As enterprise cybersecurity leaders improve the maturity of their Information Technology (IT) vulnerability management programs, Operational Technology (OT) environments remain challenging to manage. Many organizations are not even fully equipped with a detailed inventory of OT assets, let alone actively managing the vulnerabilities and risks existing within all of them.
According to the National Institute of Standards and Technology (NIST), a vulnerability is a weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source. Adversaries exploit vulnerabilities to gain unauthorized access to a computer system. After exploiting a vulnerability, a cyberattack can run malicious code, install malware, steal sensitive data, or halt operations and/or assume control of ICS. Many vulnerabilities impact ICS software, placing the customers using the software at a heightened risk of a data breach, or supply chain attack.
According to a recent study from SANS Institute, while more than 91% of organizations include on-premises information technology (IT) infrastructure assets in their existing or planned vulnerability program, just 23% do the same for their OT assets.
As threats increasingly target in Industrial Control Systems (ICS), the need grows by the day for effective mitigation of vulnerabilities that attackers can exploit. Organizations must come into balance with proven, documented OT vulnerability management practices to not only protect themselves from these threats but to also be compliant with an ever-increasing number of regulations1. This blog summarizes the key findings of a Dragos, Inc. white paper: Understanding the Challenges of OT Vulnerability Management and How to Tackle Them.
Beware: Public Sources Often Contain Incorrect or Inaccurate Data
Compounding these issues is the fact that that public vulnerability sources used for assessment, classification, and prioritization often contain incomplete or inaccurate data. Public vulnerabilities are known vulnerabilities that are released to the public in the form of advisories released by ICS hardware and software vendors.
After careful analysis and field validation, Dragos has found that publicly announced vulnerability severity scores are often inaccurate, incomplete and lack both context and guidance. This means that industrial teams are struggling with how to interpret and apply them in their environments and spending too much time chasing the wrong issues.
Dragos’s own ICS research has found that: 2
- 43% of vulnerability advisories contained errors making it difficult to prioritize mitigations
- 64% of advisories with no patch had no vendor mitigation advice
- 61% of advisories with a patch had no vendor mitigation advice
- 73% of vulnerabilities are deemed more severe by Dragos than their Public Advisory Common Vulnerability Scoring System (CVSS) score
- Only 6% of all advisories are deemed ‘Now’ priority, requiring immediate action to deal with a broad issue that could have a real industrial impact
Organizations that want to build out an OT vulnerability management program or improve the maturity of their existing program will need to address the shortcomings of these public sources. Simply relying on them without added context distorts the process of prioritizing vulnerabilities appropriately and makes it harder to efficiently resolve vulnerabilities at scale.
Why OT Vulnerability Management Is Different
The unique challenges of finding and remediating flaws within OT environments have held back the maturation of vulnerability management in ICS. This explains why it lags IT vulnerability management.
OT working environments are very different than IT environments, as are the potential cyber risks and the impact from them. Layered on top of that are additional protocols unique to OT including, complicated vendor relationships that impact how and when systems can be patched, and stringent regulatory and operational requirements.
When comparing vulnerability management in IT vs. OT environments the biggest risks lie in different areas. In OT for example:
- Downtime tolerance is slim to none
- Active scanning is frequently problematic
- Vendors hold a lot of control
- There are exceedingly long patch cycles
- Legacy systems are entrenched
- Unique, fit-for-purpose hardware and software prevails
- Patch installation and tracking is highly manual
Vulnerability Assessment versus Vulnerability Management
Many industrial organizations struggle to push beyond vulnerability assessment into full lifecycle vulnerability management. Vulnerability assessment without vulnerability management leaves issues unfixed and untracked. It also opens regulated industries like electrical utilities up to compliance headaches if flaws found during assessment are not addressed within the timeframes mandated by the regulators.
Dragos recently published white paper Understanding the Challenges of OT Vulnerability Management and How to Tackle Them, explains in more detail the difference between assessment and management of vulnerabilities in OT environments. It breaks the vulnerability management cycle down into four stages.
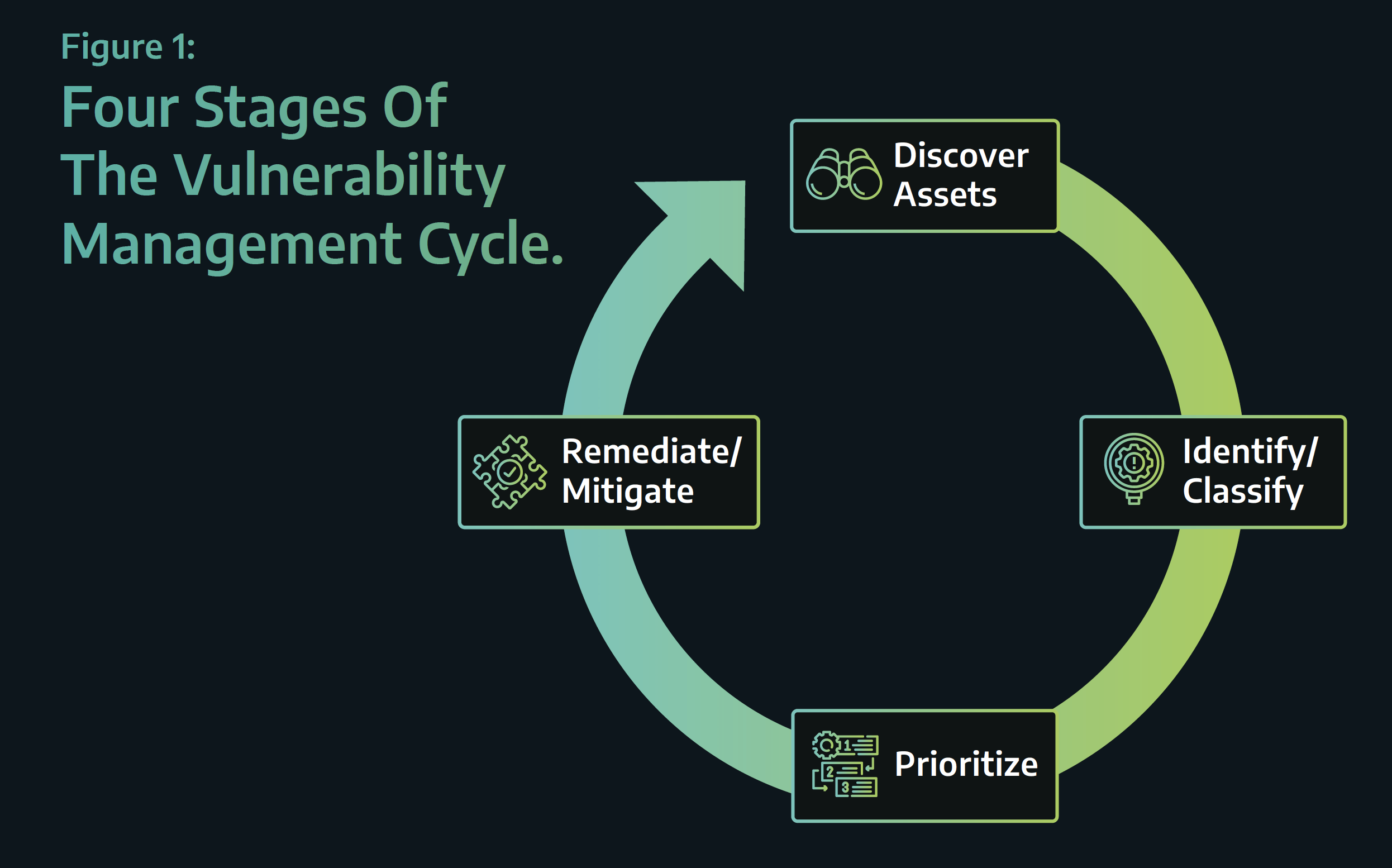
There are a lot of differences between OT vulnerability assessment and management, but the ultimate differentiators are the ability to resolve vulnerabilities and to track the resolution progress made across an inventory.
True vulnerability management requires not only cycling through the four stages, but also showing the team’s work as it does so. Because remediation and mitigation decisions are based on a complete picture of risk, in OT operational risk quite often outweighs vulnerability or security risk. This means vulnerabilities are risk accepted more frequently in OT than in IT.
Ten Ways to Get Started
Building out an OT vulnerability management process is a slow, methodical process that will take resources and wherewithal to get right. There is certainly no cookie-cutter path for an industrial organization to follow. Understanding the Challenges of OT Vulnerability Management and How to Tackle Them provides a detailed list of ten ways to get started with this process, each of the 10 points is captioned below:
- Don’t Rush In
- Everything Starts With an Asset Inventory and Visibility
- Don’t Fear Automation
- Periodic Walk Downs Are a Must
- Documentation is Crucial
- Understand OT Vulnerability Prioritization is Different
- Master The Art of Compensating Controls
- Actively Manage Vendors Relationships
- Change Management
- Hire Dedicated Staff
The Dragos OT Vulnerability Management white paper explains in much more detail the differences between OT and IT vulnerability management and provides comprehensive vulnerability management recommendations and mitigations.
Understanding the Challenges of OT Vulnerability Management and How to Tackle Them
Read the WhitepaperFootnotes:
1 https://www.sans.org/reading-room/whitepapers/analyst/vulnerability-management-survey-2020-39930
2 https://www.dragos.com/year-in-review/#section-vulnerabilities – Dragos Year In Review Data – Vulnerabilities
Ready to put your insights into action?
Take the next steps and contact our team today.