, KARAKURT, CL0P LEAKS, Ragnar Locker, and Stormous have only targeted organizations within the manufacturing sector.
What’s Next?
As Dragos continues to analyze and monitor the activities of ransomware families targeting industrial organizations, we have published multiple valuable reports and blogs in Q1 2022. Dragos published a technical report on the analysis of Lockbit 2.0 Ransomware and a blog on Conti ransomware activity in the auto manufacturing sector.15,16 In addition, Dragos has discussed ransomware threats in multiple industrial and regional threat perspective reports.
In Q2 of 2022, Dragos assesses with high confidence ransomware will continue to disrupt OT operations, whether through the integration of OT kill processes into ransomware strains, flattened networks allowing for ransomware to spread into OT environments, or through precautionary shutdowns of OT environments by operators to prevent ransomware from spreading to OT systems. Dragos assesses with moderate confidence ransomware with destructive capability will continue to target OT operations, and that the political tension between Russia and western countries will only exacerbate this.

References
- Dragos ICS/OT Ransomware Analysis: Q4 2021 – Dragos
- Cyberattacks are Prominent in the Russia-Ukraine Conflict – Trend Micro
- Emotet Redux – Black Lotus Labs
- Conti’s allegiance to Russia could help the ransomware gang avoid capture – Tech Monitor
- STORMOUS ransomware gang has officially announced…- DarkTracer via Twitter
- BazarCall Method: Call Centers Help Spread BazarLoader Malware – Palo Alto Unit 42
- AA-2022-07: Conti Threatens Western Critical Infrastructure – Dragos
- CISA, FBI, NSA AND INTERNATIONAL PARTNERS ISSUE ADVISORY ON RANSOMWARE TRENDS FROM 2021 – CISA
- UK Charges Alleged Lapsus$ Gang Members With Hacking – SecurityWeek
- TR-2022-05: Conti Gains Footholds in Automotive Organizations – Dragos
- AA-2022-10: Toyota Supply Chain Compromise and Operational Disruption – Dragos
- Suspected Conti Ransomware Activity in the Auto Manufacturing Sector – Dragos
- Hive ransomware gang targets Romanian oil firm in its latest cyberattack – The Record
- Decryptable PartyTicket Ransomware Reportedly Targeting Ukrainian Entities – CrowdStrike
- TR-2022-02: Analysis of Lockbit 2.0 RansomwareTechnical Report – Dragos
- Suspected Conti Ransomware Activity in the Auto Manufacturing Sector – Dragos
Ready to put your insights into action?
Take the next steps and contact our team today.
