The media focuses most of its attention on information security threats that originate outside of an organization. Whether it is the discovery of a new Advanced Persistent Threat (APT) or a company breach, generally one considers this to be a threat from someone from outside of the company, an outsider. And it is true, there are many outsider threats in any secured environment – natural disasters, hackers, terrorists, hacktivists, organized crime groups, etc. However, insider threats play a much larger role than most people realize.
Security experts consider insider threat to be a well-known phenomenon, and one that many regard as the greatest threat to any security environment. Edward Snowden, WikiLeaks, and Vault7 are prime examples of insider threats. Employees intentionally or unintentionally account for a significant portion of the threats to information assets in organizations.
It is not easy to profile insider threat adversaries. They may or may not have financial motivation. They may conduct their malicious activities out of anger, frustration, or whim. Employers may use polygraph examinations and many mathematical modeling techniques for insider threat detection, with varying degrees of success.
This blog and its accompanying whitepaper, “An Intelligence Perspective on Insider Threat and the Unique Role It Plays in ICS Environments,” focus on the spectrum of insider threats and how they specifically relate to industrial environments. It examines the emergence of a new type of insider threat: software and supply chain services. For a synopsis of this groundbreaking research, read on.
Industrial Control Systems (ICS) Environments and Cybersecurity
Some recent trends are adding fuel to the insider threat fire.
- Digital Transformation and the Purdue Model: ICS environments comprise operational technology (OT) and Information Technology (IT). The digitization of once analog devices and the integration of those devices into existing OT frameworks has created advances in automation and efficiency. The explosive growth of smart objects and their dependency on wireless technologies for communication increases the vulnerability to cyber attacks. The integration of physical devices (part of the ICS) with business functions (part of IT) through multiple layers of OT and IT technology is frequently described using the Purdue Model. The Purdue Model describes the logical sections of a physically divided and integrated IT and OT network. Of particular interest to this analysis are those insiders (employees) who understand the intricacies of Levels 0-3 of the Purdue Model.
- The Work from Home Model: Prior to work-from-home arrangements becoming the dominant pattern of employment since the Covid-19 outbreak in March 2020, employees reported to work and monitored and managed processes and controls from inside the plant. The work from home modality has enabled many employees to connect through the IT portions of the Purdue Model Levels 4 and 5 through to the lowest control layers (Levels 0-3).
- The Increasing Prevalence of Data Leaks: Data leaking during the last 10 years has become a major issue for U.S. intelligence organizations. Revelations from WikiLeaks and the Vault7 leaks are just a few examples. Even today so-called dark websites pose a serious threat to the security of any organization. Recently, personally identifiable information (PII) and other confidential corporate data have been dumped to dark websites as part of ransomware campaigns.
A New Description of Insider Threat: Software and Supply Chain
Software and supply chain dependencies pose a different kind of threat. Software is designed, marketed, sold, and trusted to do things like secure networks or keep track of secured assets. In some instances, it is the software that becomes an “insider” in that it is installed on systems. It is arguable whether software in critical organizational functions or in a supply chain that makes up some of the components of critical infrastructure control systems – such as programmable logic controllers (PLCs), diodes, or IED (independent electronic devices) – can be considered an “insider threat.” This supply chain software can be a pernicious type of insider threat that has yet to be fully considered. The SolarWinds incident is a prime example of this.
According to Business Insider, the SolarWinds breach was perpetrated through a software update. This type of supply chain attack is pernicious, and it exploits best practices by compromising an “insider,” in this case the software and vendor, to infect a company.
Manufacturing supply chain threats have access to extensive, in-depth knowledge of the operational technology in the plant, understand how processes should look, and knows the assets in the organization. This type of threat is unique because it represents a level of detailed knowledge that would otherwise be difficult to obtain from an outside perspective.
Supply chain espionage is much more complex and is sometimes governed by disparate manufacturing facilities and operations, sometimes spanning the globe, and multiple geo-political boundaries. Furthermore, malicious software may not have a discernible pattern of unusual behavior. Yet, its existence deep in organizations poses a serious threat to their operations.
Cyber Threat Intelligence and Insider Threat Detection
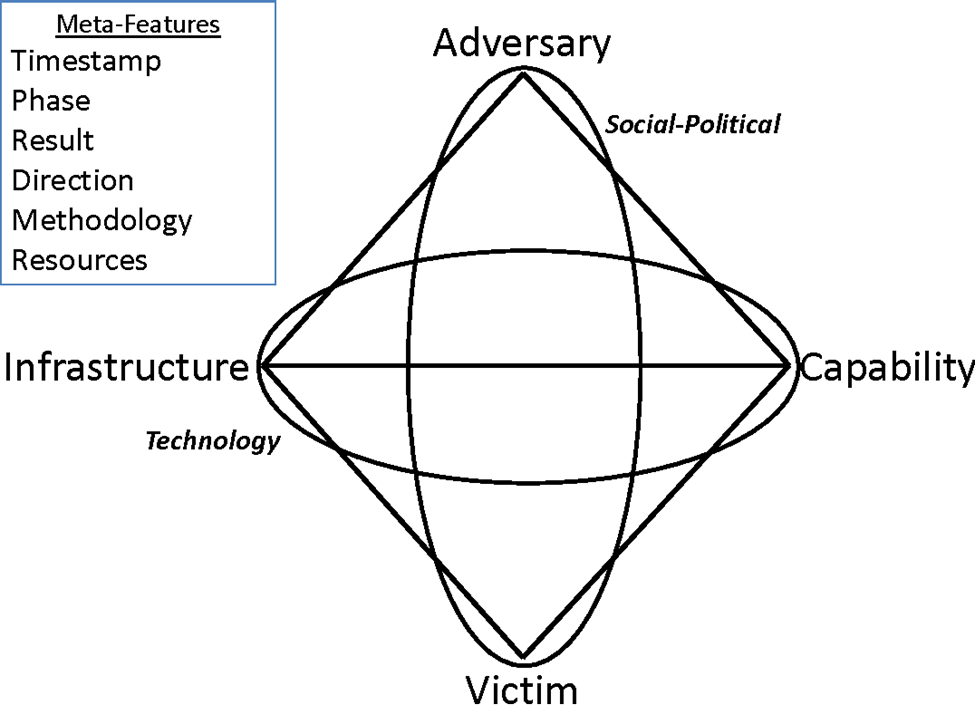
It is very complicated for cyber threat intelligence (CTI) mechanisms to detect insider threat or intent to commit fraud within an organization. For this, it’s best to consider the work of Caltagirone, Pendergast, and Betz (2013) regarding insider threats in the context of the Diamond Model of Intrusion Analysis, and the work of Wolfe and Hermanson (2004). This model can also help with the understanding of motivation and the various hidden elements such as victimology of the attacks, which is very useful for understanding intent and the predictive nature of how the attacks will evolve.
Conclusion
ICS environments provide fertile ground for insider attacks. Unlike IT environments, OT environments have specific hardware and software and can suffer catastrophic damage from endogenous or exogenous, insider-enabled attack vectors. Attacks on ICS environments require dedicated efforts in research, time, and access; thus, insiders play a unique role in the spectrum of espionage threats.
Insiders understand the processes, setpoints, controllers, and SCADA software as well as where the physical assets are located and the roles they play in the OT environment. This makes them excellent targets for exploitation.
Download our free whitepaper to learn more about:
- The impacts of supply chain espionage on ICS environments.
- The various motivations of insider threats and how to detect them in your network.
- The different threat types, kill chains, and how to apply Cyber Threat Intelligence models to your analysis.
- The specifics of ICS environments and what makes them unique in the analysis of insider threat.
- The cases of Snowden, SolarWinds, the Post Rock Rural Water District, and the Oldsmar Municipal Water district incidents, as recent examples of insider threats and about how they differ.
- What the literature shows about how to counter insider threats through education and behavioral analytics.
- Mitigation recommendations to decrease the impact of insider threats in your ICS environment.
Ready to put your insights into action?
Take the next steps and contact our team today.
