Ensure ICS Compliance with Cybersecurity Controls
Create simplified, repeatable processes to meet audit and compliance requirements faster and more accurately.
Automate Operational Technology Cybersecurity Controls
Industrial operators contend with regulations designed to protect the safety and reliability of critical operational technology (OT) assets. They’re also called to go above and beyond these non-negotiable compliance directives.
As complex as many regulations are, they still don’t provide an adequate level of protection to meet the OT risk tolerances of today’s industrial businesses. This is where OT cybersecurity frameworks and standards come into play. From C2M2 to NERC CIP, these frameworks and standards provide structured guidance for broadly tackling OT cyber risk.
Dragos provides the industrial cybersecurity solutions to help meet cybersecurity control requirements, including NERC-CIP, TSA Pipeline, US Federal BOD, EU NIS, KSA OTCC, and many others. Our cybersecurity solutions include our technology platform, threat intelligence, and expert services that enable industrial operators to navigate the most important cybersecurity compliance and standards requirements.
Mapping Dragos Solutions to Your Requirements
Discover how our technology maps to critical controls in specific cybersecurity frameworks, our expert services help operators assess current state and chart a path to a more effective OT security program, and our threat intelligence provides the insight into industrial threats and threat groups for proactive cyber defense.
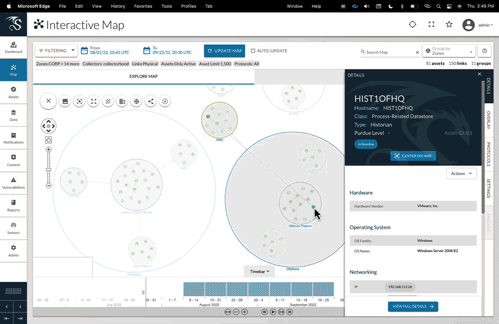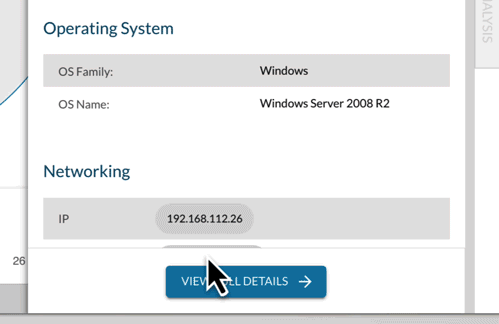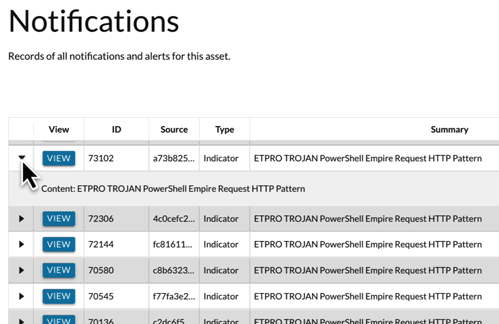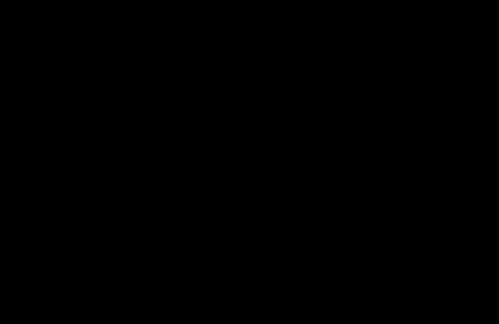
The Dragos technology platform provides visibility into OT systems to help fulfill compliance control requirements and reduce OT system risk.
- Regulatory Dashboards with asset inventories, events, and vulnerabilities – aligned with regulatory requirements
- Threat Detection – intelligence driven technology delivers most effective detection, validated by MITRE ATT&CK for ICS
- Incident Investigation – providing key forensic data and response playbooks to streamline incident response
- Vulnerability Management – with industrial-focused alternative mitigation and risk-based prioritization
Industrial cybersecurity experts to help with incident response, evaluate architecture, and advance your OT security program.
- Expert industrial responders to refine incident response plans, test those plans with tabletop exercises, and RESPOND on those worst days when you need expert assistance to investigate and resolve incidents
- Cyber industrial consultants to perform penetration tests, assess architecture and vulnerabilities, to baseline and help you create a plan to mature your program
Dragos WorldView Threat Intelligence delivers situational awareness into adversary activity and vulnerabilities that impact industrial sectors.
- Adversary research details the capabilities used to execute attacks in ICS/OT environments, and strategic intelligence reports cover regional and industry sector risks.
- Indicators of compromise (IOC) feeds provide an early warning of industrial threats to enhance SOC operations and investigations.
- Lab-tested malware and vulnerability analysis offers insight into the OT impact of a compromise and guidance on how to mitigate and respond.
Cybersecurity Regulations and Frameworks
Learn more about specific industrial cybersecurity regulations and frameworks and how Dragos can help your organization be in compliance.
| Regulation or Framework | Acronym | Description |
|---|---|---|
| Australian Security Legislation Amendment (Critical Infrastructure Protection) Act 2022 | SLACIP | The SLACIP Act amends the Security of Critical Infrastructure Act 2018 to include eleven industries, adds requirements adopting a critical infrastructure risk management program, adds definition for “Systems of National Significance” (SoNS), and enhances cybersecurity obligations for assets declared / registered as SoNS. Those obligations include incident response planning, cybersecurity exercises, vulnerability assessments, and access to system information. AESCSF Solution Brief |
| Cybersecurity Capability Maturity Model | C2M2 | Provides a framework to evaluate, prioritize, and improve cybersecurity risk management around IT and OT assets, including hardware, software, and information assets. C2M2 Solution Brief |
| Cybersecurity Maturity Model Certification | CMMC | The Cybersecurity Maturity Model Certification (CMMC) program is aligned to the US Department of Defense (DOD) information security requirements for Defense Industrial Base (DIB) partners. CMMC is designed to enforce protection of sensitive unclassified information that is shared by the Department with its contractors and subcontractors. CMMC2 Solution Brief |
| European Union Directive on Security of Network and Information Systems | NIS2 | The NIS2 Directive is a modernised framework based on the EU Network and Information Security Directive, the first piece of EU-wide legislation on cybersecurity. The Directive provides legal measures to boost the overall level of cybersecurity in the EU by focusing on preparedness and cooperation within critical sectors. European Union NIS2 Directive Solution Brief |
| ISA/IEC 62443 | 62443 | The ISA/IEC 62443 series of standards define requirements and processes for implementing and maintaining electronically secure industrial automation and control systems (IACS). These standards set best practices for security and provide a way to assess the level of security performance. ISA/IEC 62443 Solution Brief |
| IT-Sicherheitsgesetz 2.0 | IT-SiG 2 | The German Bundestag adopted the IT Security Act 2.0 (IT-Sicherheitsgesetz 2.0 – “IT-SiG 2.0”) in April 2021. In May 2021, the draft IT-SiG 2.0 was endorsed in the Bundesrat. This regulation provides amendments and updates to the original (IT-SiG 1.0), bringing a focus to the German Act to strengthen the security of federal information technology (Gesetz über das Bundesamt für Sicherheit in der Informationstechnik – BSIG.) IT-Sicherheitsgesetz 2.0 Solution Brief |
| Kingdom of Saudi Arabia National Cybersecurity AuthorityOperational Technology Cybersecurity Controls | KSA OTCC | The KSA OTCC consists of a set of cybersecurity controls and best practices that are tailored to the specific needs of the Kingdom of Saudi Arabia. It includes guidance on four primary domains: governance, defense, resilience, and third party cybersecurity. The framework is mandatory for all organizations that operate critical infrastructure in the country, including those in the energy, transportation, and healthcare sectors. OTCC-1:2022 Solution Brief |
| National Institute of Standards National Institute of Standards and Technology Cyber Security Framework | NIST CSF | The NIST CSF framework consists of five core functions: Identify, Protect, Detect, Respond, and Recover. It provides a set of guidelines and best practices that organizations can use to create, implement, and maintain their cybersecurity programs to help manage cyber risk. |
| North American Electric Reliability Corporation Critical Infrastructure Protection | NERC CIP | For electric utilities in the United States and Canada, NERC CIP reliability standards provide baseline security requirements for power systems and their interconnected facilities and equipment. NERC CIP Compliance |
| U.S. Federal Binding Operational Directive | CISA BOD | The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a Binding Operational Directive regarding asset discovery, vulnerability detection, and reporting practices for Federal Civilian Executive Branch (FCEB) agencies. The practices described in the directive, which include automated asset discovery, vulnerability detection and enumeration, and more, must be in place by April 3, 2023. CISA BOD Solution Brief |
| U.S. Transportation Security Administration Security Directive Pipeline-2021-02C | TSA SD02C | Applies to owners and operators of hazardous liquid and natural gas pipeline and liquified natural gas facilities, with the goal of reducing the risk that cybersecurity threats pose to critical pipeline systems and facilities. TSA Security Directive Pipeline Infographic |
| Cyber Assessment Framework | CAF | The CAF collection consists of four high-level objectives that are further broken down into 14 cyber security and resilience principles. It also provides guidance on their application and includes 39 Indicators of Good Practice (IGP). Unlike many generic cybersecurity practices, the CAF collection is suitable for both Information Technology (IT) and Operational Technology (OT) environments, covering various organisations that operate OT systems, ranging from power generation to pharmaceutical production. CAF Solution Brief |
The 2025 OT Cybersecurity Report is Now Available
Ready to Advance Your Cybersecurity Compliance?
Wherever you are in your cybersecurity journey we’re here to help you take the next step in auditing and adhering to industry compliance requirements.