MAGNALLIUM
Since 2017
The MAGNALLIUM activity group has targeted petrochemical manufacturers and other industrial organizations since 2013. While initial media coverage treated MAGNALLIUM as a significant threat to critical infrastructure, Dragos analysis suggests that the group lacks ICS-specific capabilities and focuses exclusively on information gathering at this time.
MAGNALLIUM Threat Group Operations
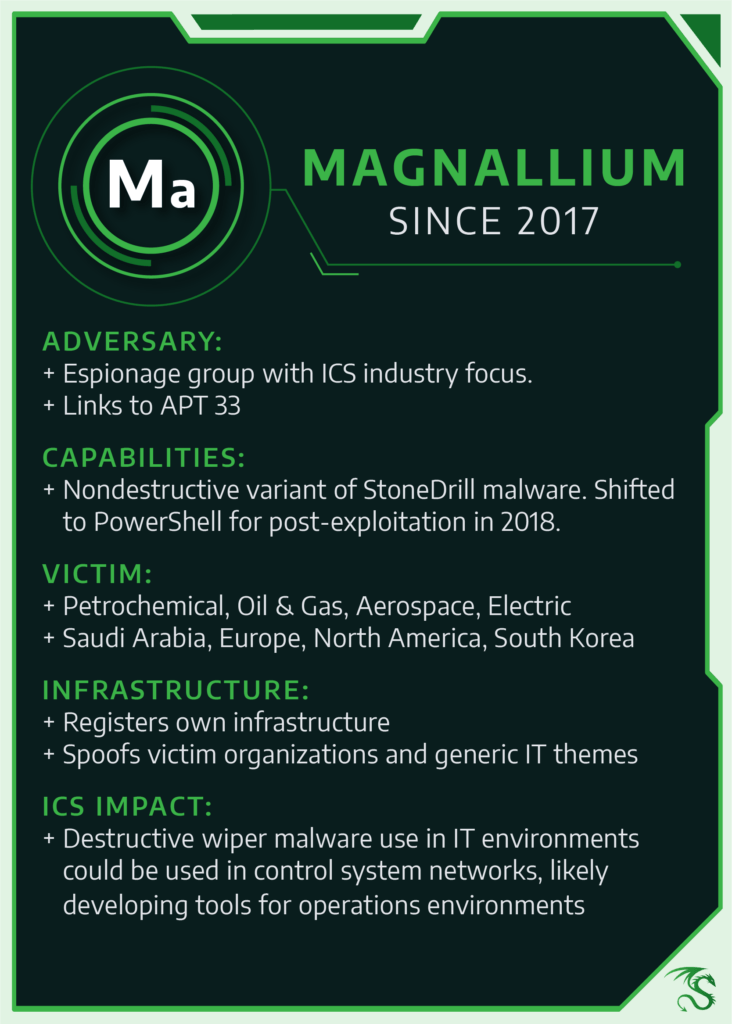
MAGNALLIUM initially had a narrow focus, including Saudi Arabian energy firms and an aircraft holding company. In 2018, MAGNALLIUM’s victimology expanded to additional targets, including entities in Europe and North America.As a result of operations against these Saudi-linked firms, MAGNALLIUM operations touched other entities in joint-ventures or similar arrangements outside the region, such as an aerospace company in the United States and petrochemical firms in South Korea.
MAGNALLIUM used phishing emails to gain access to victims’ machines. The lures were created from publicly-available job postings to produce targeted career-related spears. Publicly-available phishing kits were used to construct the emails’ contents, and the group leveraged variants of the StoneDrill wiper and TURNEDUP malware family. The group has transitioned to PowerShell based post-exploitation tools in 2018.
The group remains focused on preliminary information gathering and access operations that can be used for a future attack against ICS-related organizations. Though concerning, Dragos primarily identifies MAGNALLIUM activity focusing on the Gulf region with little indication of operations outside this area. Activity in this group overlaps with APT33 recently labeled by FireEye.
About Dragos Threat Intelligence
Dragos threat intelligence leverages the Dragos Platform, our threat operations center, and other sources to provide comprehensive insight into threats affecting industrial control security and safety worldwide. Dragos does not corroborate nor conduct political attribution to threat activity. Dragos instead focuses on threat behaviors and appropriate detection and response. Read more about Dragos’ approach to categorizing threat activity and attribution.
Dragos does not publicly describe ICS activity group technical details except in extraordinary circumstances in order to limit tradecraft proliferation. However, full details on MAGNALLIUM and other group tools, techniques, procedures, and infrastructure is available to network defenders via Dragos WorldView.